A targeted spear-phishing campaign linked to Iranian-affiliated actors has been uncovered, aimed at diplomatic missions around the world. The attackers used a compromised email account from Oman’s Ministry of Foreign Affairs to distribute malware disguised as urgent diplomatic messages.
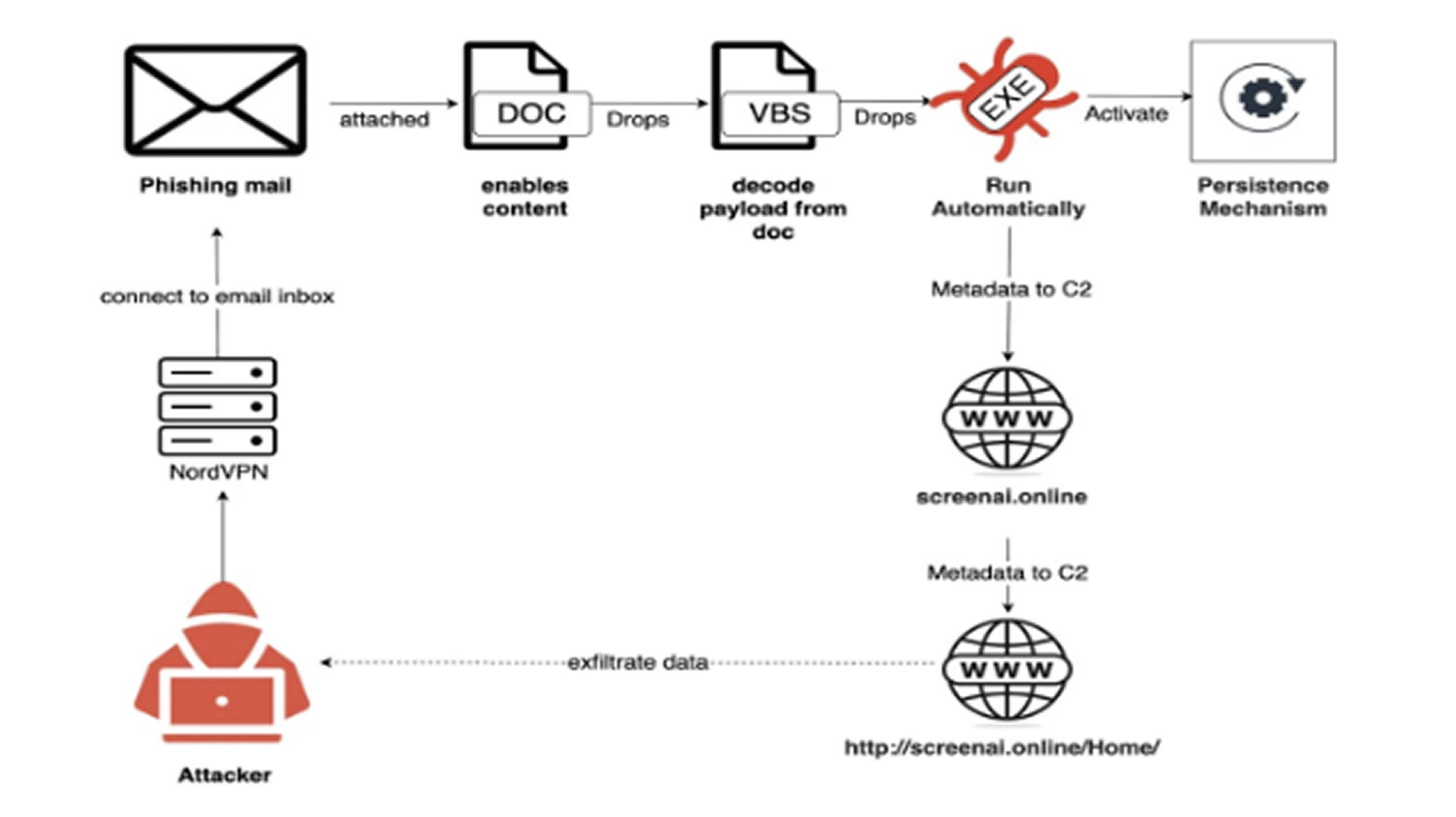
First detected in August 2025, the operation is tied to the Homeland Justice group, which is believed to be connected to Iran’s Ministry of Intelligence and Security. The attackers sent malicious Microsoft Word documents from an @fm.gov.om address, routing traffic through a NordVPN exit node in Jordan to hide their location. The emails reached 270 addresses across embassies, consulates, and international organizations, with subject lines referencing geopolitical tensions in the Middle East.
Dreamgroup analysts found the campaign was broader than initially thought, involving 104 compromised email accounts to conceal its full reach.
The attached Word files contained malware encoded through VBA macros. These macros converted numeric sequences into ASCII characters using a decoding function labeled “dddd.” The code was embedded in hidden modules named “This Document” and “UserForm1,” delivering the payload in multiple stages.
To evade detection, the malware used a delay function called “laylay,” which ran nested loops to slow down analysis tools. The payload was written to a file named ManagerProc.log in the Public Documents folder, disguised as a harmless log before being executed with hidden parameters.
Once active, the malware copied itself to ProgramData under the name sysProcUpdate.exe and altered DNS settings in the Windows registry to maintain persistence. It also collected system data such as usernames, device names, and admin privileges, sending the information through encrypted HTTPS POST requests to a command-and-control server hosted at screenai.online/Home/.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



