Cyble threat intelligence researchers have discovered a sophisticated new Linux botnet named Luno. The malware is built for cryptocurrency mining, remote command execution, and a wide variety of DDoS attacks.
According to researchers, Luno is a professionally developed tool, with advanced features that set it apart from typical botnets. It can masquerade as a legitimate process, replace system binaries, and even update itself, which suggests it is designed as a long-term criminal tool.
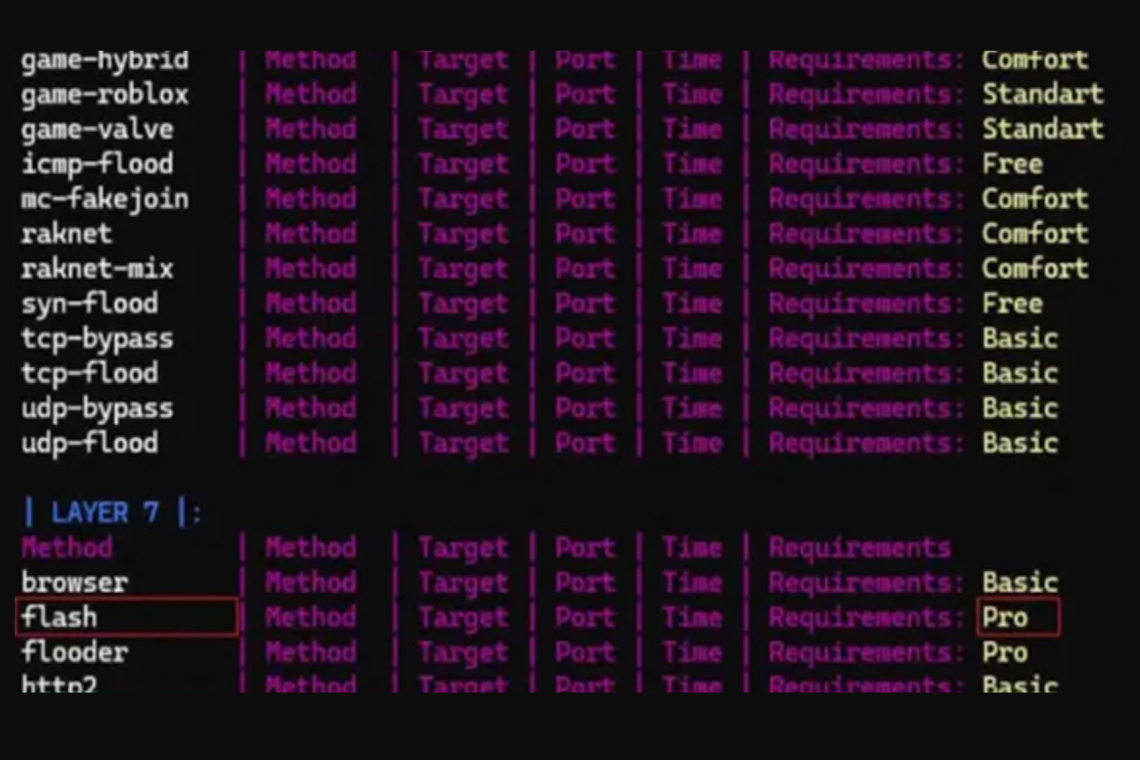
The hackers behind the malware are actively selling DDoS services on a Telegram channel, with a pricing model that points to a long-term business plan. The botnet can be rented to launch DDoS attacks on a wide range of targets, including specific game servers for platforms like Roblox, Minecraft, and Valve.
Luno is equipped with over 20 different DDoS attack modules. The malware can execute advanced attacks that randomize packet sizes and destinations to evade detection. It can even mimic human browsing traffic with a hardcoded list of user agents and a long list of legitimate referrers to bypass basic defenses. The malware can also target gaming servers by using the RakNet protocol, which allows it to bypass simple firewall rules and make its malicious traffic appear legitimate.
The botnet is designed to avoid being detected by security tools. It can check for debuggers, look for network anomalies, and will even self-delete if it senses that it is being analyzed. Cyble researchers warn that due to its resilience, modular design, and ability to steal resources and disrupt services, Luno should be treated as a long-term threat to Linux environments, particularly internet-facing servers and game-hosting platforms.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.