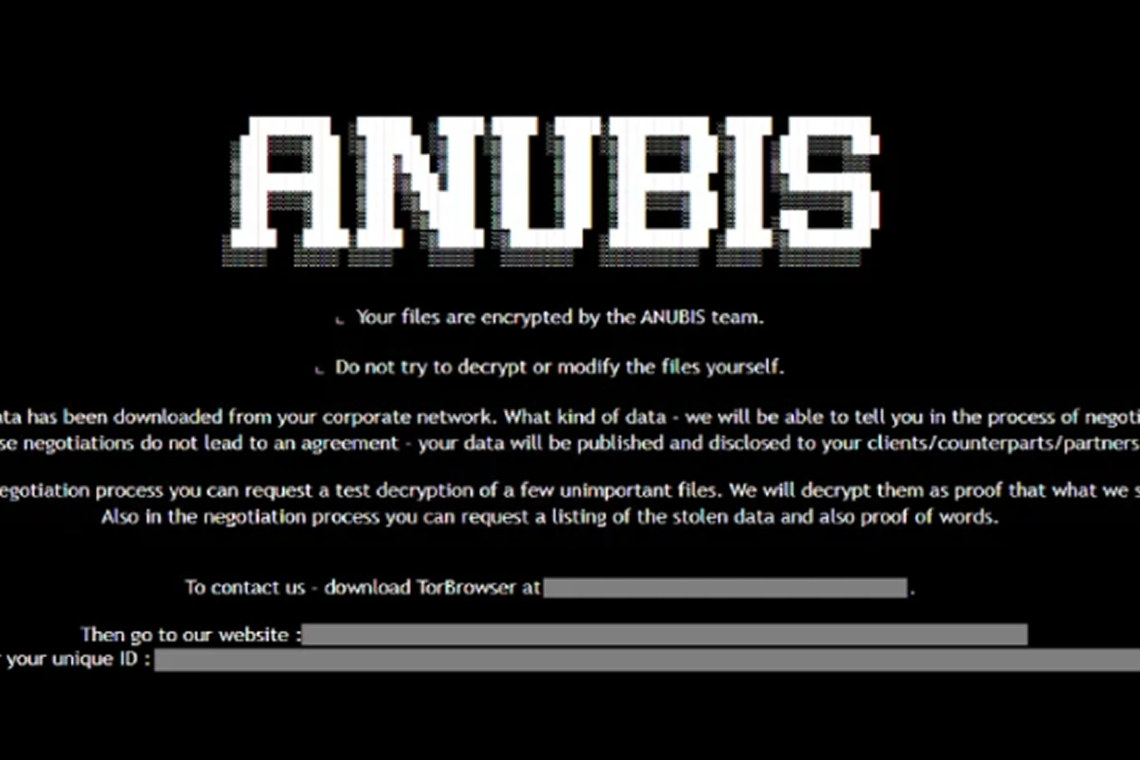
A new ransomware strain has emerged, combining the ability to encrypt files with the capability to permanently erase them. This development has been described as a "rare dual-threat."
According to a report published last week by Trend Micro researchers Maristel Policarpio, Sarah Pearl Camiling, and Sophia Nilette Robles, the ransomware includes a "wipe mode" that permanently deletes files, making recovery impossible even if the ransom is paid.
The ransomware-as-a-service (RaaS) operation is known as Anubis. It became active in December 2024 and has targeted victims in the healthcare, hospitality, and construction sectors across Australia, Canada, Peru, and the United States. Analysis of early test samples indicates that the ransomware was initially called Sphinx before the developers changed the name to Anubis in the final release.
It is important to note that this RaaS operation has no connection to either the Android banking trojan or the Python-based backdoor also named Anubis. The latter is linked to the financially motivated FIN7 group, also known as GrayAlpha.
Trend Micro reports that Anubis operates a flexible affiliate program with negotiable revenue sharing. It also supports additional profit channels such as data extortion and the sale of access to compromised systems.
The affiliate program offers an 80-20 revenue split, giving 80 percent of the ransom payment to affiliates. Data extortion and access monetization schemes provide 60-40 and 50-50 splits, respectively.
Anubis attacks typically start with phishing emails as the initial method of gaining access. Once inside, the attackers escalate privileges, perform reconnaissance, and delete volume shadow copies before encrypting files. In some cases, they also use the wipe mode to erase file contents.
This wipe function reduces file sizes to 0 KB while leaving file names and extensions unchanged. This approach makes data recovery impossible and increases pressure on victims to pay the ransom.
"The ransomware includes a wiper feature using the /WIPEMODE parameter, which can permanently delete file contents and block any recovery efforts," the researchers explained.
The ability to both encrypt and irreversibly destroy data makes Anubis especially dangerous, as it greatly increases the pressure on victims to comply with ransom demands.
Meanwhile, Recorded Future has reported on new infrastructure tied to the FIN7 group, used to impersonate legitimate software and deliver the NetSupport RAT. The cybersecurity firm, which is owned by Mastercard, identified three unique delivery methods over the past year. These include fake browser update pages, fraudulent 7-Zip download sites, and infrastructure known as TAG-124, which also goes by names like 404 TDS, Chaya_002, Kongtuke, and LandUpdate808.
The fake browser update technique uses a custom loader called MaskBat to run the remote access trojan. The other two delivery methods rely on a PowerShell-based loader named PowerNet, which decompresses and executes the malware.
Recorded Future's Insikt Group noted that MaskBat shares similarities with FakeBat but includes obfuscation and string indicators tied to GrayAlpha. Although all three delivery methods were seen in use at the same time, only the fake 7-Zip sites remained active at the time of reporting, with new domains still appearing as of April 2025.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.