CatB Ransomware: A Sophisticated Cyber Threat Exploiting Microsoft DTC for Stealthy Attacks
Emerging in late 2022, CatB ransomware also known as CatB99 or Baxtoy has quickly made headlines as a highly advanced threat actor in the cybersecurity space. Its standout features include powerful evasion tactics and a unique execution strategy, notably exploiting Microsoft’s Distributed Transaction Coordinator (MSDTC) through DLL hijacking to stealthily deploy its malicious payload.
Security analysts have drawn strong parallels between CatB and the older Pandora ransomware, hinting that CatB could be a strategic rebrand. Identical ransom notes and similar behavior support this theory. However, CatB goes further—encrypting files and stealing browser data and credentials, amplifying its destructive potential.
What makes CatB even more dangerous is its ability to detect virtual environments, effectively dodging analysis and delaying response. AttackIQ researchers have linked CatB to ChamelGang (a.k.a. CamoFei), a known cyber espionage group. This suggests a hybrid threat model, merging ransomware attacks with espionage where data theft is masked by encryption chaos.
High-profile targets across the globe have been affected. CatB’s attack chain begins with reconnaissance, gathering system and hardware details before unleashing its encryption routines. SentinelOne and Fortinet have both confirmed the malware’s advanced ability to disable defenses and maintain persistence in compromised networks.
To combat this threat, AttackIQ released a simulation tool (attack graph) that mimics CatB’s tactics, helping security teams assess and strengthen their defenses against similar real-world threats.
How the Attack Works: DLL Hijacking via MSDTC
CatB’s execution hinges on DLL search order hijacking, a method classified under MITRE ATT&CK (T1574.001). It abuses Windows’ predictable DLL loading sequence by placing a malicious DLL in a path searched earlier than the system default. When MSDTC launches, it unknowingly loads CatB’s rogue DLL, granting the ransomware system-level execution.
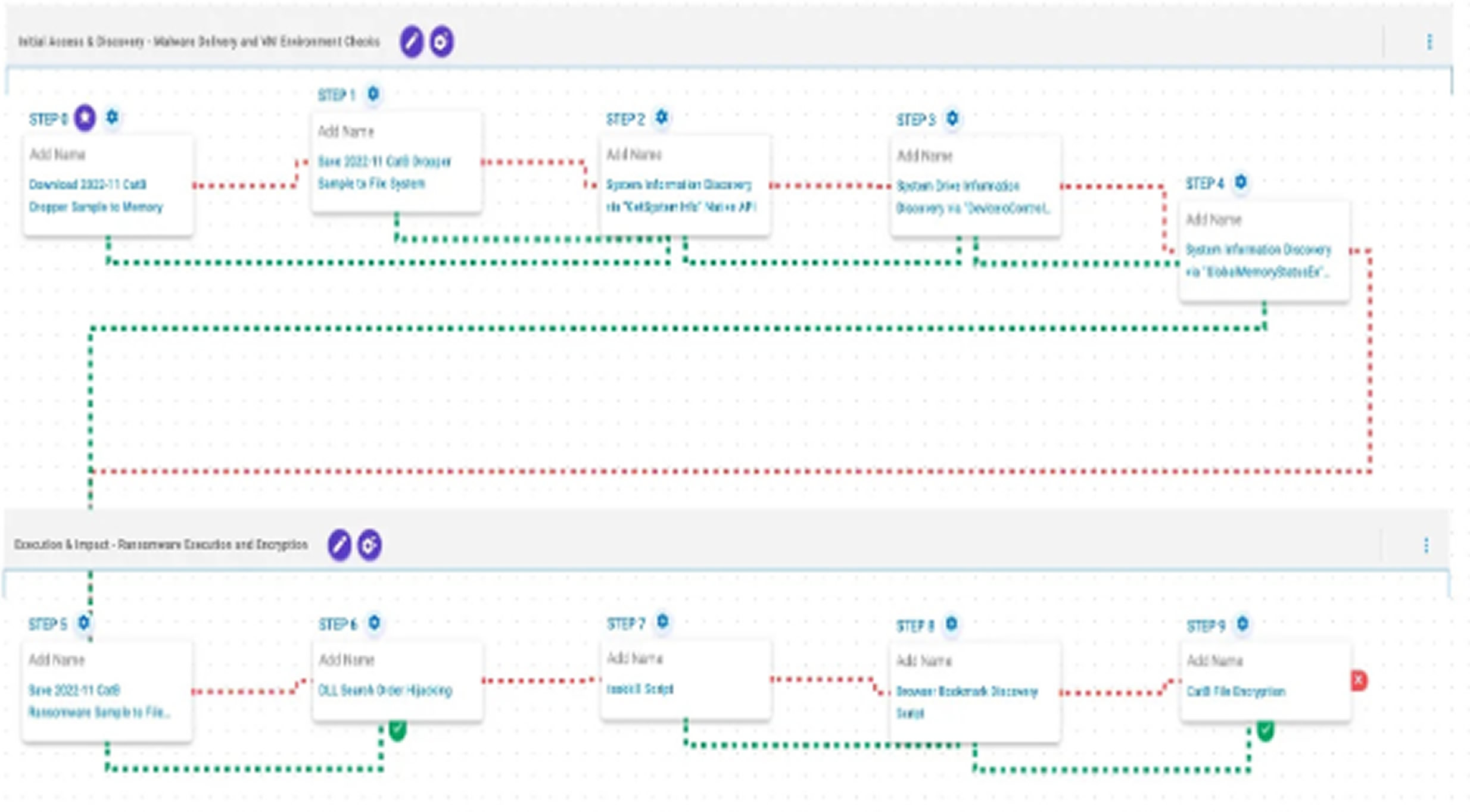
Before this, CatB’s dropper gathers system and memory data using API calls like GetSystemInfo and GlobalMemoryStatusEx, detecting whether it’s running in a virtual environment. Once in, it executes PowerShell commands to terminate security tools, clearing the path for file encryption and data exfiltration.
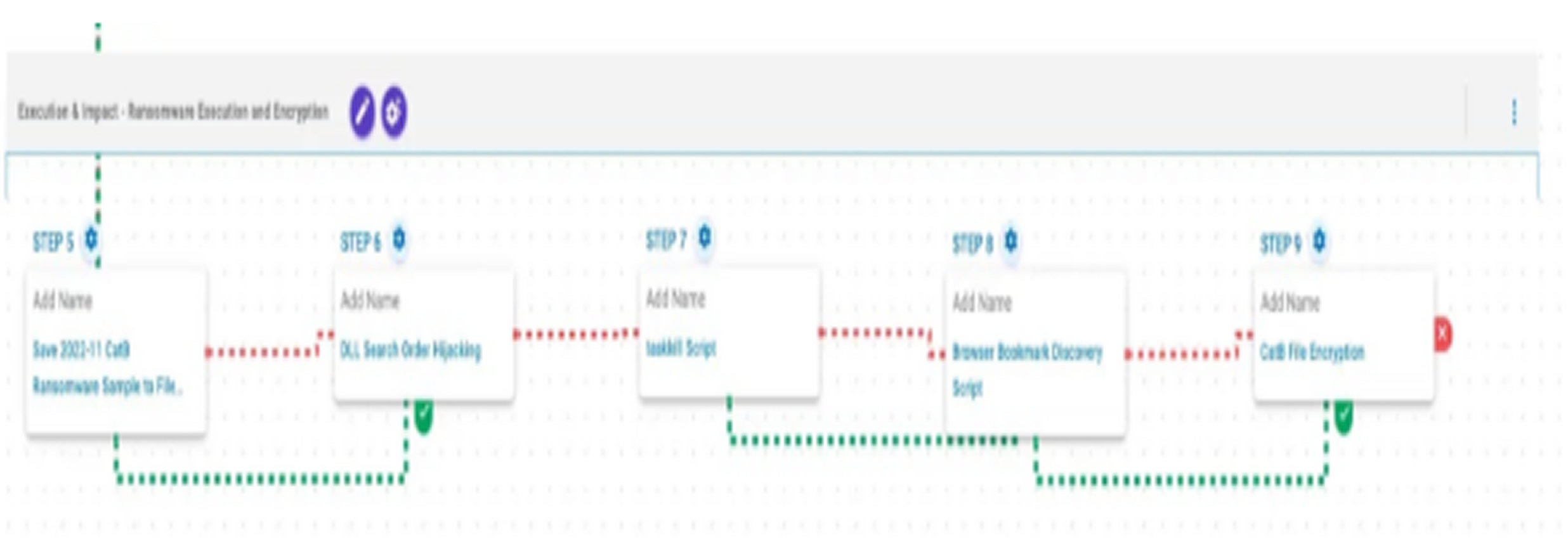
CatB’s blend of stealth, persistence, and destructive capability makes it a critical threat—demanding proactive threat modeling and advanced detection techniques from defenders worldwide.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


