Security Experts Discover Sophisticated Malware Campaign Targeting Android Users via Fake Chrome Install Pages
from unsuspecting users.
The attack cleverly hides malicious links within seemingly legitimate Amazon gift card emails, creating an effective social engineering trap that combines financial rewards and corporate trust.
The scam begins with an email claiming to offer a $200 Amazon e-gift card as a reward for outstanding performance, supposedly from the victim's employer. The professionally designed email, complete with Amazon branding and emotionally persuasive language, creates a sense of gratitude that encourages the recipient to click on the link without suspicion.
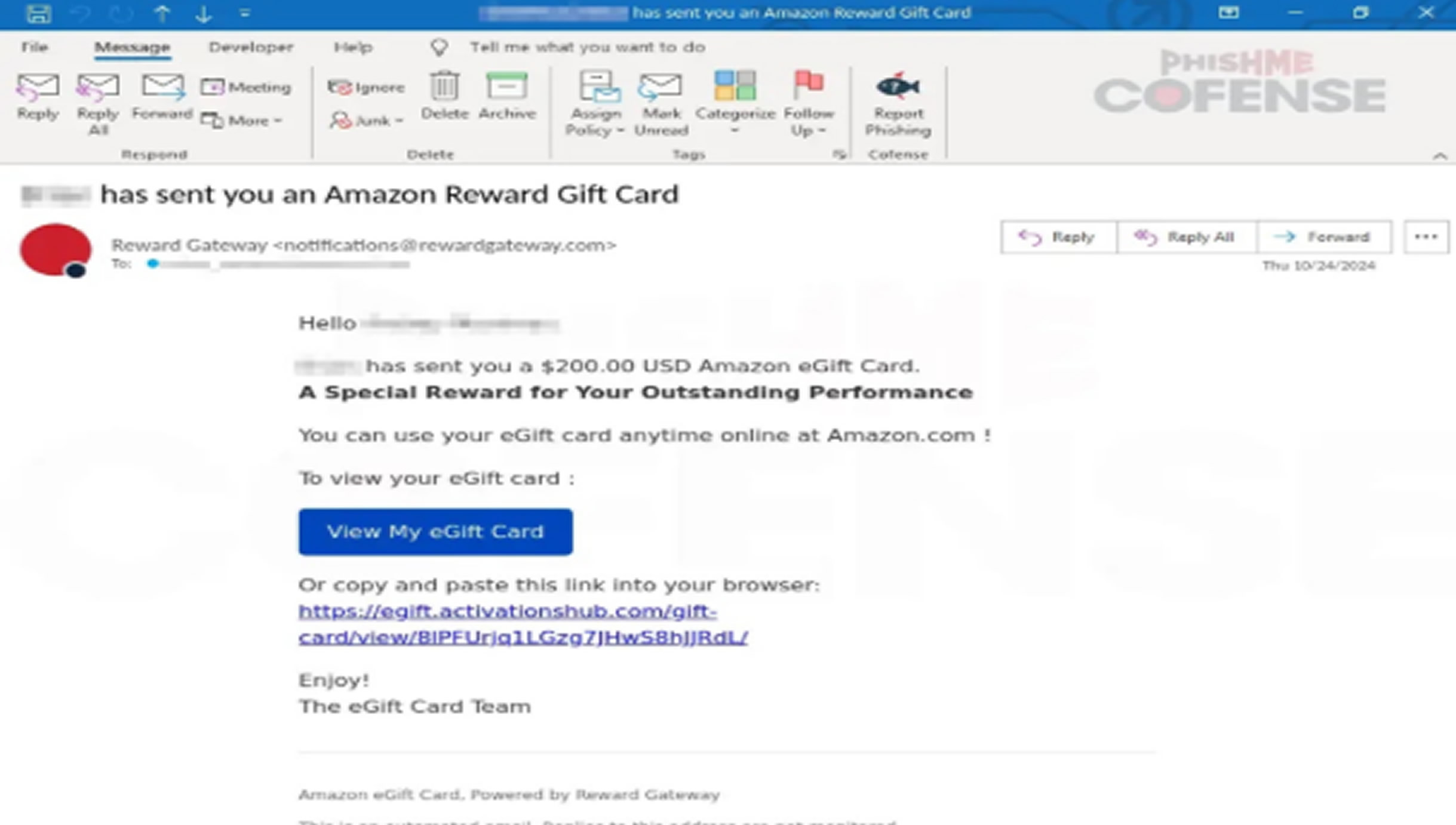
Discovered by Cofense researchers in early April 2025, this campaign has proven particularly effective in corporate environments, where employees often receive recognition through digital rewards. The phishing emails successfully bypass traditional email security systems by imitating legitimate reward notifications.
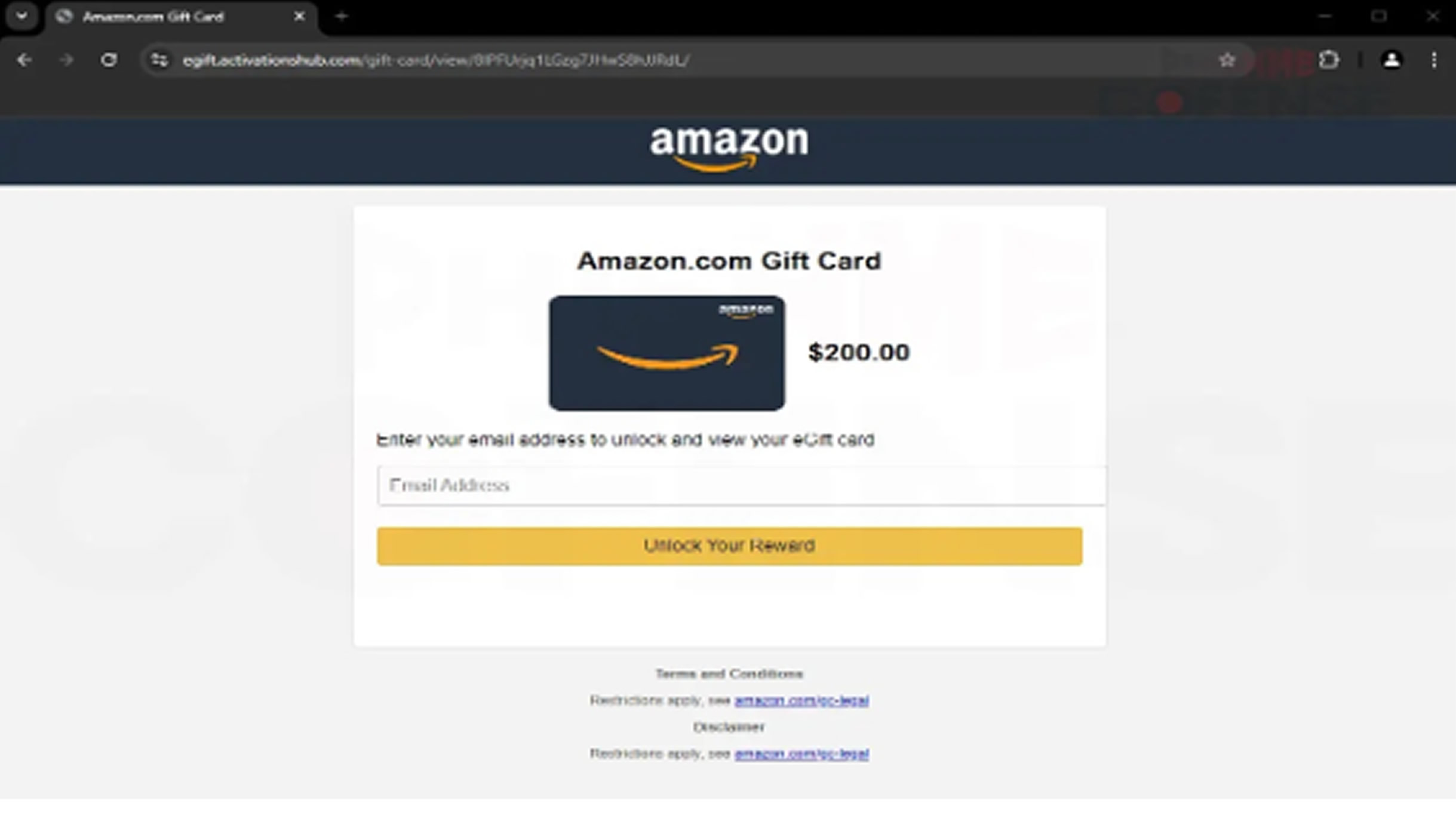
The attack is technically sophisticated, following a multi-stage process. After clicking on the “View My eGift Card” button or copying the provided link, victims are directed to a convincing, yet fraudulent, landing page designed to look like Amazon’s gift card redemption interface. The domain “egift.activationshub.com,” which was registered just days before the campaign began, serves as a red flag for malicious activity.
Infection mechanism
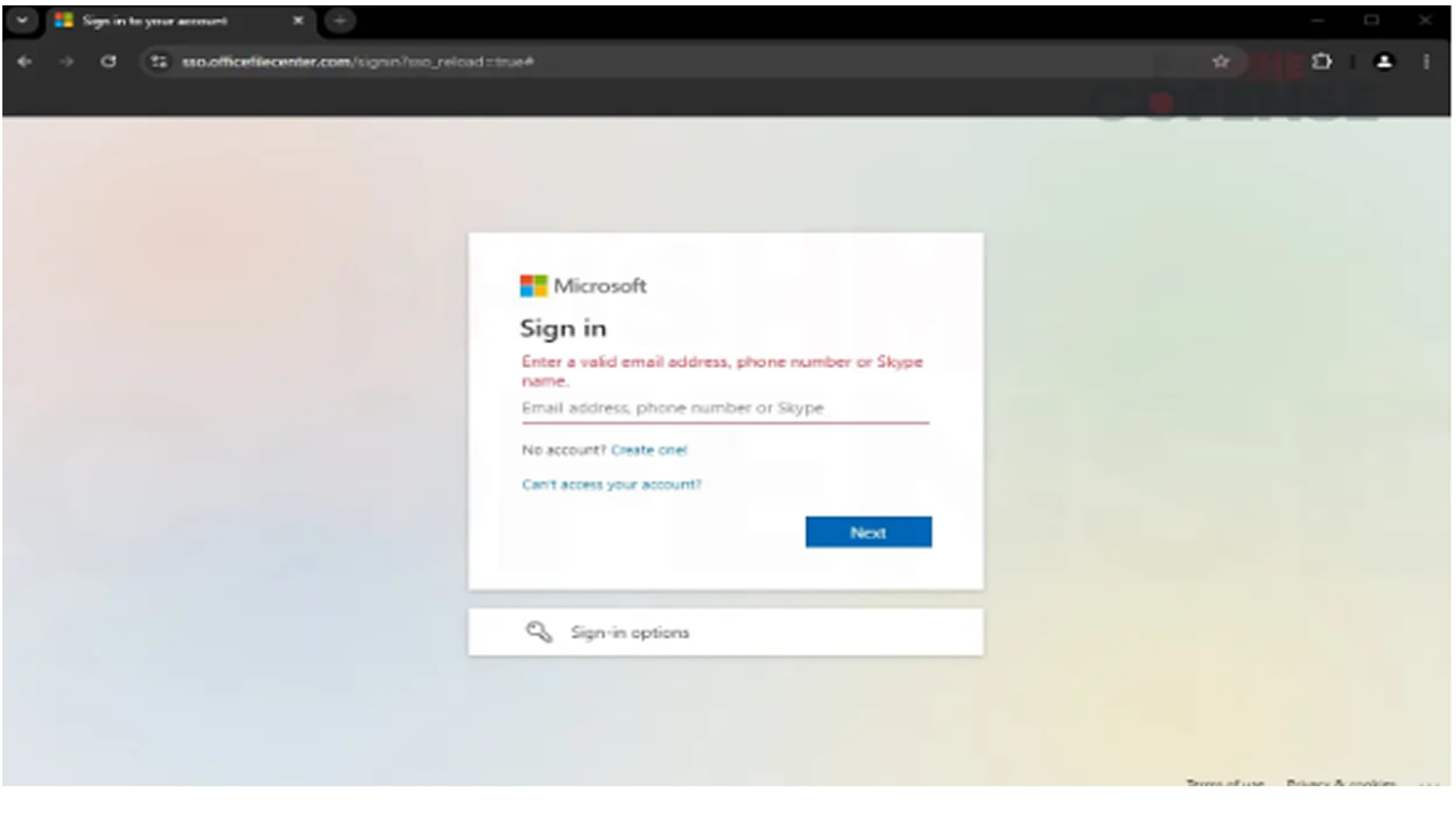
The infection mechanism is a textbook example of credential harvesting. Upon entering their email to "unlock" the gift card, victims are redirected to a fake Microsoft login page at “sso.officefilecenter.com.”
This page is a near-perfect replica of Microsoft’s authentication portal, with precise styling, logos, and input validation—only the suspicious domain name gives it away.
The attackers collect login credentials in real time and often use them immediately to access sensitive corporate data before victims realize they’ve been compromised.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


