China-Linked UNC5174 Targets Linux Systems Using SNOWLIGHT Malware and VShell Tool
A China-affiliated threat group known as UNC5174 has been linked to a new cyber campaign targeting Linux systems. The group is deploying a modified version of the SNOWLIGHT malware alongside a newly observed open-source tool called VShell.
According to a report by Sysdig researcher Alessandra Rizzo, shared with The Hacker News, attackers are increasingly adopting open-source tools for both cost-effectiveness and stealth. By using tools that are common among low-skill attackers (e.g., script kiddies), threat actors like UNC5174 can make attribution significantly harder.
“This trend is especially evident in the case of UNC5174, a group with suspected ties to the Chinese government that has operated quietly for the past year,” Rizzo noted.
UNC5174’s Attack Arsenal
UNC5174, also referred to as Uteus or Uetus, was previously documented by Mandiant (a Google company) for exploiting vulnerabilities in ConnectWise ScreenConnect and F5 BIG-IP systems. These attacks delivered a C-based ELF downloader known as SNOWLIGHT, which fetched a Golang tunneler called GOHEAVY from servers tied to the SUPERSHELL command-and-control (C2) framework.
Another tool used by the group is GOREVERSE—a publicly available reverse shell written in Golang that operates over SSH.
The French cybersecurity agency ANSSI reported similar tactics in its 2024 Cyber Threat Overview, noting that UNC5174-like techniques were used to exploit vulnerabilities in Ivanti Cloud Service Appliance (CSA), including CVE-2024-8963, CVE-2024-9380, and CVE-2024-8190.
“This group demonstrates moderate sophistication and discretion, using widely available open-source tools and even rootkit code that has already been publicly reported,” said ANSSI.
MacOS Also in the Crosshairs
Both SNOWLIGHT and VShell are reportedly capable of targeting Apple macOS devices. VShell has been spotted disguised as a fake Cloudflare authenticator app, according to malware samples uploaded to VirusTotal from China in October 2024.
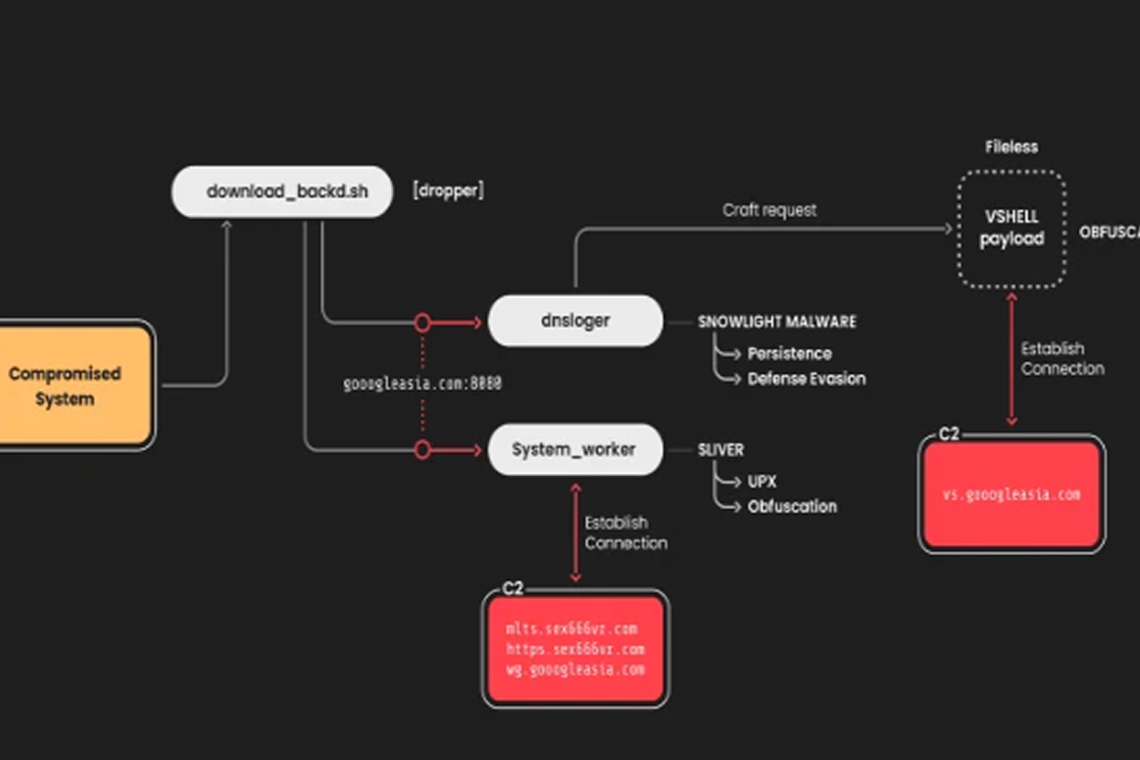
In a campaign observed by Sysdig in January 2025, SNOWLIGHT functioned as a dropper, delivering a fileless, memory-resident payload—VShell, a Remote Access Trojan (RAT) frequently used by Chinese-speaking cybercriminals. The method used for initial access remains unclear.
Once in, attackers execute a malicious Bash script (download_backd.sh) that installs two binaries: dnsloger (linked to SNOWLIGHT) and system_worker (associated with the Sliver C2 framework). These files help establish persistence and communication with the attacker-controlled server.
The final payload, VShell, is deployed through a specially crafted request to the C2 server, giving the attackers full remote control capabilities.
Advanced Stealth and Command Techniques
“VShell acts as a full-featured RAT, allowing attackers to execute commands and transfer files at will,” said Rizzo. Sysdig also emphasized the advanced nature of the campaign, highlighting the use of WebSockets for C2 and the fileless nature of the VShell payload as key indicators of its stealth.
In a related disclosure, cybersecurity firm TeamT5 revealed that another Chinese threat group exploited vulnerabilities in Ivanti appliances (CVE-2025-0282 and CVE-2025-22457) to deliver a separate malware strain named SPAWNCHIMERA. The attacks reportedly impacted organizations across nearly 20 countries, including the U.S., U.K., France, Japan, South Korea, Australia, and the UAE.
Rising Tensions and Accusations
These cyber activities have surfaced amid growing geopolitical tension. China recently accused the U.S. National Security Agency (NSA) of launching cyberattacks during the Asian Winter Games in February. Chinese officials claim the NSA targeted critical infrastructure and Huawei systems.
“At the ninth Asian Winter Games, the U.S. government carried out cyberattacks on both the event’s information systems and essential infrastructure in Heilongjiang,” said Foreign Ministry Spokesperson Lin Jian. “This act seriously threatens China’s national defense, financial systems, social stability, and the privacy of its citizens.”
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.