A prominent telecommunications company in Asia has reportedly been infiltrated
by Chinese state-sponsored hackers, who remained undetected within its systems for over four years, according to a recent report by incident response firm Sygnia.
Sygnia has been tracking the cybercriminal group under the alias "Weaver Ant," describing them as highly persistent and adept at evading detection. However, the report did not disclose the name of the affected telecom provider.
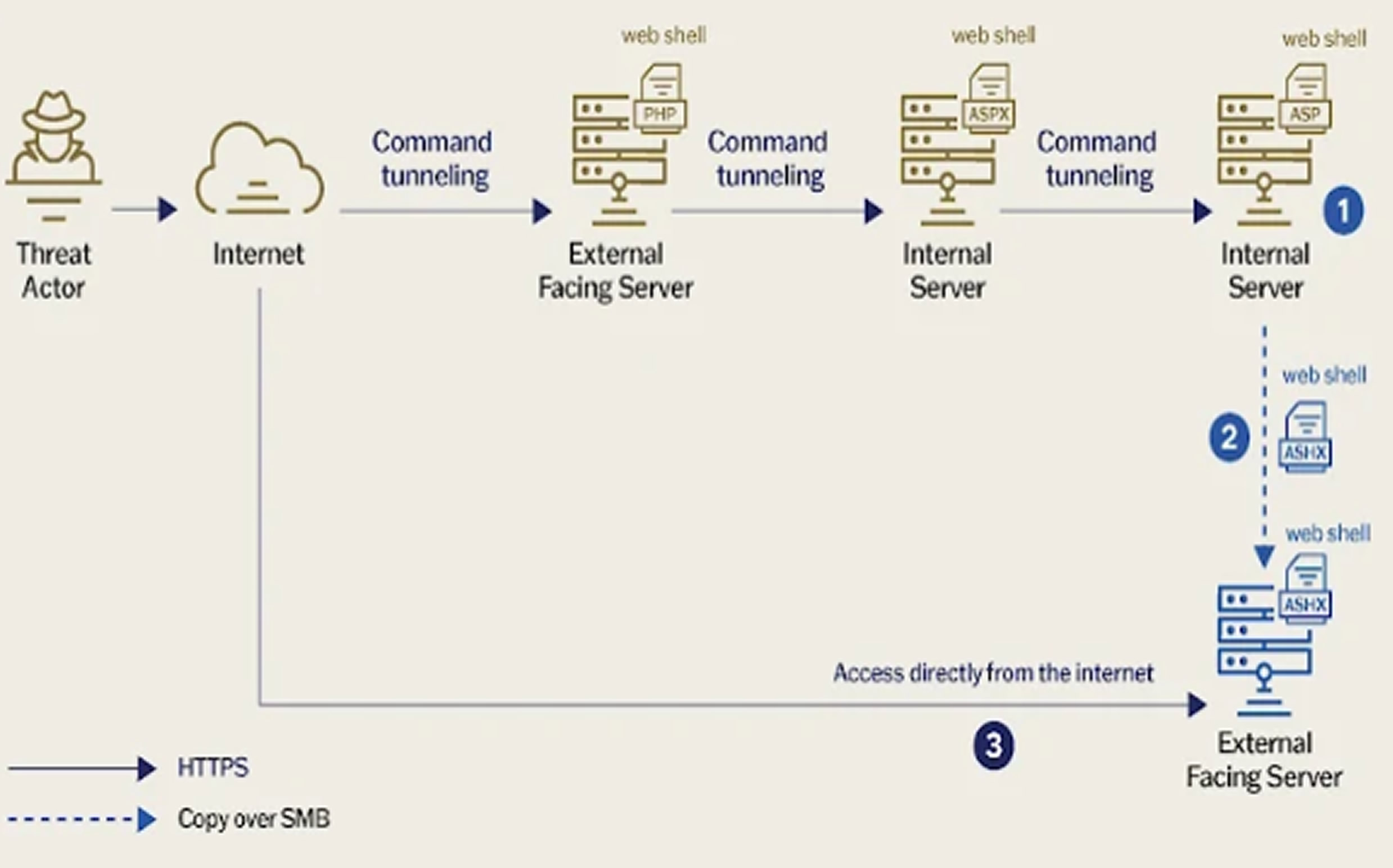
The hackers maintained their presence within the system using web shells and tunneling techniques, enabling them to conduct cyber espionage operations. Sygnia stated that the attackers' primary objective was to gain and sustain long-term access to telecommunications networks to extract sensitive information.
The attack reportedly began with the exploitation of a public-facing application, which allowed the deployment of two distinct web shells—an encrypted variant of China Chopper and a newly discovered malicious tool named INMemory. China Chopper has been previously utilized by various Chinese hacking groups, while INMemory operates by decoding a Base64-encoded string and executing it entirely in memory. This method ensures that no forensic evidence is left on disk, making detection significantly more challenging.
According to Sygnia, the INMemory web shell executed C# code contained within a portable executable (PE) file named "eval.dll." This process ultimately ran a payload delivered via an HTTP request, further strengthening the attackers’ access to the system.
The deployed web shells served as entry points for more advanced payloads, the most notable being a recursive HTTP tunneling tool. This tool enabled lateral movement across the network using the SMB protocol, a tactic previously associated with other cybercriminal groups like Elephant Beetle.
Furthermore, encrypted traffic transmitted through the web shell tunnel allowed the attackers to carry out a series of post-exploitation activities, including:
- Modifying Event Tracing for Windows (ETW) and the Antimalware Scan Interface (AMSI) to evade detection.
- Utilizing System.Management.Automation.dll to run PowerShell commands without launching PowerShell.exe.
- Executing reconnaissance commands on the compromised Active Directory environment to locate high-privilege accounts and critical servers.
Sygnia emphasized that Weaver Ant demonstrates characteristics commonly linked to Chinese state-sponsored cyber espionage groups. This attribution is based on several indicators, including the use of China Chopper, reliance on an Operational Relay Box (ORB) network utilizing Zyxel routers to obfuscate their infrastructure, the hackers’ working hours, and their deployment of an Outlook-based backdoor previously associated with Emissary Panda.
Throughout the prolonged breach, Weaver Ant continuously adapted its tactics, techniques, and procedures (TTPs) to blend into the evolving network environment. The attackers also employed innovative strategies to re-establish access and maintain their foothold. Sygnia noted that Chinese-nexus cyber intrusion groups typically share tools, infrastructure, and, in some cases, manpower, including the use of shared contractors.
China Accuses Taiwanese Hackers of Espionage
The revelation of this breach comes just days after China’s Ministry of State Security (MSS) accused four individuals allegedly linked to Taiwan’s military of engaging in cyberattacks against the Chinese mainland. Taiwan has denied these allegations.
According to the MSS, the accused individuals are part of Taiwan’s Information, Communications, and Electronic Force Command (ICEFCOM). The agency has been accused of launching phishing attacks, sending propaganda emails to government and military institutions, and running disinformation campaigns using fake social media profiles.
The MSS further claimed that the cyber intrusions involved the widespread use of open-source hacking tools such as the AntSword web shell, IceScorpion, Metasploit, and Quasar RAT.
Additionally, the MSS alleged that ICEFCOM has hired external hackers and cybersecurity firms to support its cyber warfare operations, as directed by Taiwan’s Democratic Progressive Party (DPP) authorities. The reported objectives of these operations include espionage, sabotage, and propaganda.
In alignment with the MSS's statement, Chinese cybersecurity firms QiAnXin and Antiy have revealed details of spear-phishing campaigns orchestrated by a Taiwanese hacker group known as APT-Q-20 (also referred to as APT-C-01, GreenSpot, Poison Cloud Vine, and White Dolphin). These attacks reportedly deliver a C++ trojan and deploy command-and-control (C2) frameworks such as Cobalt Strike and Sliver.
Furthermore, QiAnXin reported that the threat actors leveraged other entry methods, including exploiting N-day security vulnerabilities and using weak passwords on Internet of Things (IoT) devices like routers, cameras, and firewalls. The firm characterized these tactics as "not particularly sophisticated.
Found this article interesting? Follow us on X(Twitter) and Instagram to read more exclusive content we post.


