DarkCloud: A Sophisticated Stealer Malware Targeting Windows Users
DarkCloud, an advanced stealer malware that first emerged in 2022, has quickly become one of the most prevalent cyber threats in its category. Designed to target Windows systems, it has evolved significantly, enabling attackers to extract browser data, FTP credentials, keystrokes, screenshots, and financial information from infected devices.
Distribution Methods
DarkCloud primarily spreads through phishing campaigns, where attackers impersonate legitimate companies or disguise malicious payloads as payment receipts or fines. These campaigns often target HR departments, increasing the chances of compromise.
Other distribution tactics include:
- Malvertising (injecting malware into online ads)
- Watering hole attacks (compromising websites frequently visited by targets)
- Bundling with other malware like DbatLoader or ClipBanker
Evasion and Infection Mechanism
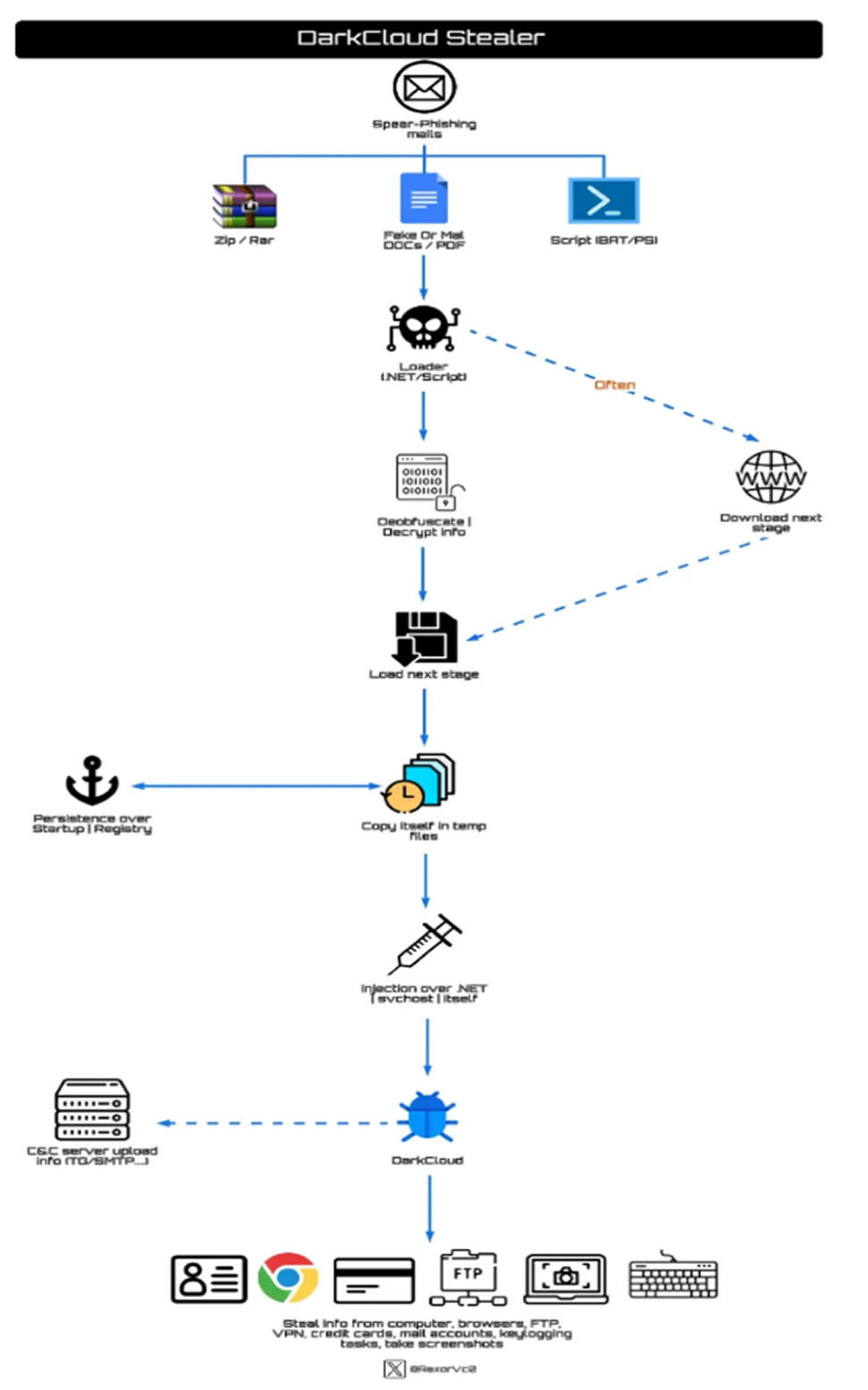
Security researcher REXorVc0 has highlighted DarkCloud’s multi-stage infection process, which is designed to bypass detection. Once a victim clicks a malicious link or downloads an infected file, the malware executes a stealthy injection process, embedding itself into Windows processes like svchost.exe or MSBuild.
By operating in legitimate system processes, DarkCloud avoids security detection while stealing passwords, browser data, and cryptocurrency wallets. The stolen data is then exfiltrated through Telegram bots, enabling attackers to access and misuse sensitive information.
Impact and Security Concerns
DarkCloud has already compromised numerous organizations, leading to significant data theft. With attackers leveraging Telegram channels to distribute and manage stolen data, the malware remains a persistent threat to businesses and individuals alike.
To protect against DarkCloud, organizations should:
- Strengthen phishing defenses with email security solutions
- Limit user privileges to prevent unauthorized software execution
- Deploy endpoint security tools capable of detecting advanced threats
- Regularly update and patch systems to minimize security vulnerabilities
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


