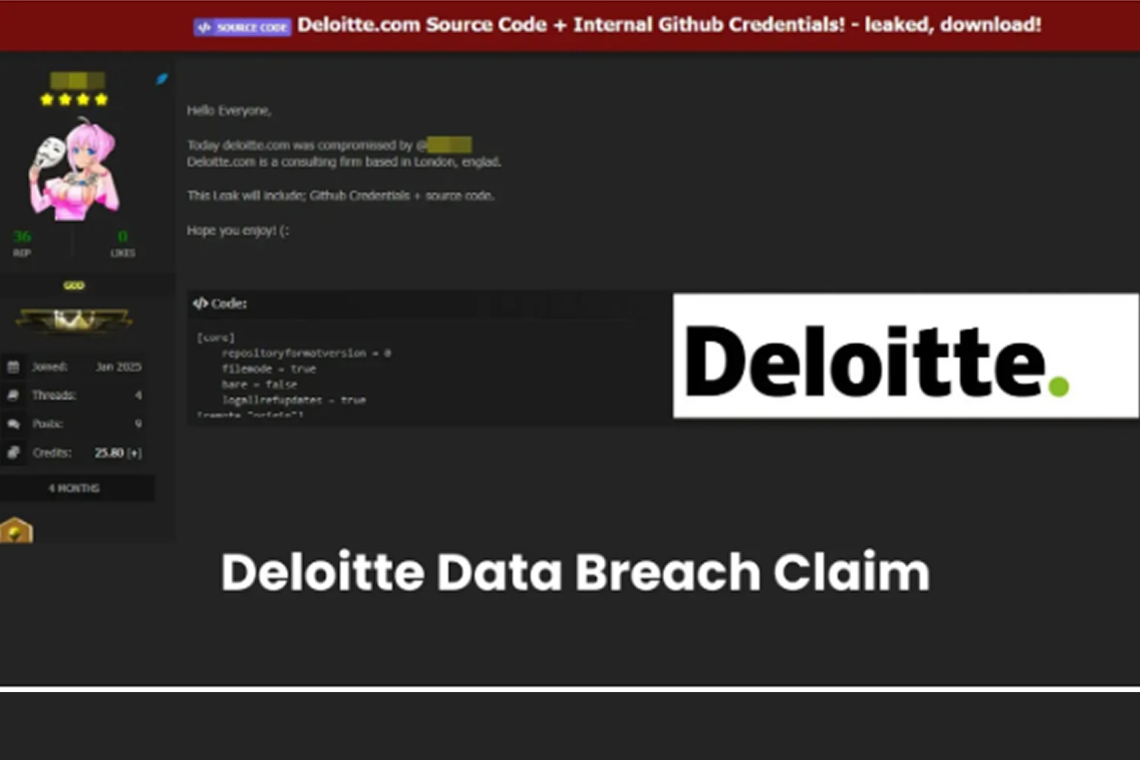
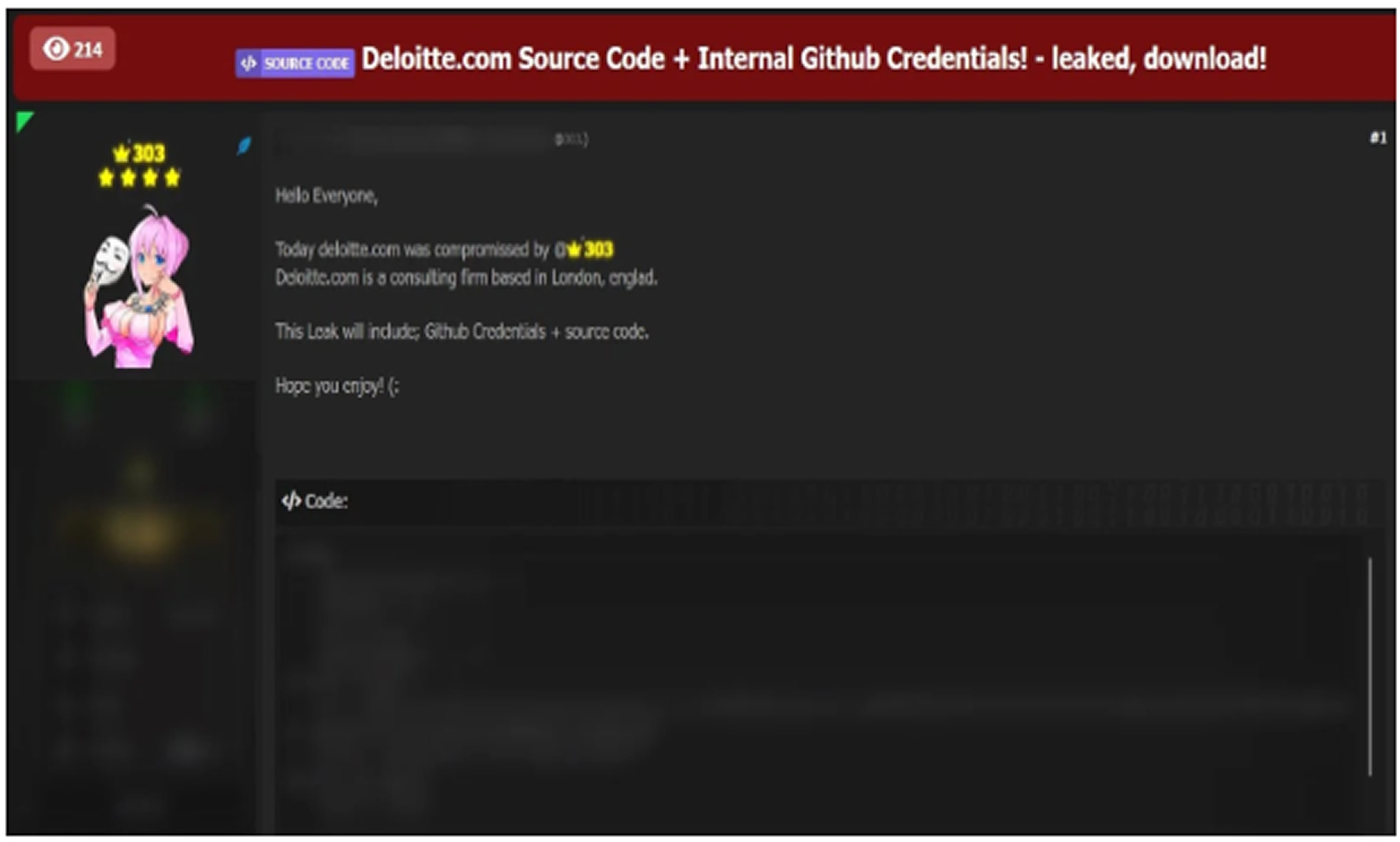
A threat actor known as “303” has reportedly claimed responsibility for breaching Deloitte’s systems and leaking sensitive internal data on a dark web forum. The alleged breach
involves GitHub credentials and source code from internal project repositories within Deloitte’s U.S. consulting division. Cybersecurity monitoring services indicate that the threat actor shared details of the compromise, including access to critical development resources. The leaked information is said to include GitHub credentials that could allow unauthorized access to Deloitte’s internal development infrastructure along with proprietary source code.
This incident adds to Deloitte’s recent cybersecurity challenges. The firm has faced several breach claims in recent months, including accusations from the Brain Cipher ransomware group in December 2024, which Deloitte denied. The company stated the compromised data was limited to a single client’s system outside Deloitte’s network and asserted no Deloitte systems were impacted. Deloitte’s credential leaks have a history dating back to 2017, when corporate VPN credentials and operational details were exposed in a public GitHub repository.
The threat actor “303” is connected to other cybersecurity incidents, such as a December 2024 breach of an Indian software company that affected major insurance firms. This pattern suggests the actor is part of a larger campaign targeting corporations and government organizations. Deloitte has not yet provided an official response to recent allegations as investigations continue.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.