A threat group suspected to have links to India has been caught targeting a European foreign affairs ministry with malware designed to extract sensitive data from infected systems.
The campaign has been attributed by Trellix Advanced Research Center to a known advanced persistent threat (APT) group called DoNot Team, also referred to as APT-C-35, Mint Tempest, Origami Elephant, SECTOR02, and Viceroy Tiger. This group has reportedly been active since 2016.
According to Trellix researchers Aniket Choukde, Aparna Aripirala, Alisha Kadam, Akhil Reddy, Pham Duy Phuc, and Alex Lanstein, DoNot APT is known for developing custom Windows malware, including backdoors like YTY and GEdit. These tools are often delivered through spear-phishing emails or malicious documents. Their targets typically include government agencies, foreign ministries, defense organizations, and NGOs, particularly in South Asia and Europe.
The attack begins with phishing emails that lure victims into clicking a Google Drive link. This triggers the download of a RAR archive that delivers a malware strain called LoptikMod, which has been in use by the group since at least 2018.
Trellix reports that these emails are sent from a Gmail address and impersonate defense officials. The subject line references an Italian Defense Attaché's visit to Dhaka, Bangladesh.
The email uses HTML formatting and UTF-8 encoding to display special characters accurately, such as the accented 'é' in 'Attaché', a detail likely meant to make the message appear more credible. The attached RAR archive contains a malicious executable disguised as a PDF file. Opening this file launches LoptikMod, a remote access trojan that establishes persistence through scheduled tasks, connects to a remote server, sends system data, receives further instructions, downloads extra components, and extracts sensitive information.
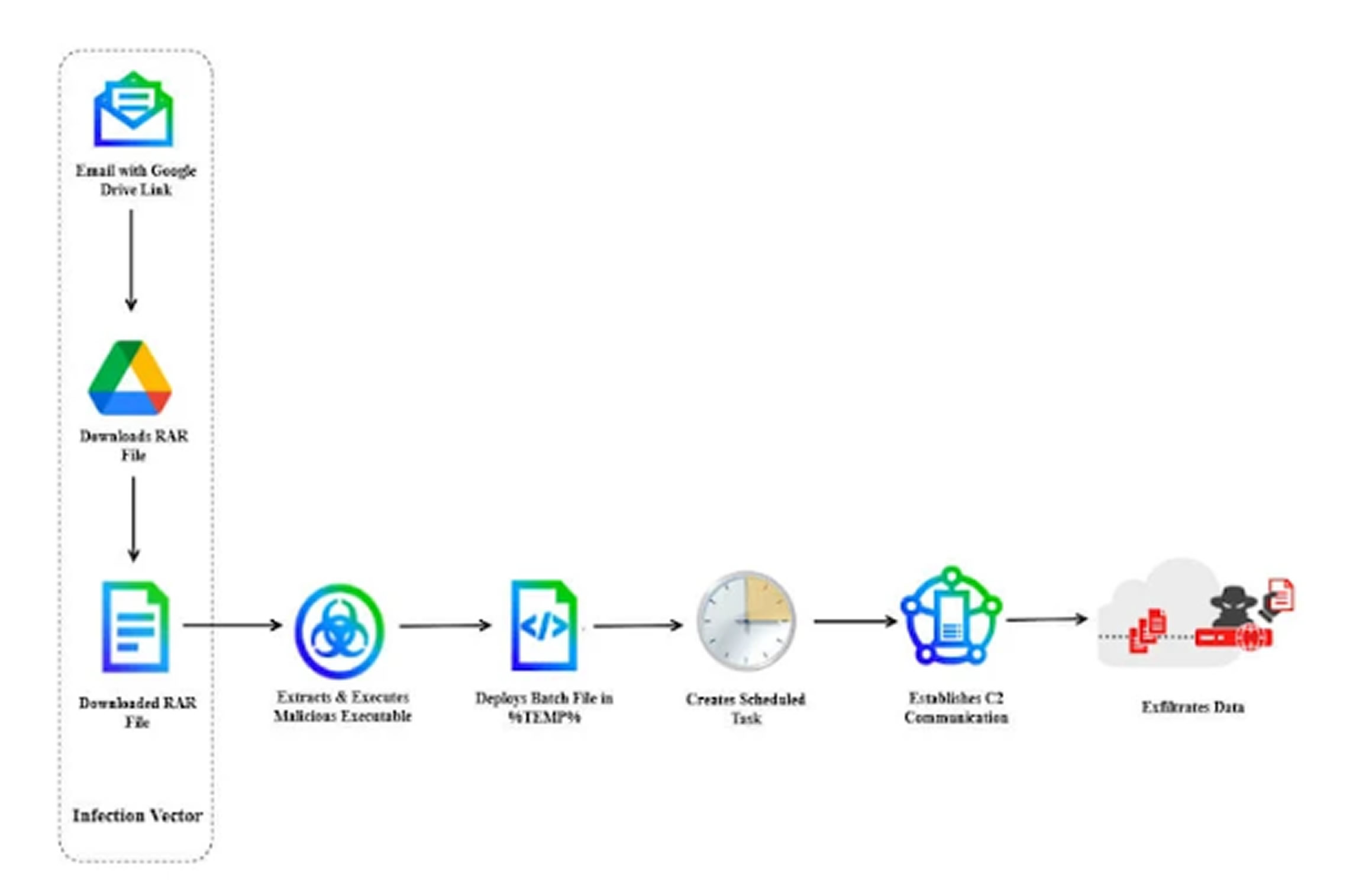
The malware also includes anti-virtual machine techniques and ASCII obfuscation to make analysis more difficult. Additionally, it ensures only one active instance is running at a time on the compromised system, reducing the risk of detection or disruption.
Trellix observed that the command-and-control server used in the operation is currently offline. This suggests the infrastructure may be temporarily shut down, permanently inactive, or relocated to a new server.
Because the C2 server is no longer active, researchers cannot currently determine the specific commands issued to infected systems or the types of data collected.
The researchers concluded that the group operates with a clear intent of long-term surveillance and data theft, driven by a cyber espionage agenda. Although their activities have historically focused on South Asia, this attack targeting South Asian embassies in Europe shows that their interests have expanded to include European diplomatic channels and intelligence.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.