New DslogdRAT Malware Targets Ivanti Connect Secure Vulnerability
Cybersecurity experts are raising alarms over a newly discovered malware named DslogdRAT, which has been deployed through a recently patched security flaw in Ivanti Connect Secure (ICS).
According to a report released Thursday by JPCERT/CC researcher Yuma Masubuchi, attackers exploited a then-unknown (zero-day) vulnerability—CVE-2025-0282—to install both DslogdRAT and a web shell on systems belonging to Japanese organizations around December 2024.
CVE-2025-0282 is a critical bug that enables remote code execution without authentication. Although Ivanti released a fix in early January 2025, the flaw had already been used by a China-linked cyber-espionage group known as UNC5337 to deliver the SPAWN malware suite, including tools like DRYHOOK and PHASEJAM. These tools have not yet been linked to any specific threat actor.
Since the initial attack, updates of the SPAWN malware—SPAWNCHIMERA and RESURGE—have been delivered via the same vulnerability, as confirmed by both JPCERT/CC and the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
Meanwhile, Google’s Mandiant team revealed that a different ICS vulnerability—CVE-2025-22457—was also exploited to spread SPAWN malware by a separate Chinese group dubbed UNC5221. JPCERT/CC noted it's unclear whether the DslogdRAT attacks are related to this campaign.
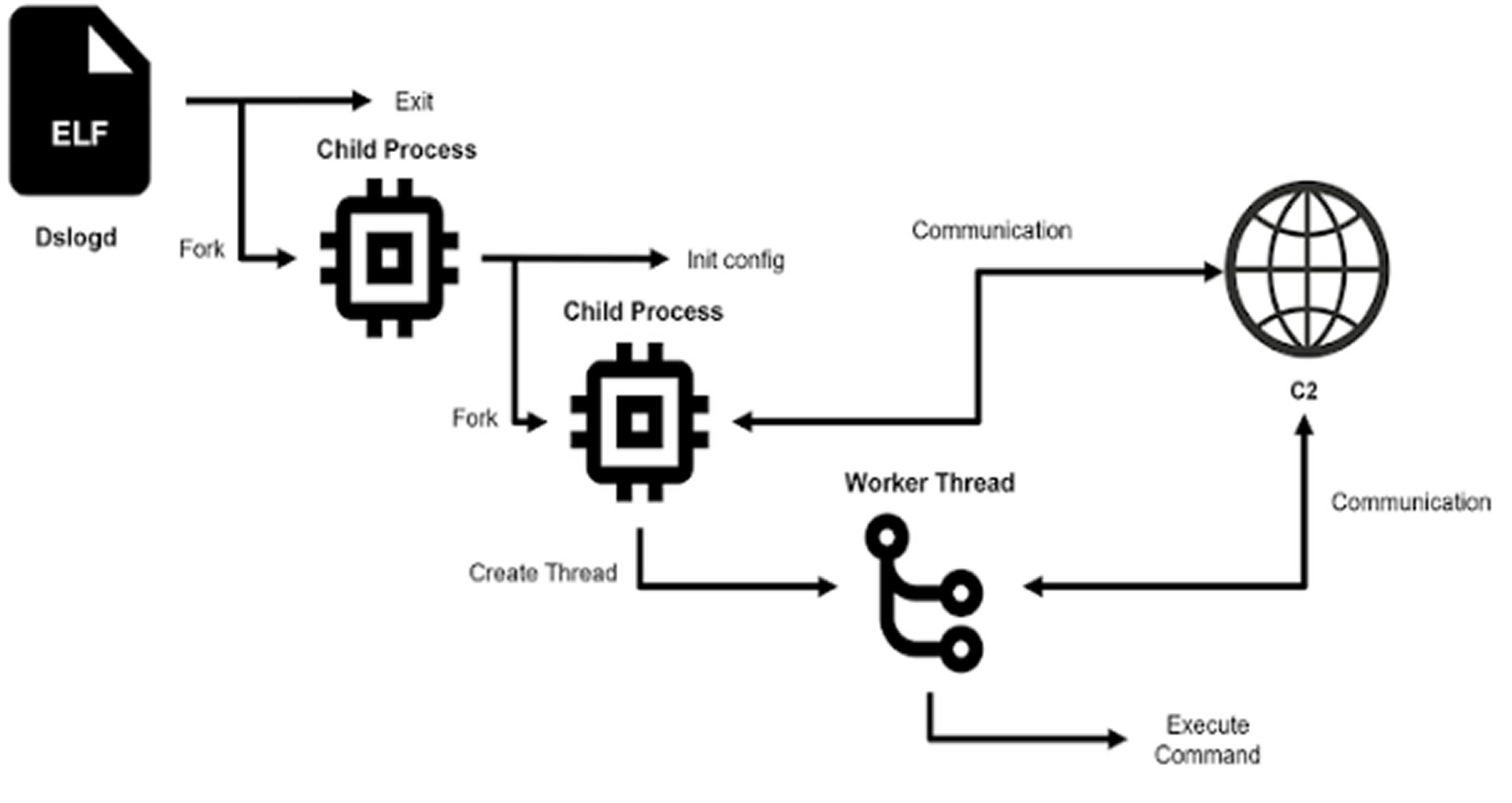
In the attack sequence, CVE-2025-0282 is used to plant a Perl-based web shell, which then facilitates the delivery of additional malware like DslogdRAT.
Once installed, DslogdRAT establishes a socket connection to an external server, transmits basic system info, and waits for further commands. It can execute shell commands, upload or download files, and use the infected device as a proxy.
This discovery comes amid a warning from threat intelligence firm GreyNoise, which reported a 900% increase in suspicious scanning activity targeting ICS and Ivanti Pulse Secure devices. In the past 24 hours alone, scans originated from over 270 unique IPs—more than 1,000 over the last 90 days.
Of these, 255 IP addresses are considered malicious—many using TOR exit nodes—while another 643 have been flagged as suspicious. The majority of these scans originated from the U.S., Germany, and the Netherlands.
GreyNoise cautioned: “This surge could signal coordinated reconnaissance and potential future exploits. Although no specific CVEs have been linked to the scanning, spikes like this often precede active attacks.”
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.