Cybersecurity experts have discovered a sophisticated ransomware campaign that targets and mocks Elon Musk supporters.
This operation, identified as a variant of Fog Ransomware, uses multiple stages of PowerShell scripts and payloads hosted on Netlify to carry out its malicious activities.
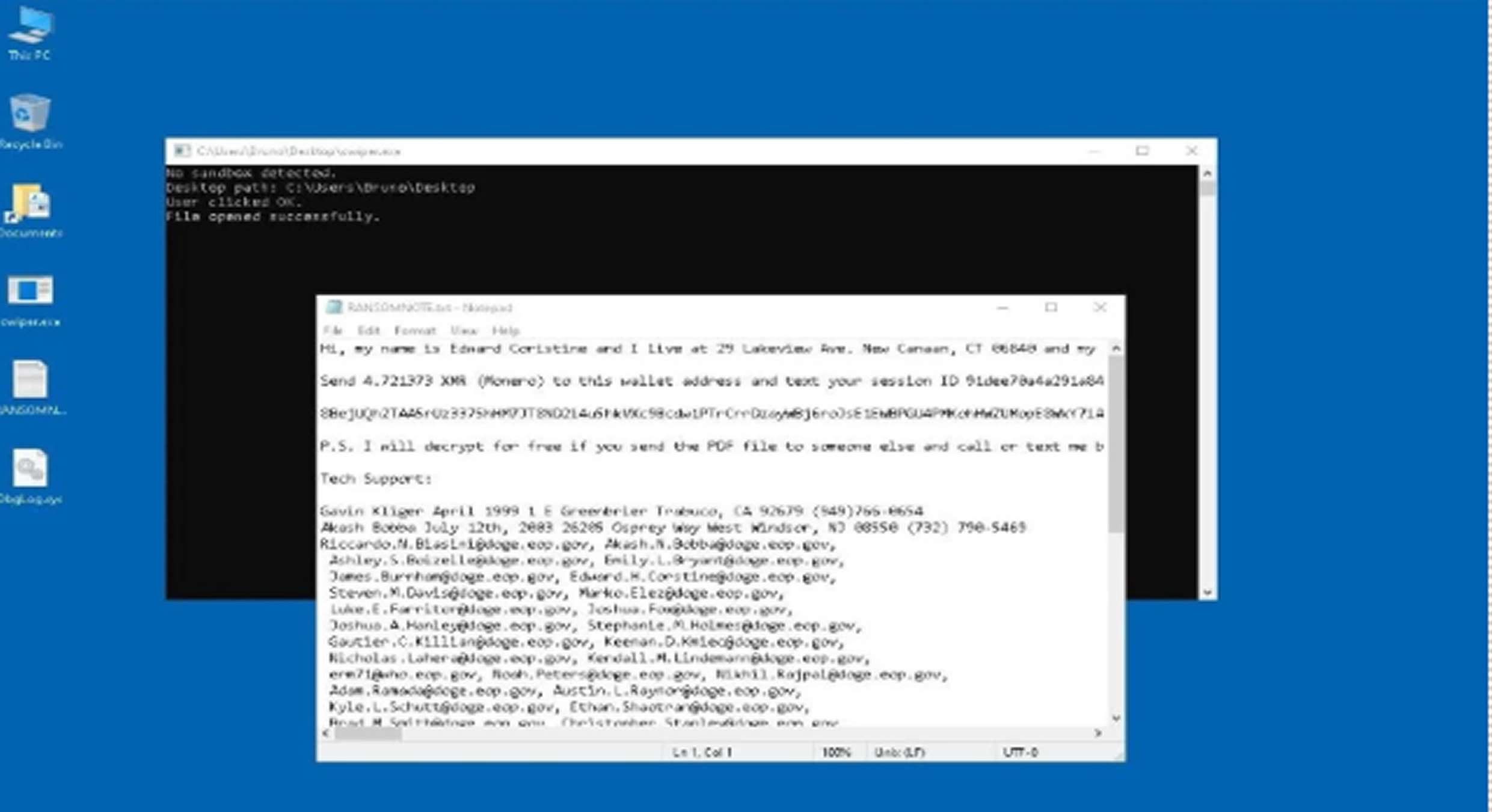
The campaign marks a troubling shift in politically-themed malware, blending financial motives with satirical elements. Its ransom note stands out by impersonating someone named “Edward Coristine,” who is allegedly linked to DOGE cryptocurrency. Strangely, the note includes government email addresses as technical support contacts and features mocking content aimed at Musk enthusiasts.
When activated, the malware plays a YouTube video that ridicules Elon Musk, serving as both a distraction and a reinforcement of its parodic intent.
Researchers at KrakenLabs uncovered the campaign after tracking infections to phishing emails disguised as “Pay Adjustment” notifications with PDF attachments.
The attack uses a complex chain involving .lnk file droppers and several stages of PowerShell execution. This method showcases a mix of technical skill and psychological manipulation designed to target specific audiences.
The full infection sequence is composed of multiple working components. It begins with a phishing PDF that links to a ZIP archive hosted on Netlify. This archive deploys PowerShell scripts, starting with “Pay.ps1,” which initiates the attack.
Key components include “cwiper.exe,” which handles the ransomware encryption; “ktool.exe,” which uses Intel’s Bring Your Own Vulnerable Driver (BYOVD) technique to gain kernel-level access; and tailored PowerShell scripts used for system reconnaissance.
Despite its mocking tone, the presence of a Monero wallet suggests that the true aim of the campaign is financial gain.
This combination of monetary incentive and political satire reflects a growing trend in ransomware attacks, where criminal objectives are hidden behind ideological or humorous fronts.
Infection Mechanism Breakdown
The attack begins when a victim opens a phishing PDF claiming to offer pay adjustment information.
This document directs the user to a Netlify-hosted site (hilarious-trifle-d9182e.netlify.app) that stores the malicious files.
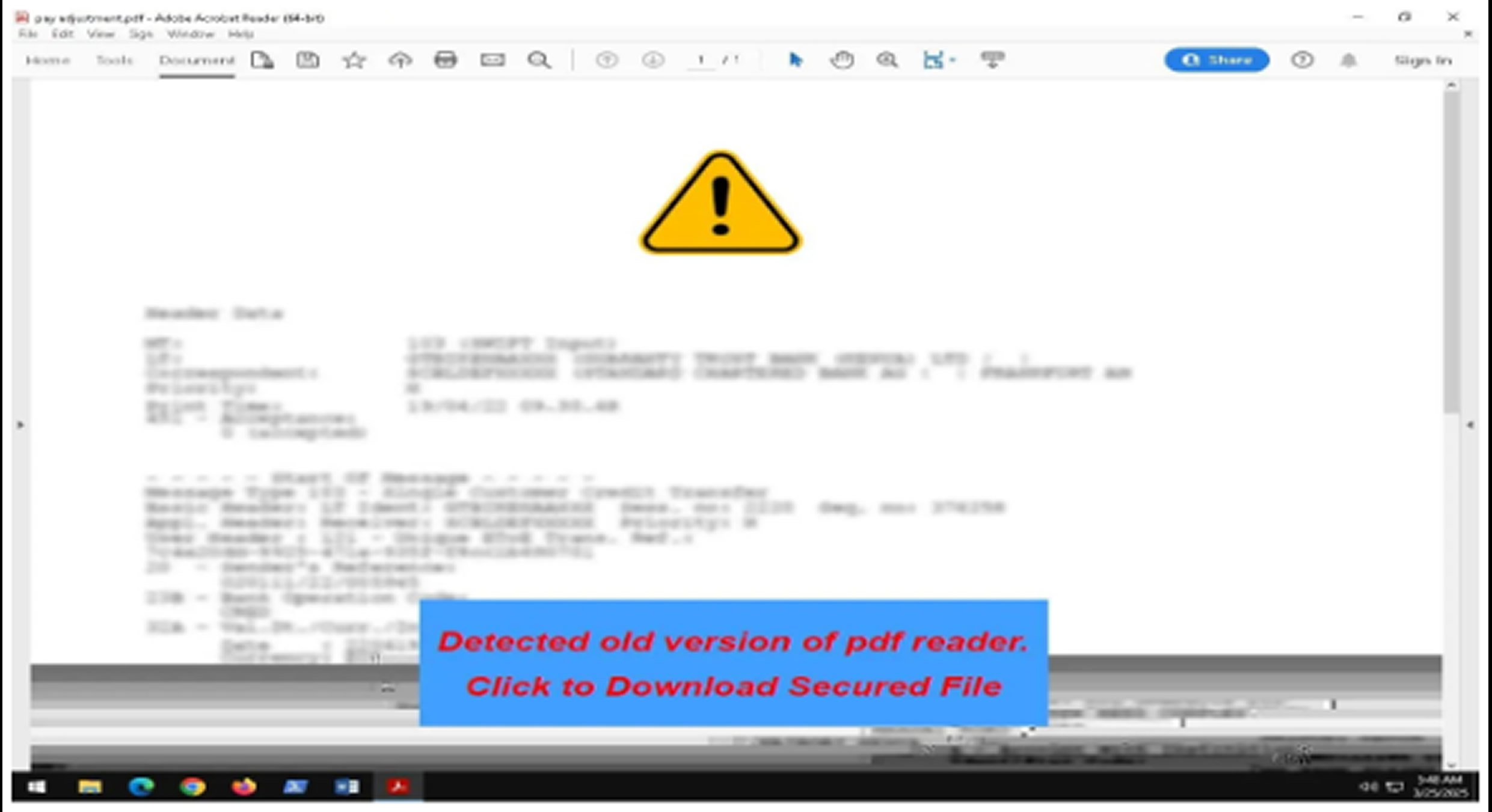
The first PowerShell script, “Pay.ps1,” serves as a loader that downloads and runs “stage1.ps1,” the central script managing the process. Among the most advanced components is “trackerjacker.ps1,” which uses XOR-based obfuscation to bypass detection systems.
Once decoded, this script gathers system data, while another script, “lootsubmit.ps1,” collects geolocation data using the Wigle API.
Together with “cwiper.exe” and “ktool.exe,” this campaign reveals a high level of technical expertise hidden beneath its satirical appearance.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


