Russian Hosting Provider Proton66 Linked to Global Surge in Cyberattacks
Cybersecurity researchers have reported a sharp increase in cyberattacks—including mass scanning, credential brute-force attempts, and exploitation efforts—traced to IP addresses linked to a Russian bulletproof hosting provider called Proton66.
According to Trustwave SpiderLabs’ two-part report, the attacks have been active since January 8, 2025, and have affected organizations worldwide. IP blocks 45.135.232.0/24 and 45.140.17.0/24 were especially aggressive, with many IPs showing no prior history of malicious activity or having remained dormant for over two years.
Proton66 is believed to be connected to PROSPERO, another Russian autonomous system. Previous research by French cybersecurity firm Intrinsec tied both to bulletproof hosting services advertised under Securehost and BEARHOST. Malware families such as GootLoader and SpyNote have used Proton66 infrastructure for command-and-control (C2) servers and phishing campaigns.
In a separate report, journalist Brian Krebs revealed that Prospero may be routing its activity through networks associated with Kaspersky Lab. However, Kaspersky denied any collaboration, clarifying that any routing through its networks was incidental due to its partnerships with telecom providers.
Trustwave’s latest analysis reveals that Proton66 IPs (e.g., 193.143.1[.]65) have been used to exploit several recent critical vulnerabilities:
- CVE-2025-0108: Auth bypass in Palo Alto Networks PAN-OS
- CVE-2024-41713: Input validation flaw in Mitel MiCollab
- CVE-2024-10914: Command injection in D-Link NAS
- CVE-2024-55591 & CVE-2025-24472: Auth bypasses in Fortinet FortiOS
These Fortinet flaws have also been linked to Mora_001, an initial access broker associated with the SuperBlack ransomware.
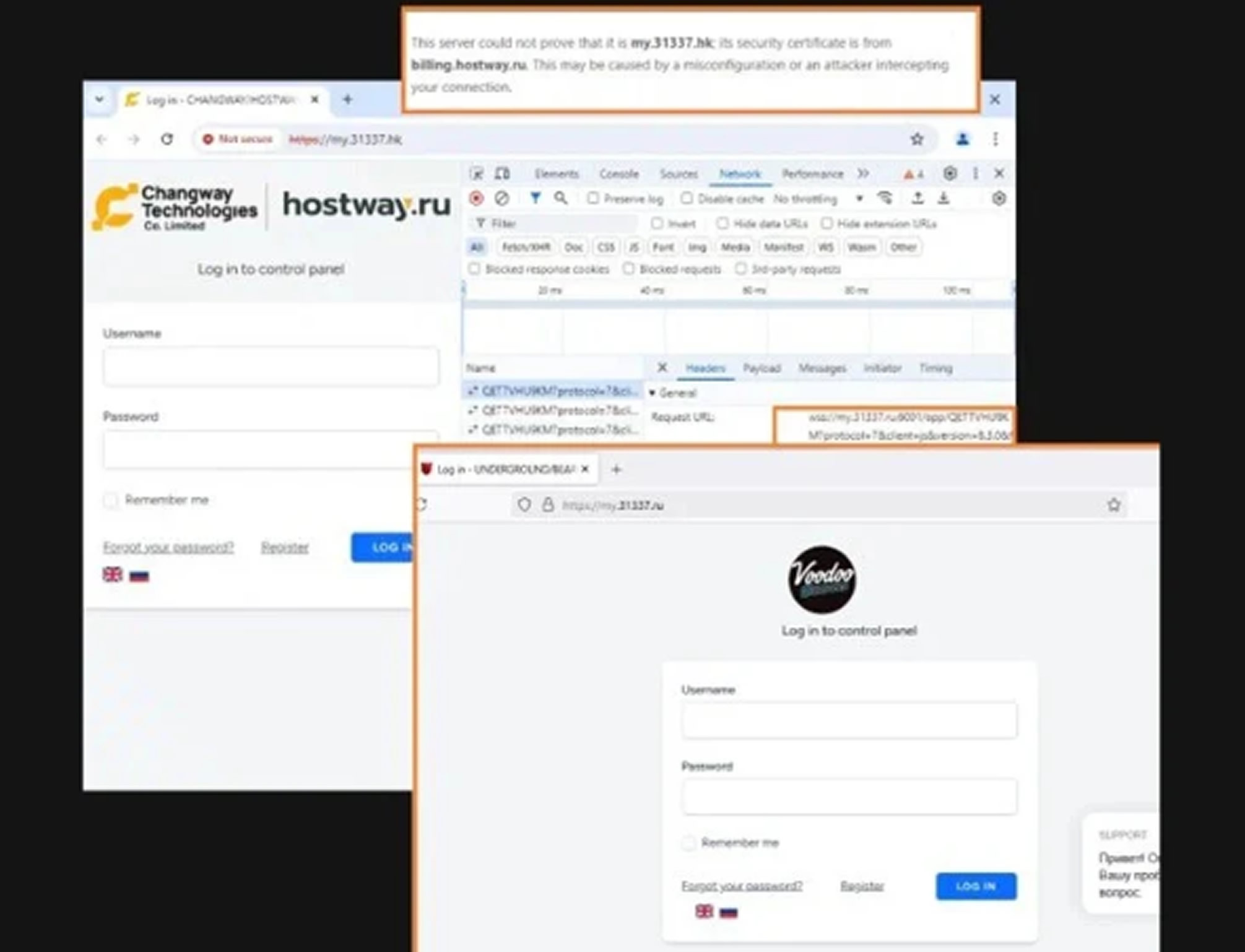
Additionally, malware campaigns connected to Proton66 have spread variants such as XWorm, StrelaStealer, and WeaXor ransomware. One notable campaign used compromised WordPress sites (e.g., 91.212.166[.]21) to redirect Android users to fake Google Play pages distributing malicious APKs. These phishing attempts were tailored for French, Spanish, and Greek-speaking users and used obfuscated JavaScript to avoid detection.
Another attack chain targeted Korean chat room users, beginning with a malicious LNK file that launched a PowerShell script. This led to the download of a Base64-encoded .NET DLL, which ultimately delivered the XWorm malware.
In Germany, Proton66-linked infrastructure hosted a phishing campaign distributing StrelaStealer—an information-stealing malware communicating with 193.143.1[.]205.
Meanwhile, WeaXor ransomware (a variant of Mallox) was found connecting to a C2 server at 193.143.1[.]139, also within Proton66’s network.
To mitigate these risks, experts recommend blocking all CIDR ranges associated with Proton66 and Chang Way Technologies, a potentially connected hosting provider based in Hong Kong.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


