Google’s Threat Intelligence Group (GTIG) reported tracking 75 zero-day vulnerabilities exploited in 2024, a decrease from 98 in 2023 but an increase from 63 in 2022.
The analysis highlights a growing trend of attacks targeting end-user platforms, though enterprise technologies are increasingly in the crosshairs.
The report points to evolving attacker tactics, improved vendor defenses, and challenges in detecting commercial surveillance activities. In 2024, 44% of zero-day vulnerabilities targeted enterprise products, up from 37% in 2023, mainly driven by attacks on security and networking software. Over 60% of zero-day exploits against enterprise tech affected these tools, which offer attackers efficient access to systems and networks.
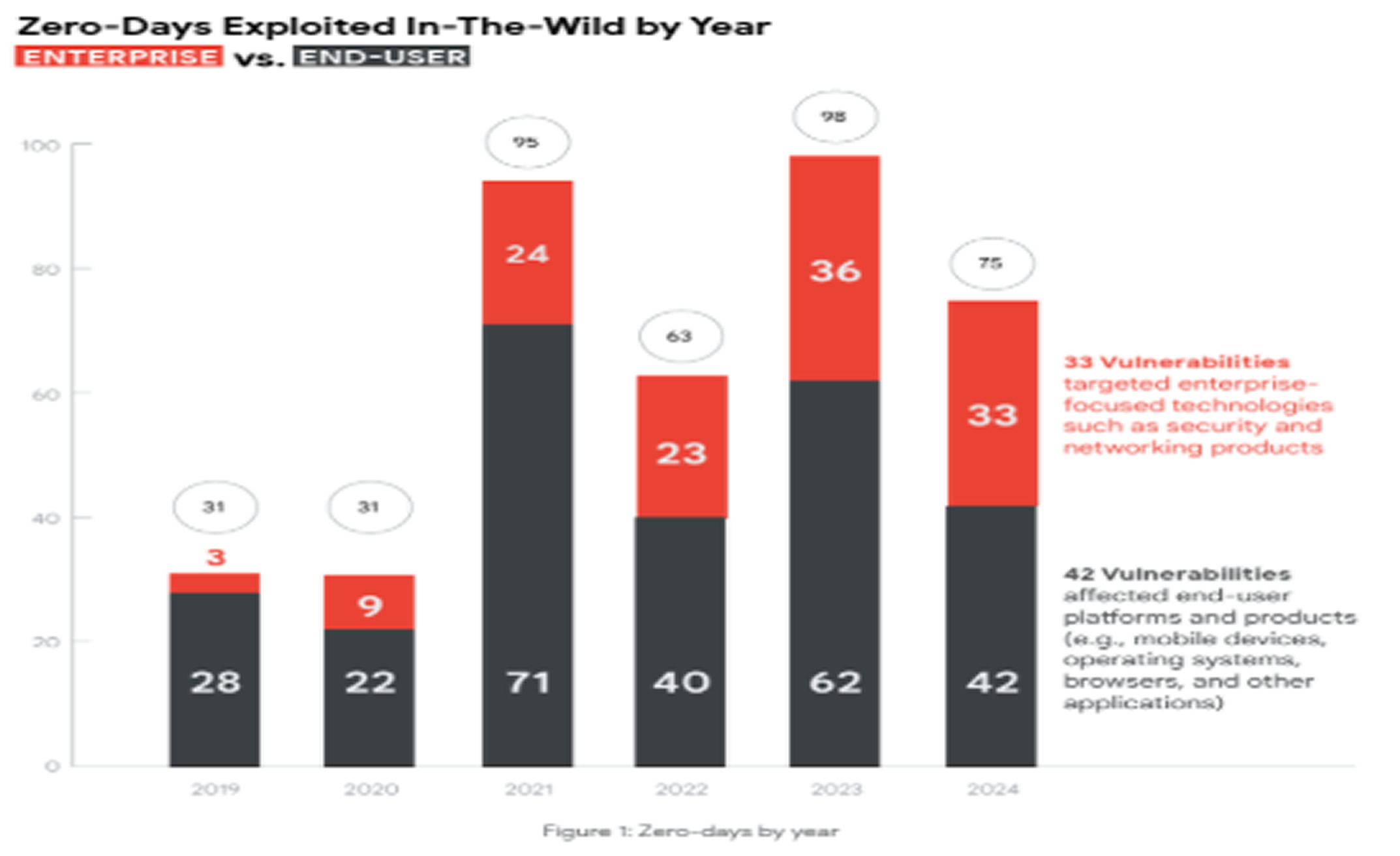
Browser and mobile exploits saw a decline, while attacks on end-user platforms remained at 56%. Google Chrome was the most targeted browser, with mobile attacks often utilizing exploit chains. Zero-day activity in desktop operating systems rose, with Microsoft Windows continuing to be a prime target, reflecting its widespread use. Microsoft Windows exploitation increased from 13 zero-days in 2022 to 16 in 2023, and 22 in 2024.
Enterprise products from companies like Ivanti, Palo Alto, and Cisco were targeted due to limited endpoint detection and response (EDR) monitoring, allowing single flaws to compromise entire systems. Over half of zero-day vulnerabilities in 2024 enabled remote code execution or privilege escalation, with the top vulnerabilities being use-after-free, command injection, and cross-site scripting (XSS).
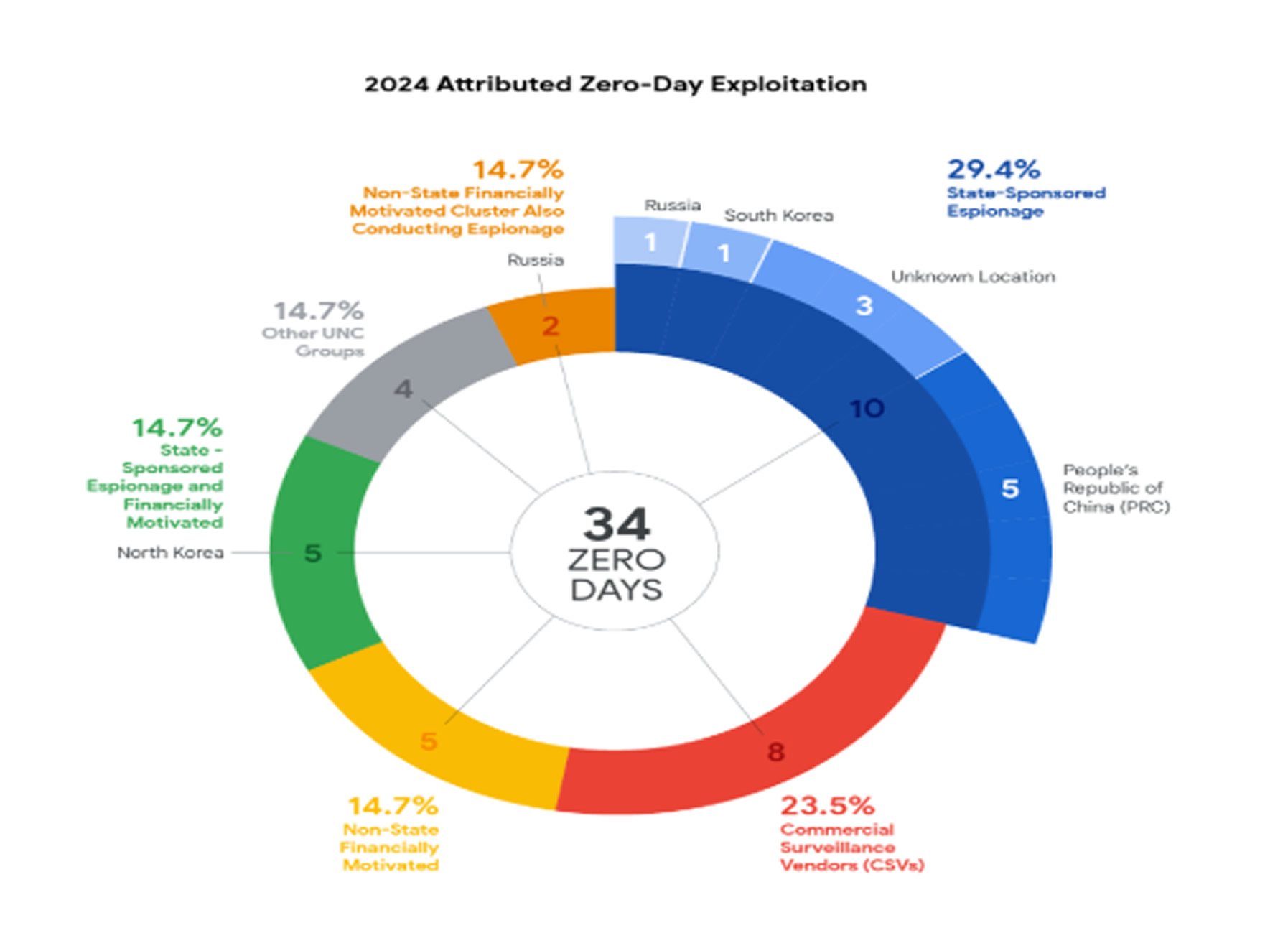
The report also notes that 53% of the zero-day cases were attributed to cyber espionage groups, particularly nation-state and commercial surveillance vendors (CSVs). While the number of zero-day exploits attributed to CSVs declined from 2023 to 2024, their role in zero-day exploitation has significantly expanded, indicating increased access to these vulnerabilities.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.