A major supply chain vulnerability, identified as “GerriScary” (CVE-2025-1568), could have
allowed attackers to insert malicious code into at least 18 key Google projects, such as ChromiumOS, Chromium, Dart, and Bazel.
Discovered by Tenable security researcher Liv Matan, the flaw stems from misconfigurations in Google’s Gerrit code collaboration platform. These misconfigurations enabled unauthorized users to compromise trusted repositories through a sophisticated series of actions.
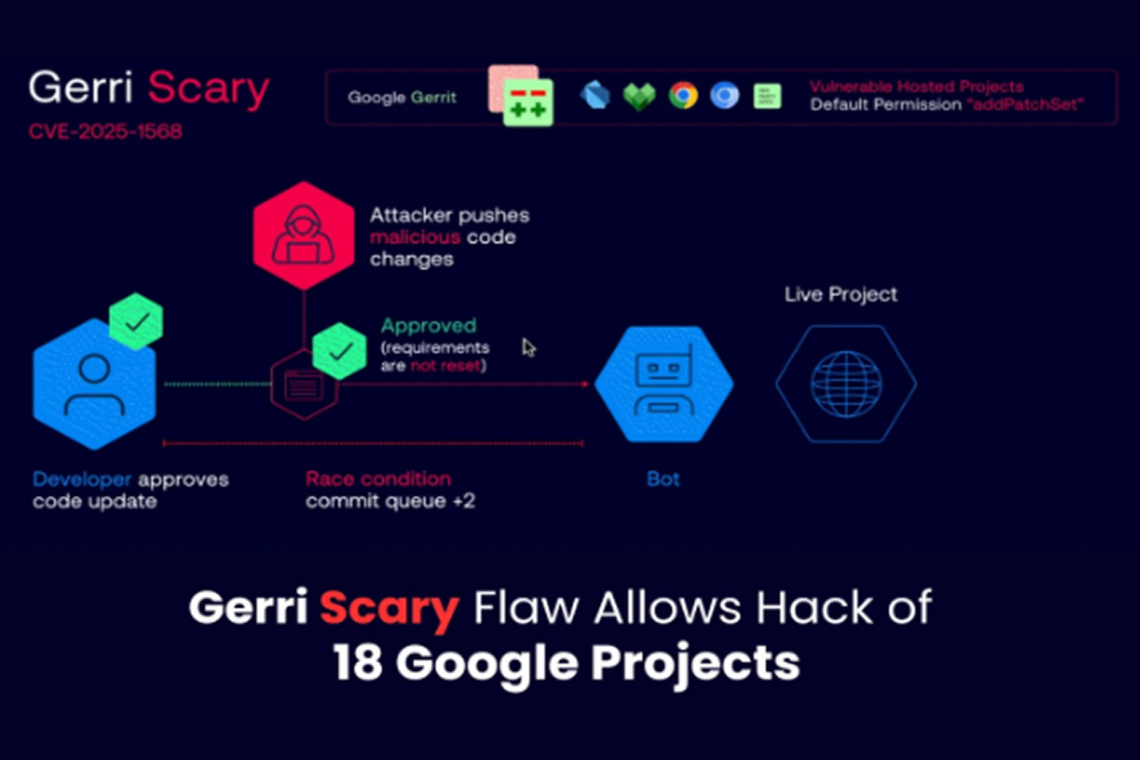
The GerriScary exploit relied on three key elements. First, Gerrit’s default settings grant the “addPatchSet” permission to all registered users, meaning anyone with a Google account could alter existing code changes. Second, several projects contained flaws in their “Copy Conditions,” which decide whether code review approvals carry over to new revisions.
The most severe part of the exploit involved a race condition with automated bots responsible for code submission. Attackers could monitor code changes that were already approved with the “Commit-Queue +2” label, signaling they were ready for merging, and inject malicious patches in the brief time before the bot executed. In repositories like ChromiumOS and Dart, this window was roughly five minutes, while others had only a few seconds to a couple of minutes.
Liv Matan demonstrated that it was possible to identify vulnerable repositories by checking HTTP response codes when attempting to modify commit messages. A “209” status code indicated that the necessary permissions were in place without generating log entries. This method allowed broad scanning of Google’s Gerrit infrastructure to detect affected projects.
The attack worked by tracking changes that were ready for submission and exploiting the timing gap before the bots acted. If a malicious patch was submitted during this short window, and approval settings were misconfigured, the patch would retain prior approvals and be merged automatically without user intervention.
The vulnerability affected a wide range of critical projects. ChromiumOS, which powers Chrome OS devices, was a primary target. Other impacted projects included Dart, BoringSSL, Bazel, Dawn, and Gerrit itself. Additional vulnerable repositories were Ceres Solver, Quiche, Android KVM, and several Linux-related projects.
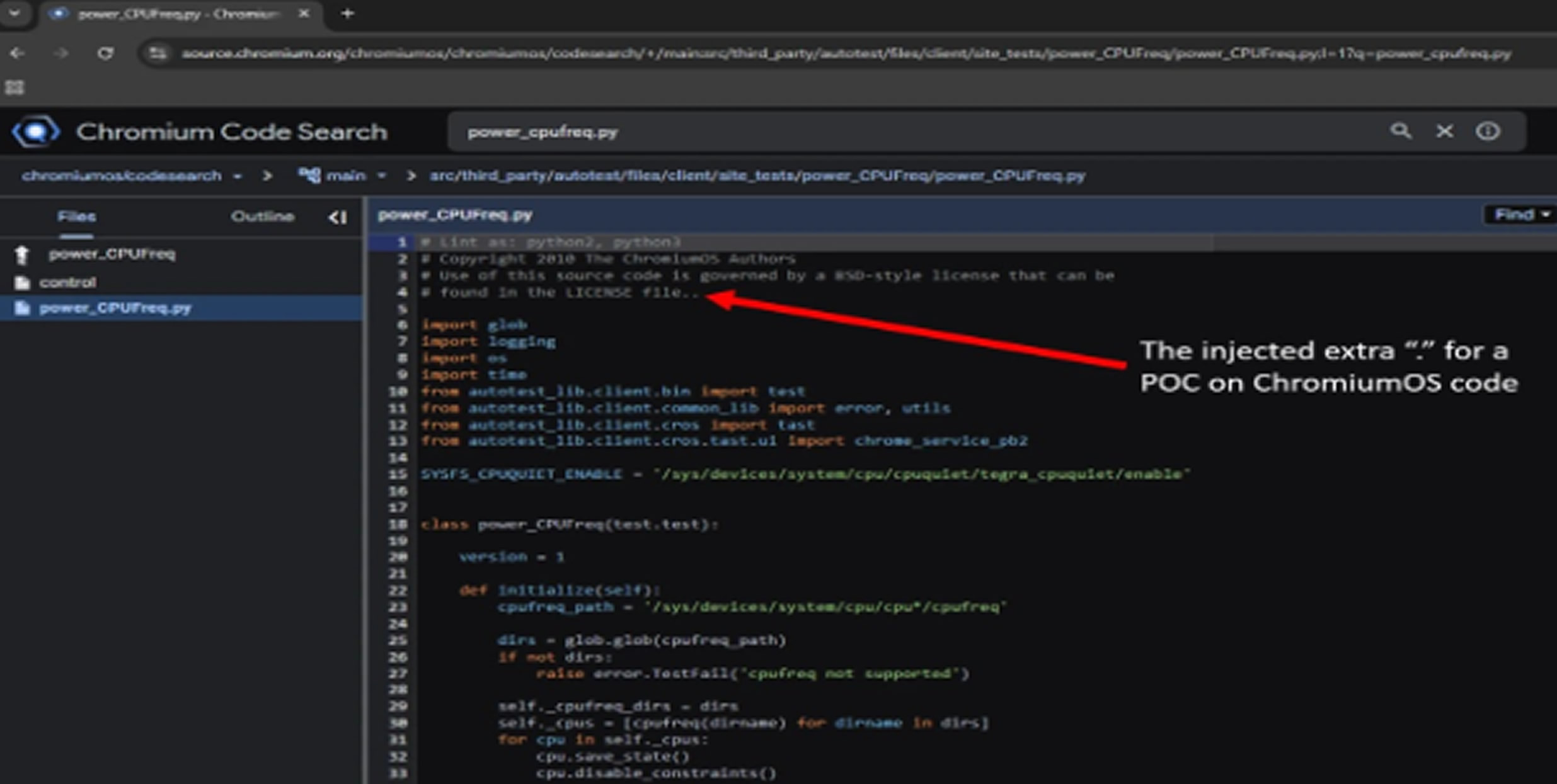
Liv Matan showcased the issue by injecting harmless comments into ChromiumOS repositories, which can be found in the public code search tool. To follow ethical standards, they refrained from fully exploiting the race condition in live environments. Google acted promptly, updating configuration settings across projects to ensure new revisions require fresh approvals.
The ChromiumOS team also removed the “addPatchSet” permission from general registered users, reserving it for trusted contributors. While Google addressed the issue within its own ecosystem, researchers caution that other organizations using Gerrit might still be exposed.
Because configuring Copy Conditions correctly is complex, similar misconfigurations may exist in many other Gerrit-based projects, posing ongoing risks of supply chain attacks.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.