Cybercriminals Exploit QR Codes to Steal Login Credentials
Cybercriminals have discovered a new method to steal login credentials, requiring nothing more than a quick scan of a QR code. This attack, commonly referred to as “quishing” (QR phishing), has been targeting victims across the US and Europe.
A Sneaky Evolution of Phishing
Phishing scams have become increasingly sophisticated, and QR code-based attacks take deception to a whole new level. Unlike traditional phishing, where suspicious links might raise red flags, quishing hides the trap within a simple scannable image. One scan, and the victim could unknowingly hand over their credentials without any immediate warning.
According to Unit 42 researchers, cybercriminals have been actively using this tactic since 2024, primarily to steal Microsoft login credentials. Victims are tricked into scanning QR codes that direct them to malicious websites, where they are prompted to enter their credentials—handing them directly to attackers.
How Attackers Bypass Security Systems
These QR code scams don’t just trick users—they also evade security defenses. Cybercriminals cleverly use trusted redirects to disguise malicious links, making them appear legitimate. Additionally, they take advantage of Cloudflare Turnstile verification, which helps them bypass security scans designed to detect fraudulent activity.
One of the most alarming aspects of these attacks is the use of personalized fake login pages. Instead of blindly collecting credentials, attackers reject incorrect login attempts, ensuring that only valid credentials are captured. This increases their success rate and makes it harder for victims to recognize the attack.
Targeted and Industry-Specific Attacks
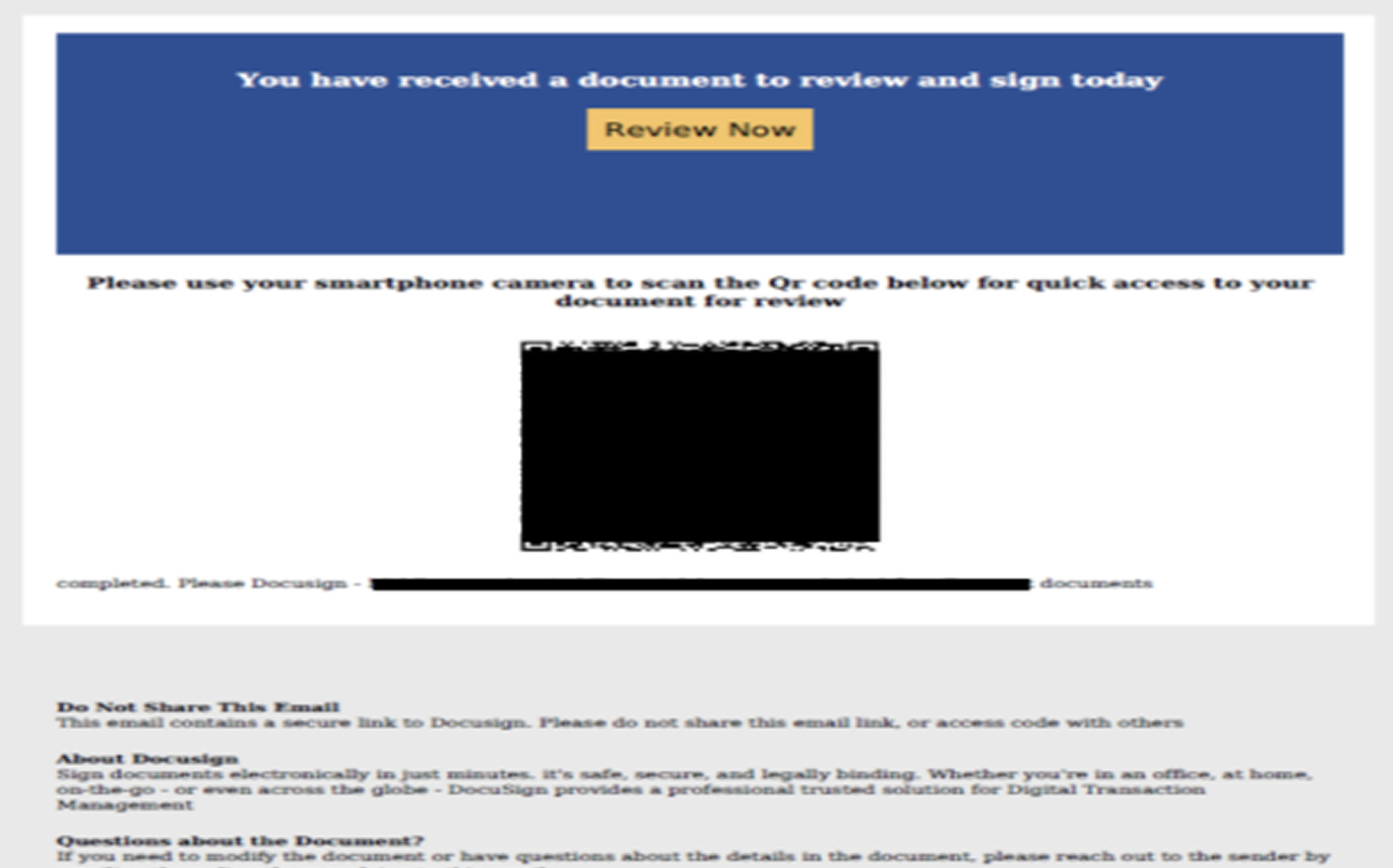
Unlike traditional phishing, which often casts a wide net, quishing attacks are highly targeted. Researchers found that specific individuals and industries—including medical, automotive, education, energy, and financial sectors—are being targeted based on pre-attack reconnaissance.
Victims typically receive emails impersonating trusted services like Adobe Acrobat Sign, DocuSign, or HR payroll updates. These emails contain PDF attachments with embedded QR codes, urging users to scan them to “sign a document.” The realistic branding, including company logos and official-sounding subject lines, makes it difficult for users to detect the scam.
Why QR Code Phishing is So Dangerous
Attackers exploit human psychology and security blind spots to increase their chances of success. One of the biggest risks is that QR codes bypass traditional email security scans, as the malicious link is hidden inside an image rather than a visible hyperlink.
Furthermore, users tend to scan QR codes with personal devices, which are often less protected than corporate systems. Since QR codes don’t reveal the full URL before scanning, victims may not realize they are being redirected to a malicious site until it’s too late.
To make matters worse, attackers use redirection mechanisms and trusted website exploits to
further obscure the phishing link. Even tech-savvy users may struggle to spot the deception.
The Ultimate Goal: Credential Theft
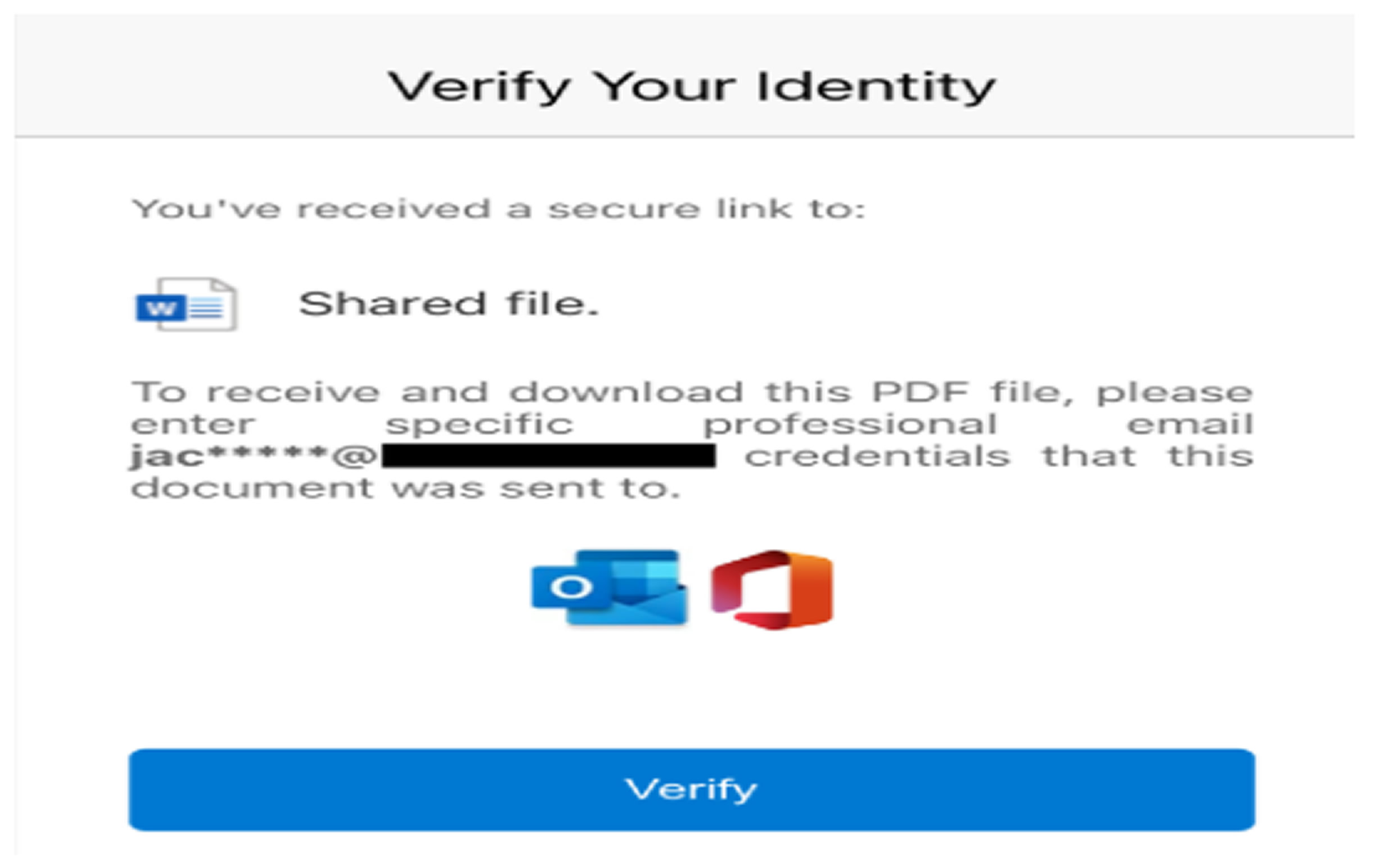
Once victims scan the QR code, they are redirected to a fake Microsoft 365 login page that looks identical to the real one. If they enter their credentials, attackers steal their sensitive information, potentially gaining access to corporate accounts, emails, and other critical data.
What makes these attacks particularly dangerous is their precision. Instead of blindly collecting credentials, attackers use targeted name lists and customize login pages to reject incorrect credentials. This ensures that only the real victim falls for the scam, increasing the attack’s effectiveness.
How to Protect Yourself
To stay safe from QR code phishing scams, cybersecurity experts recommend several best practices. First, always verify the sender before scanning any QR code received via email. If an email seems suspicious or unexpected, it’s best to confirm its legitimacy through official channels.
Second, be cautious about scanning QR codes that lead to login pages. If you must log in, manually enter the website address instead of using the QR code. Using corporate devices rather than personal phones for work-related actions can also help reduce exposure to these attacks.
Finally, enabling multi-factor authentication (MFA) adds an extra layer of security. Even if an attacker manages to steal credentials, MFA can prevent unauthorized access.
With cybercriminals refining their techniques, awareness is the first line of defense. Stay vigilant, and think twice before scanning that QR code.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


