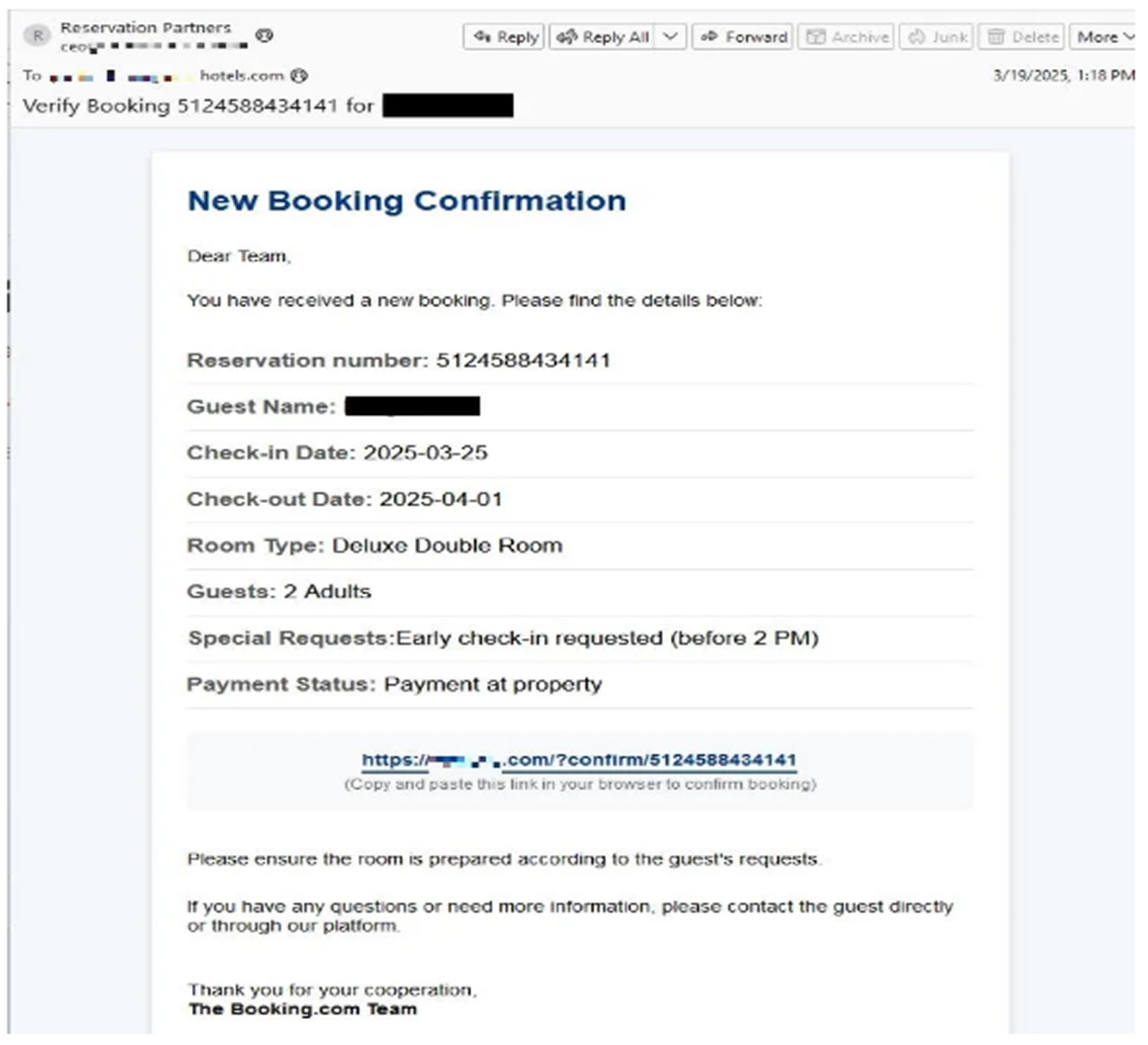
A new phishing campaign has been uncovered, specifically targeting the hospitality industry, with cybercriminals impersonating
Booking.com to deceive hotel staff into installing malware.
This attack exploits social engineering tactics and the urgency associated with hotel bookings, pressuring victims to act quickly without verifying security details. The scammers send fraudulent emails that appear to come from Booking.com, containing seemingly legitimate reservation details such as check-in dates (set just a few days ahead), room specifications, and guest information to enhance credibility.
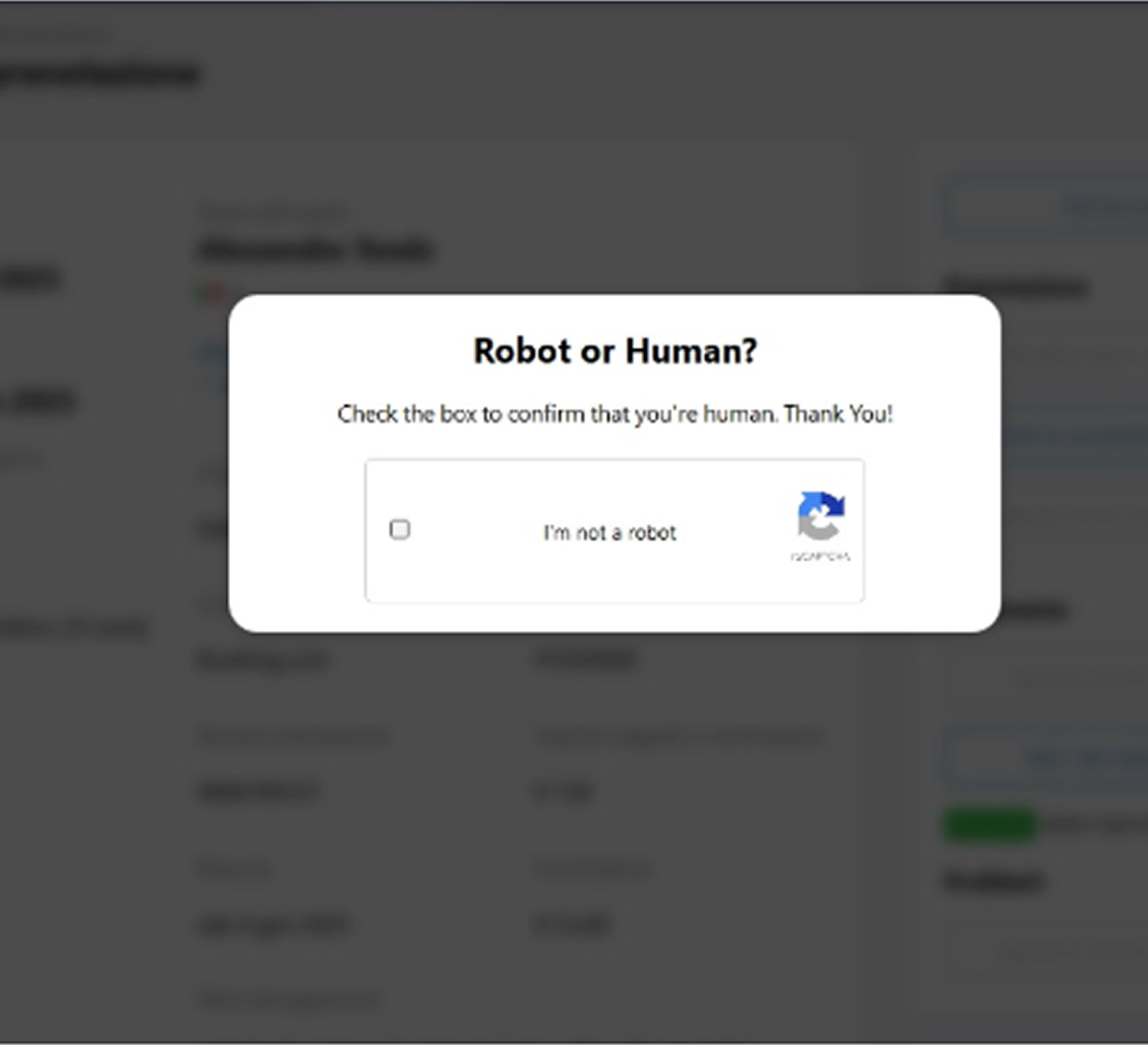
The emails instruct hotel staff to copy and paste a URL into their browser to confirm the booking. However, this link directs them to a fraudulent website featuring a fake CAPTCHA verification interface. Malwarebytes researchers have noted that this aligns with recently observed phishing campaigns using fake CAPTCHA schemes, showing an evolution in cybercriminal tactics.
Once victims interact with the fake CAPTCHA, they receive further instructions guiding them through a dangerous infection chain. They are prompted to press Windows Key + R, open the Run dialog box, paste copied content from the clipboard, and press Enter.
Infection Mechanism
The malicious code that victims unknowingly execute is an mshta command, which fetches and runs remote scripts. Mshta is a legitimate Windows utility designed for executing HTA (HTML Application) files, which can contain JavaScript or VBScript. In this case, the attacker’s script is pulled from a remote server and executed on the system.
Once executed, the malware likely establishes persistence on the victim’s machine while evading security detection. The primary objective appears to be gaining access to customer payment details and personal data stored in hotel management systems—highly valuable information on dark web marketplaces.
This campaign highlights how cybercriminals continue refining social engineering techniques, tailoring attacks to specific industries. As these methods become more sophisticated, traditional security awareness training may not be enough, emphasizing the need for continuous education and advanced security measures in the hospitality sector.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


