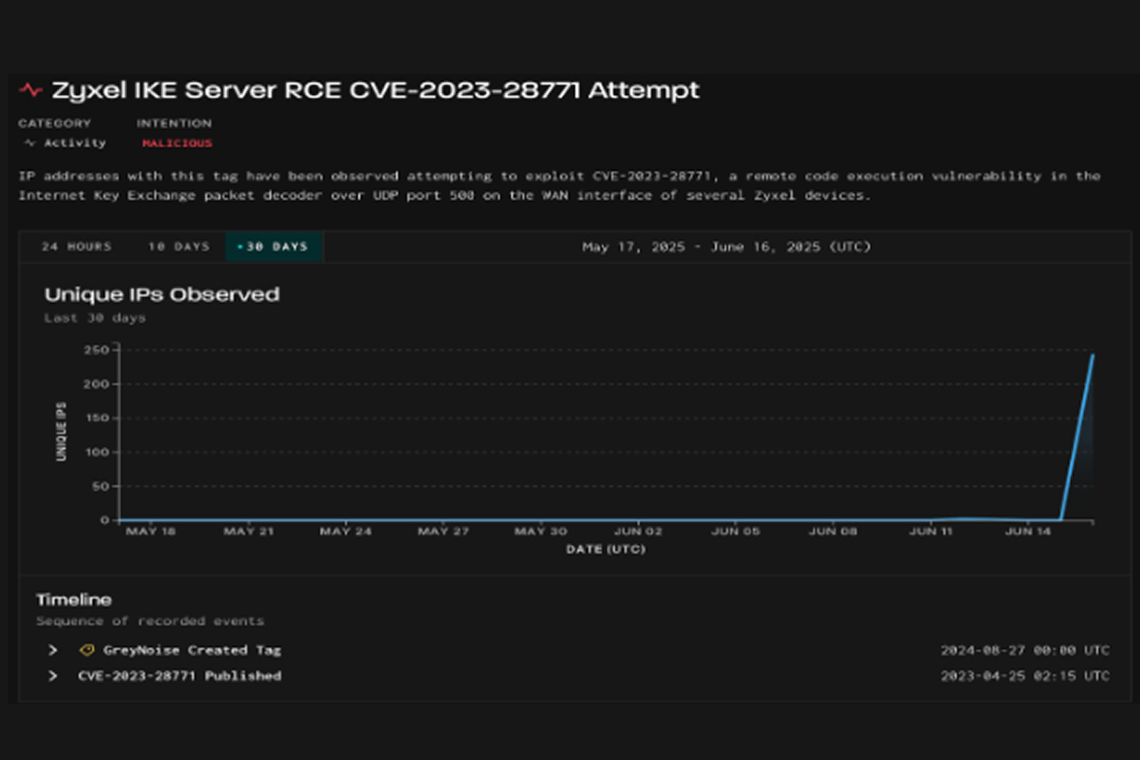
Researchers at GreyNoise have identified attempts to exploit the remote code execution vulnerability tracked as CVE-2023-28771 in Zyxel devices.
On June 16, the team detected a spike in exploitation attempts targeting this flaw, which carries a CVSS score of 9.8. The vulnerability affects Zyxel IKE decoders via UDP port 500.
“Exploitation attempts against CVE-2023-28771 were minimal in recent weeks. However, on June 16, GreyNoise recorded a sudden surge of activity, observing 244 unique IP addresses attempting to exploit the flaw,” the alert noted.
The primary countries targeted included the United States, the United Kingdom, Spain, Germany, and India. Notably, the attacking IPs had shown no suspicious behavior in the two weeks leading up to June 16 and focused exclusively on this particular vulnerability. All 244 IP addresses appeared to originate from Verizon Business in the U.S. Still, because the attack vector uses UDP port 500, researchers caution that the IPs could be spoofed and may not reflect the true origin. GreyNoise attributed the exploit activity to variants of the Mirai botnet, a link that was later supported by VirusTotal findings.
GreyNoise offered the following mitigation steps:
- Block malicious IP addresses: Although spoofing is possible, all 244 IPs have been flagged as malicious. Security teams are advised to block these addresses and monitor for any related threats.
- Assess Zyxel device exposure: Ensure that all internet-facing Zyxel devices have been updated to address CVE-2023-28771.
- Monitor for signs of post-exploitation: Exploitation could result in the devices being added to botnets or further compromised. Watch for unusual activity on affected systems.
- Restrict IKE/UDP port 500 access: Apply network-level filtering to minimize unnecessary exposure to this port.
Zyxel released patches for CVE-2023-28771 in April 2023, urging customers to apply the fixes immediately. The company also warned that attackers were actively exploiting the command injection flaw to install malware on vulnerable systems.
By the end of May 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability to its Known Exploited Vulnerability Catalog based on confirmed evidence of active exploitation.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.