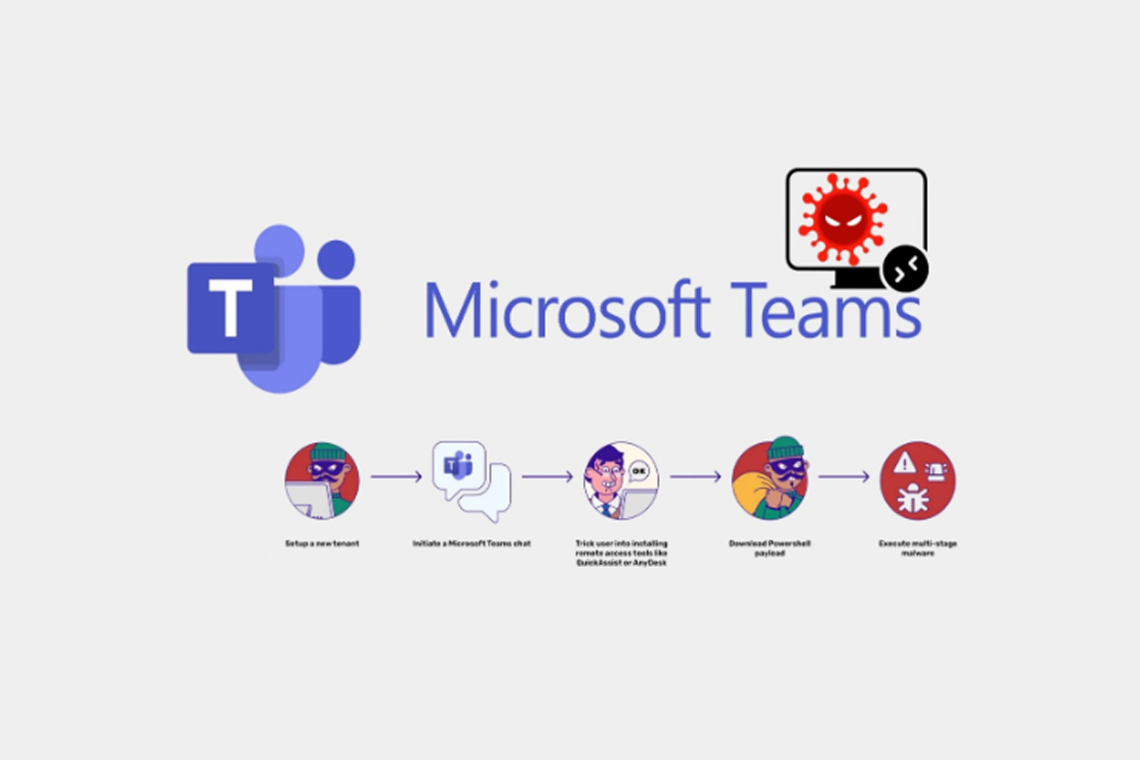
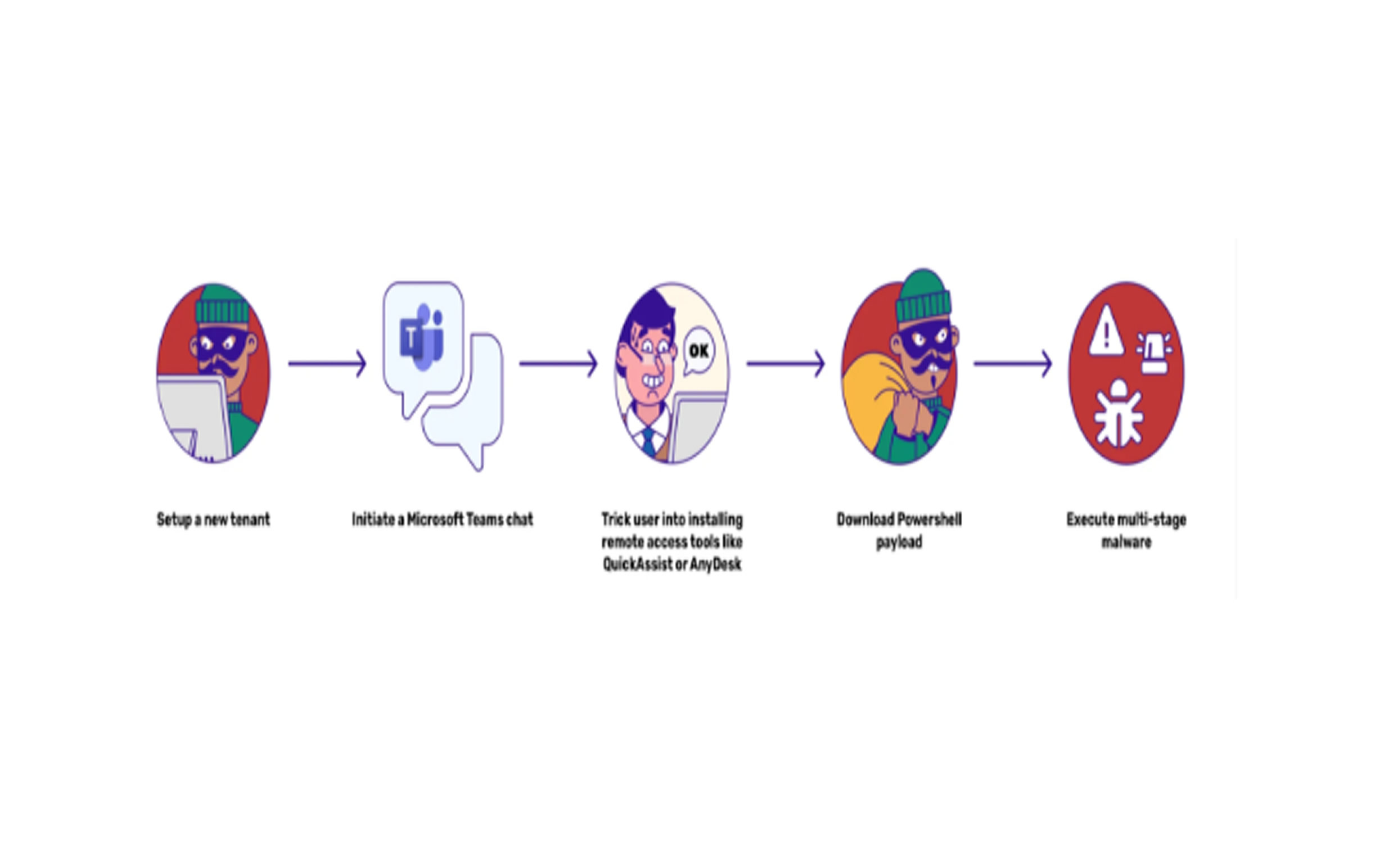
Cybercriminals are targeting Microsoft Teams to deliver malware and gain remote access to corporate systems. By posing as IT support staff, attackers trick employees into installing remote access tools like QuickAssist or AnyDesk.
These fake accounts often use names like “IT SUPPORT” and mimic internal staff, making the deception more convincing. Once access is granted, attackers deploy PowerShell-based malware capable of stealing credentials, executing remote commands, and maintaining long-term control.
Recent campaigns have used malware loaders such as DarkGate and Matanbuchus. Some attacks are linked to a group known as Water Gamayun, which targets IT professionals with custom malware and social engineering.
To stay safe, employees should verify any request for credentials or software installation through a separate, trusted channel. Combining technical defenses with strong user awareness is key to preventing these attacks.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.