RansomHub Affiliates Linked to Other Ransomware Groups Through EDR Disabling Tool
A new investigation has revealed connections between affiliates of RansomHub and other ransomware groups, including Medusa, BianLian, and Play. The link is tied to the use of a specialized tool designed to disable endpoint detection and response software on infected systems.
Cybersecurity researchers from ESET identified this tool, known as EDRKillShifter, which was first observed being used by RansomHub actors in August 2024. The primary function of EDRKillShifter is to neutralize security defenses on a compromised system, allowing ransomware to execute without being detected.
How the Attack Works
EDRKillShifter relies on a well-known strategy called Bring Your Own Vulnerable Driver. This method involves exploiting legitimate but vulnerable drivers to terminate security programs protecting the targeted endpoint. By eliminating security defenses, the ransomware can operate freely without being flagged by detection tools.
According to cybersecurity experts, ransomware affiliates prioritize gaining administrative privileges during an attack. Once they achieve this level of access, they deploy EDR killers to disable security software before executing the ransomware encryptor. This approach is particularly important because ransomware developers rarely make significant updates to their encryptors, as frequent modifications could introduce flaws that security vendors might exploit.
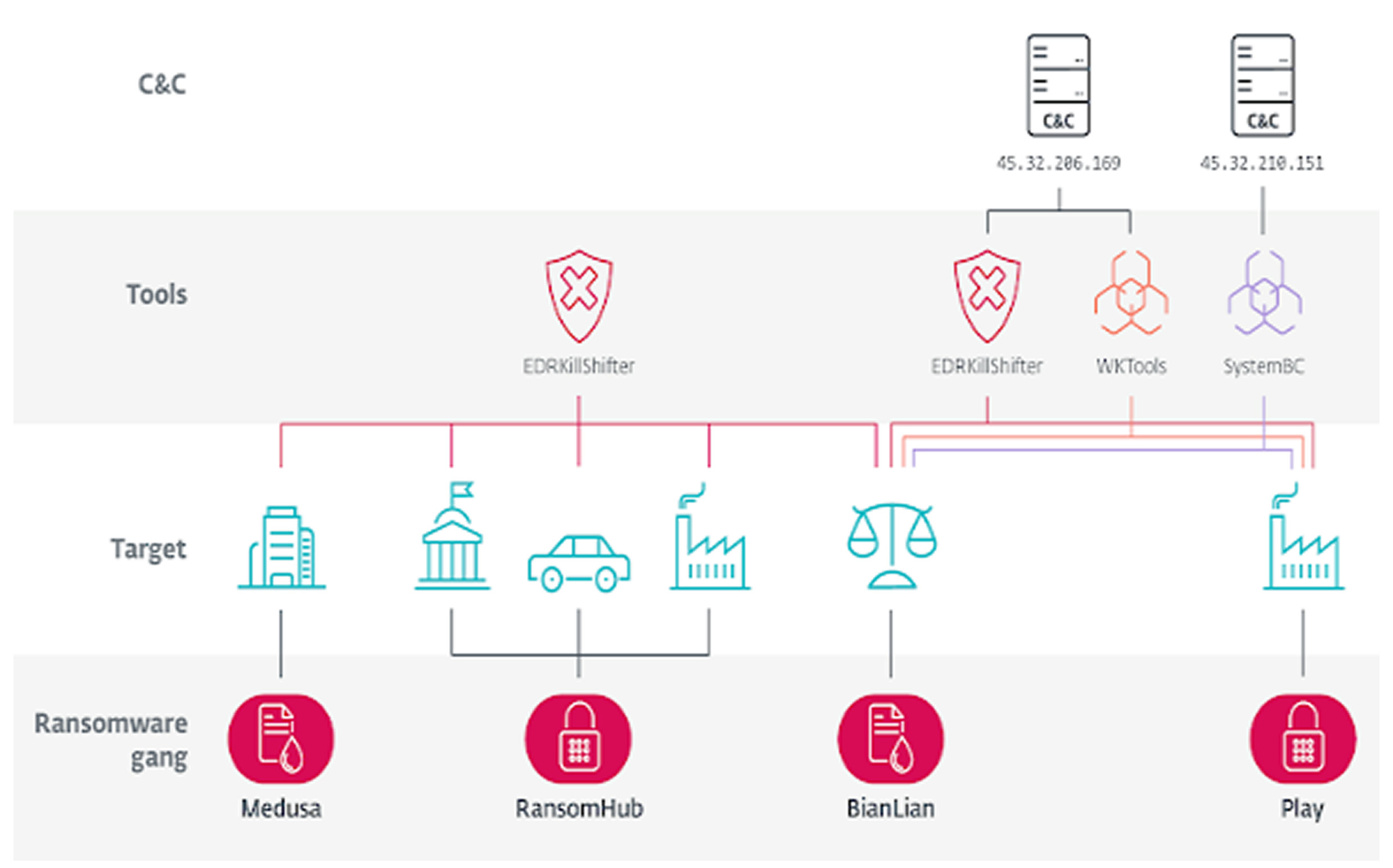
Unusual Collaboration Between Ransomware Groups
What makes this situation unique is that RansomHub’s operators developed EDRKillShifter and provided it to their affiliates, yet it has also appeared in attacks linked to Medusa, BianLian, and Play. This is noteworthy because both Play and BianLian operate under a closed Ransomware-as-a-Service model, meaning they do not actively recruit new affiliates and typically work with trusted long-term partners.
ESET researchers suspect that trusted members of Play and BianLian have been working with rival groups, including newer ones like RansomHub. They have likely been repurposing RansomHub’s tools for their own attacks. This is unusual because closed ransomware groups typically rely on a consistent set of core tools rather than adopting external software.
Investigators believe that these attacks may be linked to a single threat actor, referred to as QuadSwitcher. This individual appears to be closely associated with Play, as their attack techniques closely resemble those used in Play-related intrusions.
Other Cybercriminals Using EDRKillShifter
Another ransomware affiliate, known as CosmicBeetle, has also been found using EDRKillShifter in attacks involving RansomHub and fake LockBit ransomware incidents. The increased use of BYOVD tactics to deploy EDR killers highlights a growing trend among cybercriminals.
In previous cases, the ransomware group Embargo used a similar tool called MS4Killer to disable security defenses. More recently, the Medusa ransomware group has been linked to a custom malicious driver named ABYSSWORKER, which serves a similar purpose.
Preventing EDR Killers from Being Deployed
Cybersecurity experts emphasize that attackers need administrative privileges to deploy EDR killers. Therefore, organizations should focus on detecting and mitigating threats before cybercriminals reach this stage.
To strengthen security, businesses and corporate environments should enable detection for potentially unsafe applications. This can prevent vulnerable drivers from being installed and stop attackers from disabling endpoint protection solutions.


