Cybersecurity experts are raising concerns over an ongoing campaign that spreads fake cryptocurrency trading apps to deliver a compiled V8 JavaScript (JSC) malware known as JSCEAL. This malware is capable of stealing credentials and wallet data.
According to Check Point, attackers use thousands of malicious Facebook ads to lure users to fraudulent websites that prompt them to download fake trading apps. These ads are promoted through either hacked or newly created accounts.
Check Point's analysis reveals that the attackers break the installer into multiple parts and shift much of the functionality into JavaScript files embedded within the compromised websites. This modular and layered infection strategy allows them to adapt their methods and tools throughout the campaign.
Parts of this operation were previously documented by Microsoft in April 2025 and more recently by WithSecure, which tracks the campaign under the name WEEVILPROXY. WithSecure believes the campaign has been active since March 2024.
The infection process uses advanced anti-analysis techniques that rely on script-based fingerprinting before delivering the JSCEAL payload. The attackers also implemented a method requiring both the fake website and installer to run together, complicating detection and analysis.
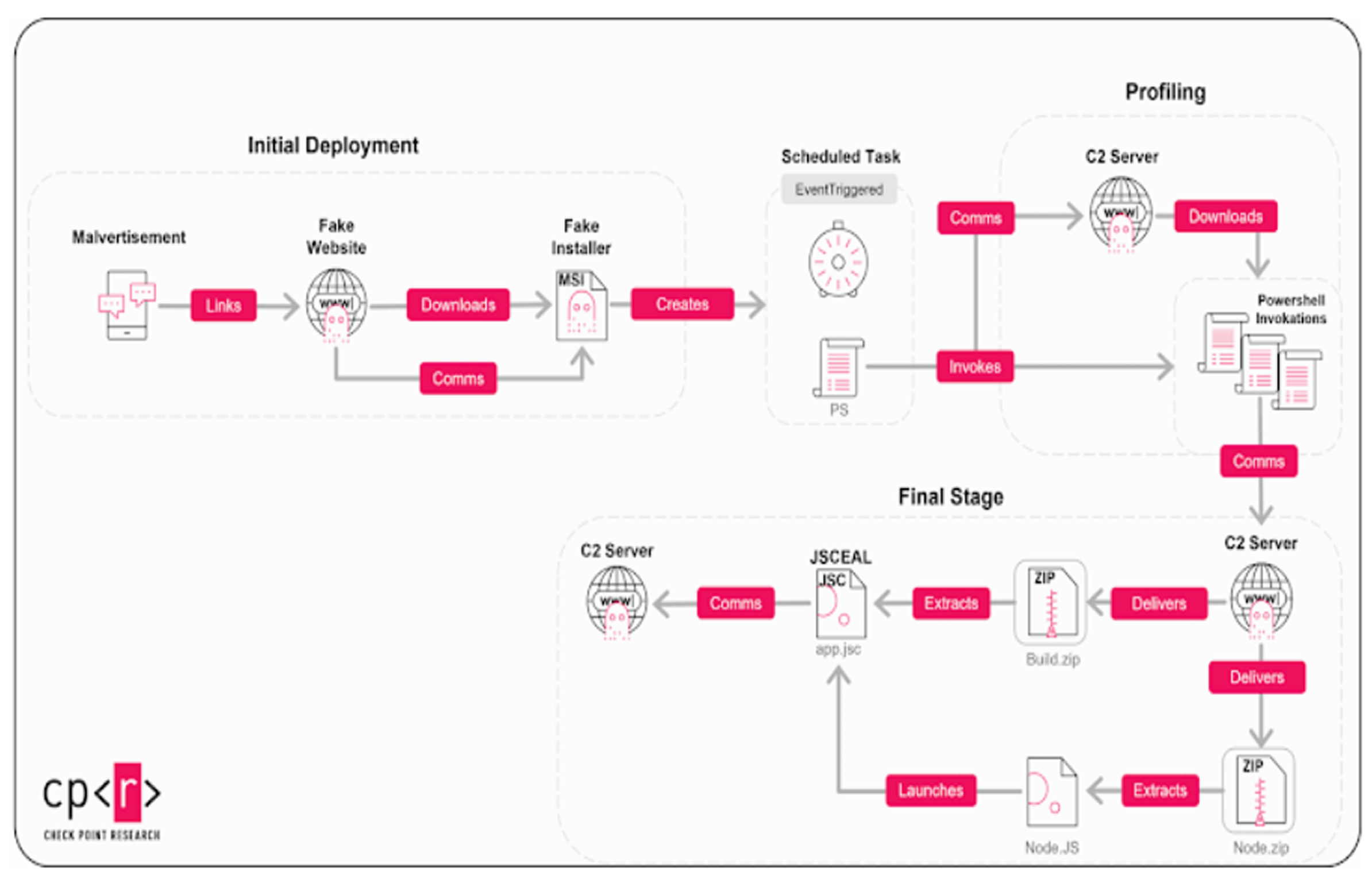
Clicking the Facebook ad starts a redirection process that leads users to a spoofed landing page mimicking services like TradingView. If the visitor's IP address or referral source does not meet certain conditions, a decoy site is shown instead. The spoofed site contains JavaScript code that communicates with a local server on port 30303 and includes scripts that track the installation process and initiate POST requests.
The installer from the fake site extracts several DLL files and sets up HTTP listeners on localhost:30303 to handle requests from the site. If any element fails, the infection cannot continue. To avoid suspicion, the installer opens a webview using msedge_proxy.exe and redirects the victim to the real website of the app.
The DLL files interpret POST requests, gather system data, and begin fingerprinting. The stolen data is then sent to the attacker via a PowerShell backdoor as a JSON file. If the victim is seen as a high-value target, the attack progresses to executing the JSCEAL malware using Node.js.
JSCEAL connects to a remote server for further commands and sets up a local proxy to hijack web traffic. It injects malicious scripts into financial and crypto-related websites to steal credentials instantly. The malware can also collect browser cookies, saved passwords, Telegram data, screenshots, and keystrokes, and perform adversary-in-the-middle attacks and crypto wallet manipulation. It also functions as a remote access trojan.
Check Point describes the malware as highly advanced, giving attackers full control of a victim's machine while remaining hidden from standard security tools. The use of compiled and heavily obfuscated JSC files helps the malware bypass defenses and makes it much harder to analyze.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.