Cybersecurity researchers have identified a new variant of the well-known malware loader Matanbuchus, which includes major updates aimed at improving stealth and avoiding detection.
Matanbuchus is a malware-as-a-service (MaaS) tool used to deliver follow-up payloads such as Cobalt Strike beacons and ransomware. Originally advertised in February 2021 on Russian-language cybercrime forums for $2,500 per rental, it has since been distributed through deceptive methods like ClickFix-style lures. These tactics target users who visit legitimate but compromised websites.
Over time, Matanbuchus has expanded its delivery methods to include phishing emails linked to malicious Google Drive files, drive-by downloads, booby-trapped MSI installers, and malvertising campaigns. It has been used to deploy secondary malware like DanaBot, QakBot, and Cobalt Strike, all of which are commonly associated with ransomware activity.
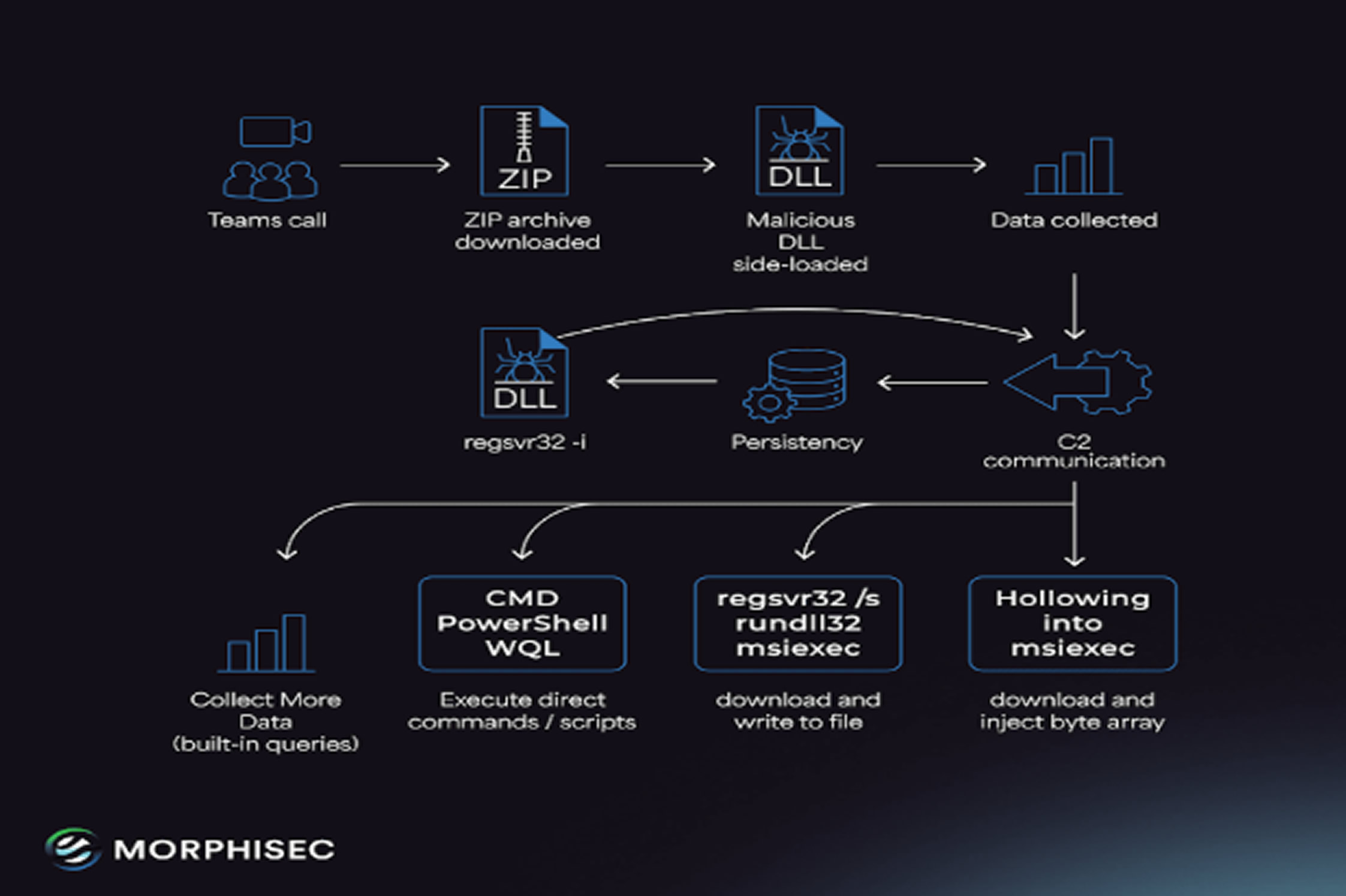
The latest version, known as Matanbuchus 3.0, introduces several upgrades. These include more sophisticated communication techniques, in-memory execution, stronger obfuscation, reverse shell capabilities for both CMD and PowerShell, and support for executing DLLs, EXEs, and shellcode payloads. According to Morphisec, the malware was recently observed in an attack targeting a company through fake IT support calls on Microsoft Teams. Attackers tricked employees into launching Quick Assist for remote access, followed by the execution of a PowerShell script that delivered Matanbuchus.
Similar social engineering methods have been seen in attacks by threat actors tied to the Black Basta ransomware group.
According to Morphisec CTO Michael Gorelik, victims are often carefully selected and convinced to run a script that downloads an archive file. This archive contains a renamed Notepad++ updater (GUP), a modified configuration XML file, and a malicious DLL that serves as the Matanbuchus loader.
The new version is being marketed for $10,000 per month for the HTTPS variant and $15,000 for the DNS version. Once installed, the malware gathers system details and scans running processes to identify security tools and check if it has administrative privileges. It then sends this information to a command-and-control (C2) server, which responds with further payloads in MSI or portable executable format. Persistence is achieved through a scheduled task.
Gorelik explained that the developers use advanced techniques to create this scheduled task, including shellcode injection and use of COM objects. The shellcode performs simple API resolution but implements a complex COM-based task scheduling method using ITaskService manipulation.
The loader can also receive remote commands from the C2 server to collect active processes, services, and installed applications. Gorelik described Matanbuchus 3.0 as a highly advanced threat. Its features include stealthy communication, in-memory execution, stronger obfuscation, support for WQL queries, and reverse shells for CMD and PowerShell. The loader’s capability to run commands like regsvr32, rundll32, msiexec, and process hollowing adds to its flexibility, posing a serious risk to compromised environments.
As malware-as-a-service continues to evolve, Matanbuchus 3.0 exemplifies a growing class of stealth-focused loaders. These threats increasingly rely on techniques like LOLBins, COM object hijacking, and PowerShell staging to avoid detection. Security researchers are now tracking these tools more closely as part of efforts to manage attack surfaces. Many of them are being linked to the exploitation of enterprise collaboration platforms such as Microsoft Teams and Zoom.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



