Cybersecurity experts are raising alarms over a wave of phishing attacks that mimic well-known brands to lure victims into calling phone numbers operated by attackers.
This tactic, called Telephone-Oriented Attack Delivery (TOAD), also known as callback phishing, uses PDF attachments in emails to convince recipients to dial a number controlled by cybercriminals. Cisco Talos researcher Omid Mirzaei highlighted this trend in a recent report shared.
Between May 5 and June 5, 2025, Microsoft and DocuSign emerged as the most impersonated brands in such attacks, followed by NortonLifeLock, PayPal, and Geek Squad. These phishing emails often include fake invoices or urgent notices disguised with recognizable branding. Some incorporate QR codes embedded in PDF annotations or sticky notes that link to phishing sites, including fake Microsoft login pages.
In callback phishing, the victim is urged to call a support number, where a scammer impersonates a company representative and guides them into giving up credentials or installing remote access tools. Attackers often use hold music, scripts, and spoofed numbers to make the call seem authentic. These methods have helped install malware, banking trojans, and remote access software on victims’ devices.
The FBI warned in May 2025 about callback phishing linked to a financially motivated group known as Luna Moth. These attackers posed as IT personnel to trick victims into installing malware.
Cisco Talos noted that threat actors often use VoIP numbers to stay anonymous and reuse them across multiple scams. Some are active for up to four days, allowing prolonged phishing operations. “Brand impersonation remains one of the most effective social engineering techniques,” Cisco said, recommending brand detection tools to help prevent such attacks.
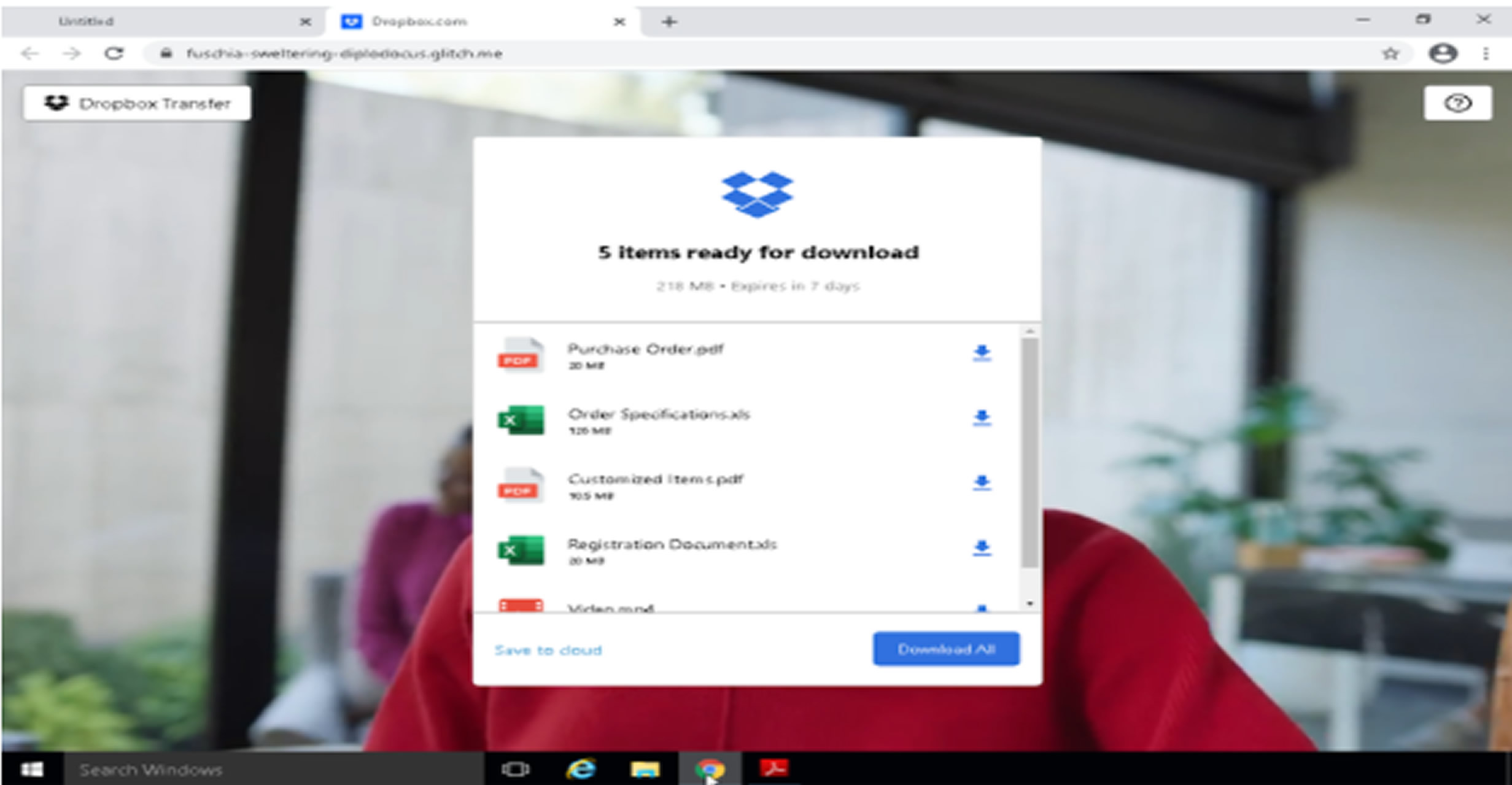
More recently, attackers have abused a Microsoft 365 feature called Direct Send, which allows messages to appear as if they’re coming from inside the target organization without requiring authentication. This technique has already been used against over 70 companies since May. These emails are harder to detect and can direct users to phishing pages or fake payment portals, depending on the scam.
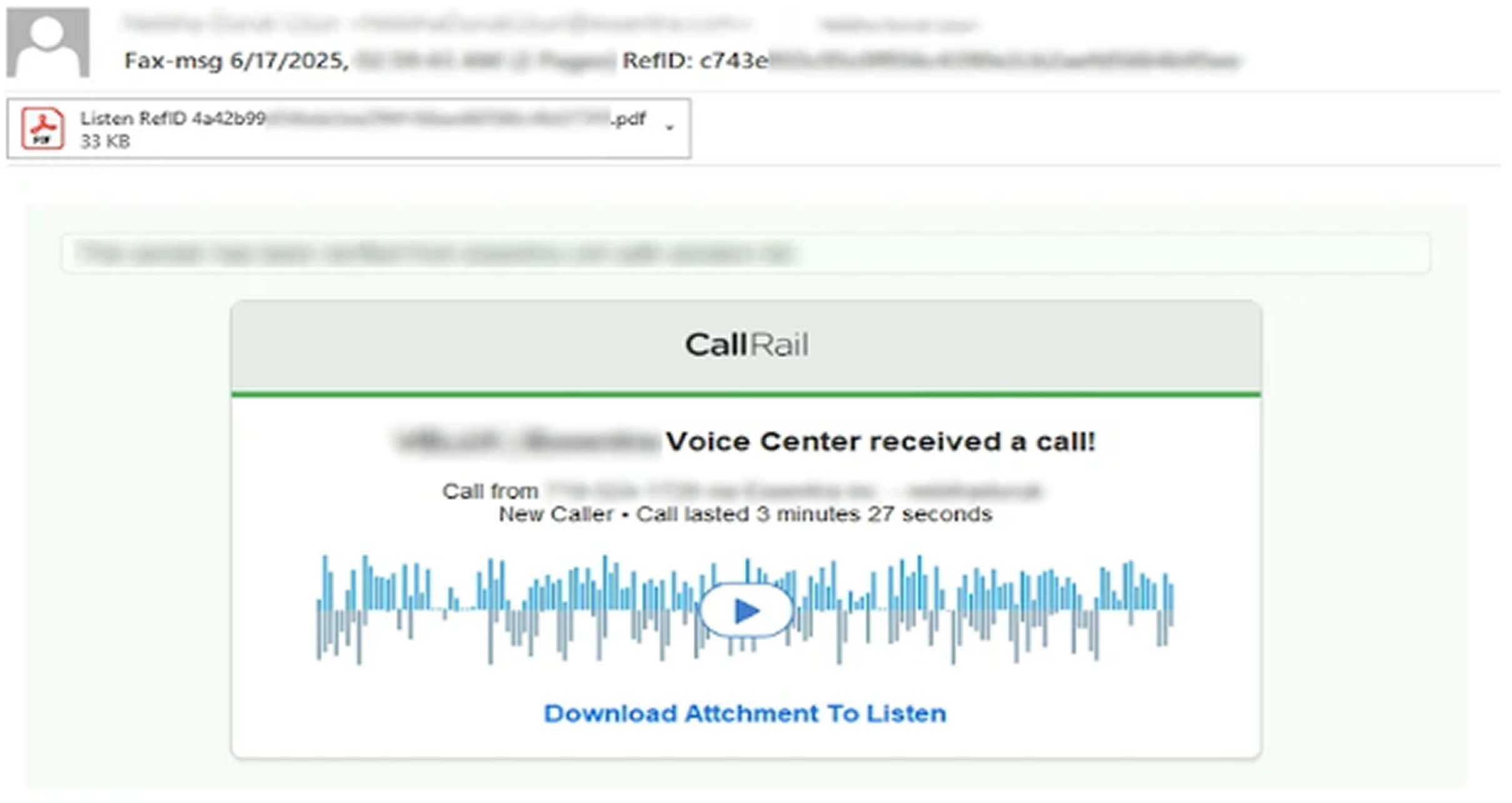
One phishing email sent on June 17 resembled a voicemail notification and carried a PDF attachment with a QR code linking to a fake Microsoft 365 login page. According to researcher Tom Barnea, Direct Send’s simplicity makes it attractive for attackers, especially since it bypasses many traditional filters.
In another twist, Netcraft found that when asked where to log in to various brand websites, large language models (LLMs) returned incorrect or even dangerous URLs in about a third of responses. Some of these domains were inactive or unregistered, making them easy targets for threat actors to exploit and impersonate brands.
Netcraft also observed attackers poisoning AI coding assistants like Cursor by uploading fake APIs to GitHub that redirect blockchain transactions to attacker wallets. These were promoted using fake but convincing GitHub accounts and blogs designed to be indexed by AI training tools.
Meanwhile, a service known as Hacklink is helping scammers inject malicious links into compromised reputable sites such as .gov and .edu domains. This manipulates search engine algorithms to rank phishing sites higher, often disguising the link preview to match legitimate search terms, a tactic that can severely damage brand reputation and user trust.
Altogether, these campaigns show that attackers are blending phone calls, phishing emails, QR codes, search engine manipulation, and AI tools to target individuals and organizations in increasingly sophisticated ways.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.