BladedFeline: An Iran-Aligned Threat Actor Targeting Kurdish and Iraqi Government Officials
ESET has attributed a recent series of cyberattacks against Kurdish and Iraqi government officials in early 2024 to BladedFeline, an Iran-aligned threat group assessed to be a sub-cluster of the well-known Iranian nation-state actor OilRig. Active since September 2017, BladedFeline has consistently targeted entities within the Kurdistan Regional Government (KRG), the Iraqi government, and a regional telecommunications provider in Uzbekistan.
The group employs a diverse arsenal of custom-developed malware and tools designed to maintain and expand unauthorized access within these organizations. Notable implants include:
- Shahmaran, a backdoor facilitating remote command execution and file management;
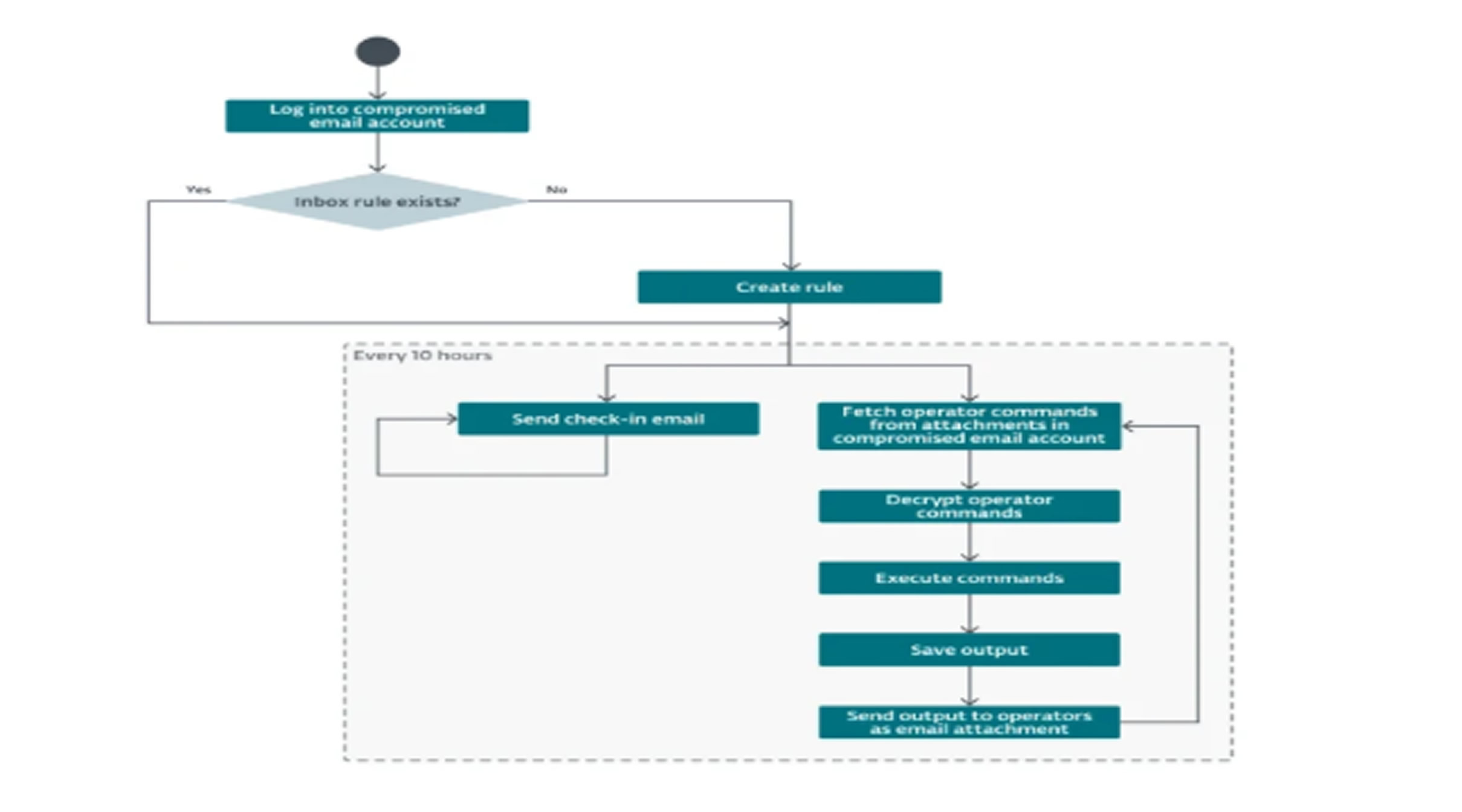
- Whisper (also known as Veaty), a C#/.NET backdoor that communicates via compromised Microsoft Exchange webmail accounts;
- Spearal and its successor Optimizer, .NET backdoors utilizing DNS tunneling for command-and-control communications;
- Slippery Snakelet, a Python-based implant with capabilities for command execution and file transfer;
- PrimeCache, a malicious IIS module that intercepts HTTP requests with specific cookie headers to execute commands and exfiltrate data.
BladedFeline is suspected to gain initial access through exploitation of vulnerabilities in internet-facing applications, followed by deployment of the Flog web shell to establish persistent access. The group also utilizes tunneling tools such as Laret and Pinar to maintain footholds within compromised networks.
Strategically, BladedFeline focuses on cyber espionage efforts to gather diplomatic and financial intelligence from high-level officials in the KRG and Iraqi government. This aligns with Iran’s broader regional objectives to monitor and potentially influence Kurdish-Western diplomatic relations and to counter Western presence and influence in Iraq following the U.S. invasion and occupation.
Attribution to OilRig is supported by shared tooling and techniques observed in BladedFeline’s operations, including malware components previously identified on compromised KRG systems in 2017 and 2018. Additional corroboration comes from the discovery of a malicious implant dubbed Hawking Listener, uploaded to VirusTotal in March 2024 by the same actors responsible for deploying Flog.
In conclusion, BladedFeline represents a persistent and evolving cyber threat actor advancing Iranian strategic interests through sophisticated cyber espionage campaigns targeting key governmental and diplomatic entities within Iraq and the Kurdistan region.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



