Two well-known threat actor groups, codenamed Head Mare and Twelve, appear to have joined forces to launch cyberattacks against Russian organizations,
According to new research from Kaspersky.
Kaspersky’s findings suggest a close collaboration between the two groups, as Head Mare has been observed using tools previously associated with Twelve. Additionally, command-and-control (C2) servers that were exclusively linked to Twelve are now being leveraged by Head Mare in its recent operations.
Both groups were initially documented by Kaspersky in September 2024. Head Mare previously exploited a now-patched vulnerability in WinRAR (CVE-2023-38831) to gain initial access, deploy malware, and in some cases, install ransomware variants like LockBit for Windows and Babuk for Linux (ESXi) to demand ransoms. Meanwhile, Twelve has been responsible for highly destructive attacks, using publicly available tools to encrypt victims' data and deploying wipers to permanently destroy their infrastructure, making recovery impossible.
Kaspersky’s latest analysis highlights two new tools used by Head Mare: CobInt, a backdoor previously linked to ExCobalt and Crypt Ghouls in attacks on Russian companies, and PhantomJitter, a custom implant installed on servers for remote command execution. Notably, CobInt has also been seen in Twelve’s attacks, further suggesting tactical connections between different threat actors targeting Russia.
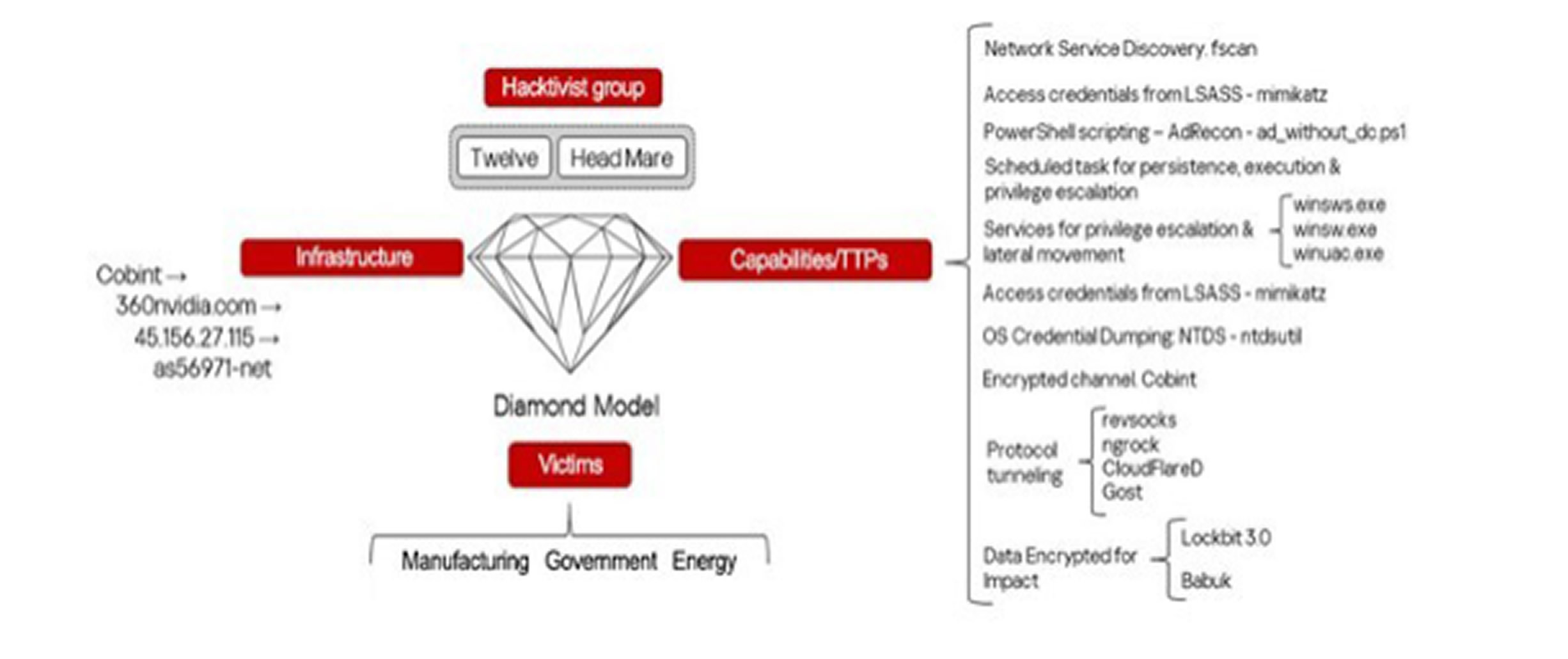
Head Mare has exploited multiple entry points to breach networks, including vulnerabilities in Microsoft Exchange Server (such as CVE-2021-26855, also known as ProxyLogon). It has also used phishing emails with malicious attachments and compromised contractors’ networks—a technique known as a trusted relationship attack—to infiltrate victims’ systems. Kaspersky found that ProxyLogon was used to execute commands that downloaded and launched CobInt on targeted servers. Unlike previous methods that relied on scheduled tasks for persistence, the attackers have shifted to creating privileged local user accounts on business automation servers, allowing them to connect via RDP for interactive tool execution.
To evade detection, the threat actors disguise their malicious payloads with names resembling legitimate system files (e.g., calc.exe or winuac.exe). They also erase event logs to remove traces of their activity and use proxy and tunneling tools like Gost and Cloudflared to obscure network traffic.
Additionally, Head Mare and Twelve employ a variety of reconnaissance and exploitation tools, including:
- System reconnaissance: quser.exe, tasklist.exe, netstat.exe
- Network scanning: fscan, SoftPerfect Network Scanner
- Active Directory enumeration: ADRecon
- Credential theft: Mimikatz, secretsdump, ProcDump
- Lateral movement: RDP, mRemoteNG, smbexec, wmiexec, PAExec, PsExec
- Data exfiltration: Rclone
The final stage of their attacks typically involves deploying LockBit 3.0 and Babuk ransomware on compromised hosts, followed by ransom notes instructing victims to contact the attackers via Telegram for file decryption.
Kaspersky warns that Head Mare is actively expanding its techniques and toolset. In recent attacks, the group has gained initial access not only through phishing emails but also by compromising third-party contractors. This collaboration with Twelve suggests a strategic effort to target both state-controlled and private companies in Russia.
Meanwhile, BI.ZONE has linked the North Korea-affiliated threat actor ScarCruft (APT37, Reaper, Ricochet Chollima, Squid Werewolf) to a phishing campaign in December 2024, which delivered a malware loader capable of deploying an unknown payload from a remote server.
BI.ZONE also identified similarities between ScarCruft’s recent activity and a campaign documented by Securonix in October 2024, called SHROUDED#SLEEP, which led to the deployment of the VeilShell backdoor in attacks on Cambodia and other Southeast Asian nations.
Additionally, BI.ZONE has reported ongoing cyberattacks by Bloody Wolf, which has been using NetSupport RAT to compromise over 400 systems in Kazakhstan and Russia, marking a shift from its previous use of STRRAT malware.
Found this article interesting? Follow us on X(Twitter) and Instagram to read more exclusive content we post.


