Critical Linux Kernel Vulnerability CVE-2024-53141 Enables Privilege Escalation to Root
A newly identified high-severity vulnerability, CVE-2024-53141, has been discovered in the Linux kernel's IP sets framework, posing a serious security risk by allowing local attackers to escalate privileges and potentially execute code as root.
With a CVSS score of 7.8, this vulnerability—uncovered by security researchers st424204 and d4em0n—specifically affects the bitmap:ip set type within the netfilter subsystem.
Root Cause and Exploitation Mechanics
The flaw arises due to improper handling of the IPSET_ATTR_CIDR attribute when the IPSET_ATTR_IP_TO field is missing. As per an advisory from Ubuntu, this results in incorrect range validation for IP addresses, enabling malicious manipulation.
The vulnerability allows attackers to perform:
- Out-of-bounds (OOB) writes to the kernel heap
- Arbitrary memory manipulation
- Conversion of OOB conditions into use-after-free (UAF) scenarios
- Bypassing Kernel Address Space Layout Randomization (KASLR)
- Hijacking kernel control flow to execute attacker-supplied code
The vulnerability lies in the bitmap_ip implementation (ip_set_bitmap_ip.c), particularly in functions like ip_to_id, which can return values outside safe memory bounds. The proof-of-concept (PoC) exploit demonstrates advanced primitives such as:
- Heap address leaks via the ip_set_init_comment extension
- Arbitrary OOB writes using the ip_set_init_counter extension
- Use-after-free conditions via manipulated msg_msgseg structures
- KASLR bypass through heap spraying and object reallocation
- Instruction pointer (RIP) control and ROP chain execution, enabling complete compromise by overwriting the core_pattern variable and spawning a root shell
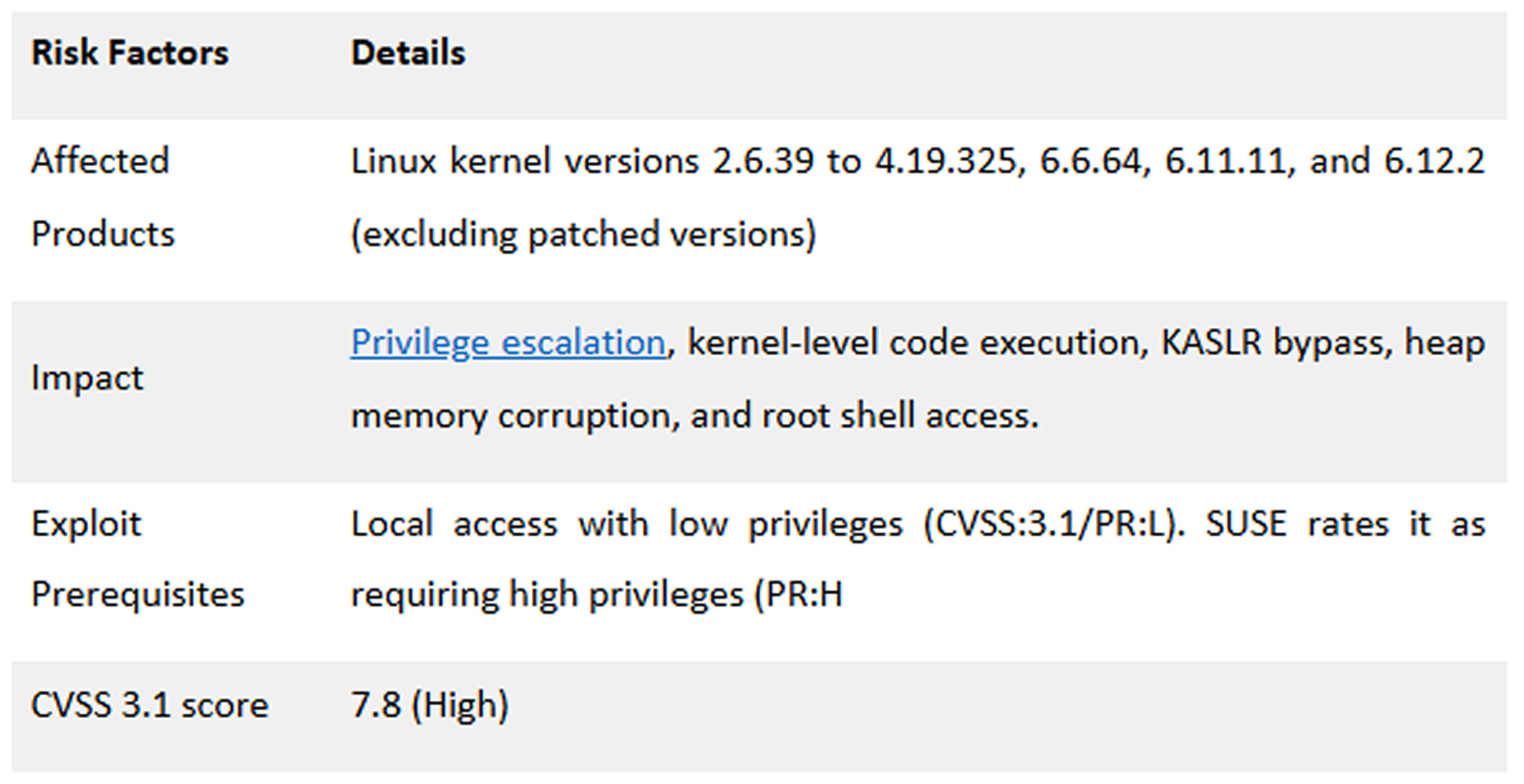
Affected Versions and Fixes
The vulnerability impacts kernel versions:
2.6.39 up to (but not including) 4.19.325, 6.6.64, 6.11.11, and 6.12.2
The PoC specifically targets Linux kernel 6.6.62
A patch has been released in the following kernel versions:
- 4.19.325
- 6.6.64
- 6.11.11
- 6.12.2 and above
The fix introduces proper input validation in the bitmap_ip_uadt function.
Urgent Recommendation
Security analysts emphasize the critical need for immediate patching, especially since exploit code is publicly available, heightening the risk of widespread attacks.
“This vulnerability offers a complete exploitation path—from heap manipulation to full kernel-level code execution,” the advisory warns.
System administrators should update vulnerable systems without delay to mitigate the risk of compromise.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


