Bluetooth Flaws in Widely Used Stack Could Let Hackers Remotely Access Millions of Cars
Researchers at PCA Cyber Security, formerly known as PCAutomotive, have identified critical vulnerabilities in a popular Bluetooth stack that could allow attackers to remotely compromise millions of vehicles.
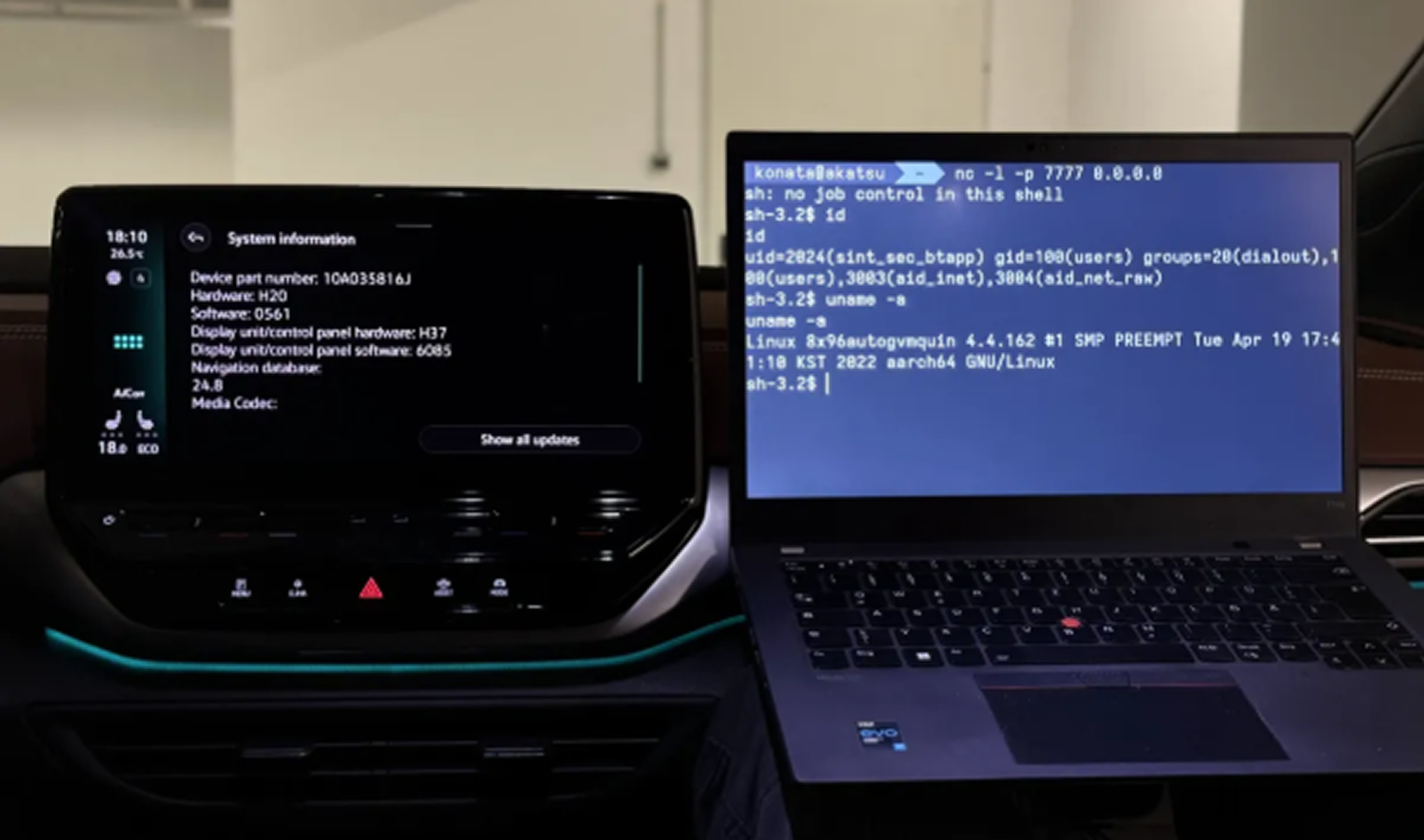
Their analysis focused on the BlueSDK Bluetooth framework developed by OpenSynergy. The team uncovered multiple flaws that could lead to remote code execution, security bypasses, and data leaks. These vulnerabilities can be combined in an attack scenario the researchers have named PerfektBlue.
PerfektBlue: Remote Exploitation and Risk to Vehicle Functions
Using the PerfektBlue method, PCA Cyber Security demonstrated how an attacker could remotely infiltrate a vehicle’s infotainment system. Once access is gained, the attacker could monitor the car’s location, record audio from inside the cabin, and access private data such as the user's phonebook.
Although not yet demonstrated in this specific case, the researchers noted that lateral movement from the infotainment system to more critical vehicle systems could be possible. Past research has shown that once inside a car’s internal network, hackers might be able to manipulate functions such as the horn, steering, or windshield wipers.
PerfektBlue was successfully demonstrated on newer infotainment systems found in vehicles from Mercedes-Benz, Skoda, and Volkswagen. Additionally, an unnamed original equipment manufacturer (OEM) was informed of the vulnerabilities only recently.
Widespread Impact Beyond Vehicles
BlueSDK is used in a wide range of devices beyond automobiles. These include smartphones and portable electronics produced by several leading technology brands, putting an even larger number of users and devices at risk.
The attack can be carried out if the hacker is within Bluetooth range and able to pair their laptop with the vehicle’s infotainment system. In some scenarios, no user interaction is needed for pairing. In others, the attack might require the user to confirm a pairing request. According to PCA Cyber Security, the PerfektBlue attack may need only a single click to execute.
Disclosure, CVEs, and Patches
The vulnerabilities were disclosed to OpenSynergy in May 2024 and assigned the identifiers CVE-2024-45434, CVE-2024-45431, CVE-2024-45432, and CVE-2024-45433. OpenSynergy began issuing patches to its customers in September 2024. PCA Cyber Security delayed public disclosure to allow enough time for the updates to be widely implemented.
Earlier in the year, the same research firm disclosed similar Bluetooth-related vulnerabilities that could be used to remotely compromise a Nissan Leaf electric vehicle. Those findings also highlighted serious risks, including spying and unauthorized control of key functions.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



