New Phishing-as-a-Service Platform Uses DNS MX Records for Targeted Attacks
Cybersecurity researchers have identified a new phishing-as-a-service (PhaaS) platform that exploits Domain Name System (DNS) mail exchange (MX) records to serve customized fake login pages impersonating 114 well-known brands.
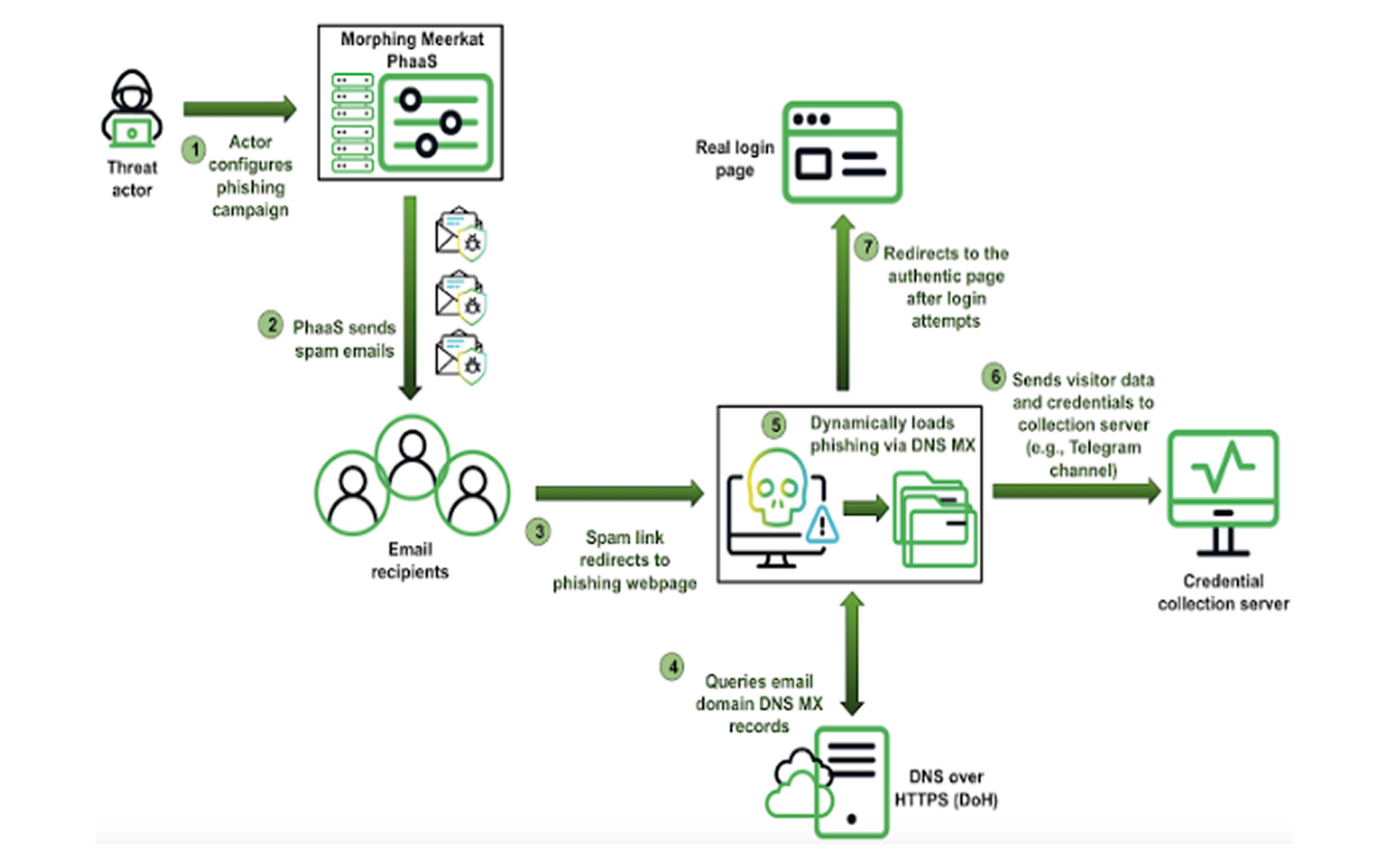
The DNS intelligence firm Infoblox is tracking this threat under the name Morphing Meerkat, which is responsible for phishing campaigns that use advanced techniques to evade security detection and target users globally.
How Morphing Meerkat Operates
Morphing Meerkat’s phishing campaigns use a variety of deceptive techniques, including:
- Exploiting open redirects on advertising technology (adtech) infrastructure to trick users into visiting phishing sites.
- Compromising legitimate domains to distribute phishing content.
- Using Telegram to store and distribute stolen credentials.
One such campaign was documented by Forcepoint in July twenty twenty-four, where phishing emails contained links to a supposed shared document. When clicked, the link directed victims to a fake login page hosted on Cloudflare R2, designed to steal login credentials and exfiltrate them via Telegram.
A Sophisticated Global Operation
Morphing Meerkat has sent thousands of spam emails, often using compromised WordPress sites and open redirect vulnerabilities in platforms like Google-owned DoubleClick to bypass security filters.
To maximize its reach, the phishing platform can automatically translate phishing pages into more than a dozen languages, including English, Korean, Spanish, Russian, German, Chinese, and Japanese, making it highly effective for targeting users worldwide.
Advanced Evasion and Anti-Analysis Techniques
- The phishing landing pages employ several security evasion tactics:
- Obfuscation and code inflation to make detection and analysis difficult.
Blocking right-click functionality and disabling keyboard shortcuts such as:
- Ctrl + S (Save the page as HTML)
- Ctrl + U (View page source code)
Using DNS MX Records for Targeted Phishing
What makes Morphing Meerkat particularly dangerous is its use of DNS MX records to dynamically determine the victim’s email provider.
When a user clicks a phishing link, the attack kit checks the MX record associated with their email (e.g., Gmail, Microsoft Outlook, or Yahoo!) and then serves a fake login page that exactly matches the victim’s email service provider.
If the MX record cannot be identified, the attack defaults to a generic Roundcube login page.
Why This Method is Effective
By displaying a phishing page that perfectly matches the victim’s actual email provider, Morphing Meerkat makes the attack more convincing and difficult to detect.
Infoblox researchers explain:
"This attack method benefits cybercriminals by allowing them to deliver highly targeted phishing pages that match the victim’s expectations. Since the landing page design aligns with the email message, victims are more likely to trust the site and enter their credentials."
Morphing Meerkat’s ability to dynamically adapt phishing pages, evade security measures, and target victims worldwide makes it a serious cybersecurity threat. Organizations and individuals must remain vigilant against phishing emails and implement multi-factor authentication (MFA) to prevent unauthorized access.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


