A China-linked hacking group known as Mustang Panda has launched a fresh cyber espionage campaign targeting the Tibetan community, according to IBM’s X-Force team.
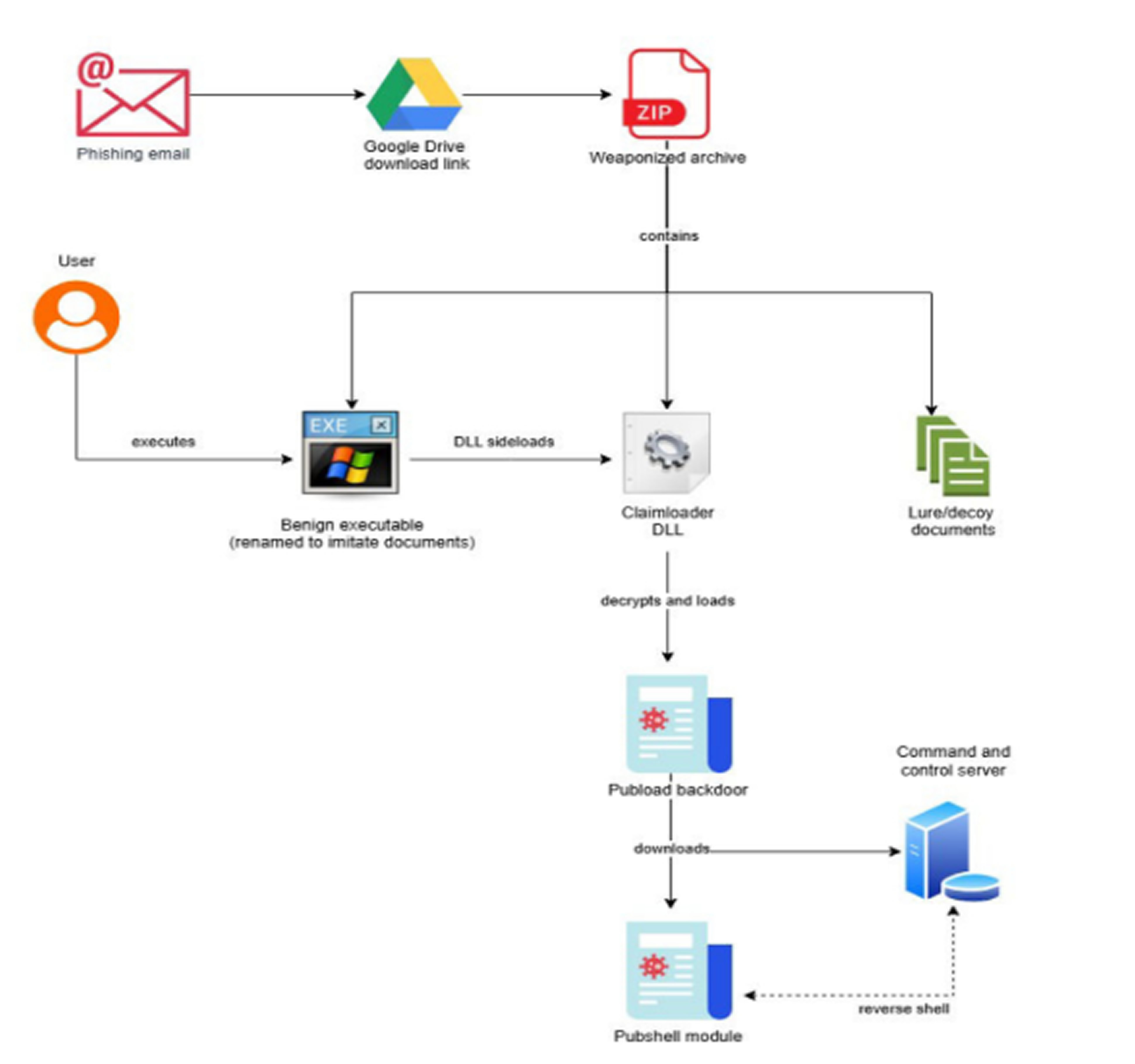
The attacks, detected earlier this month, used spear-phishing emails that referenced Tibet-related themes such as the 9th World Parliamentarians’ Convention on Tibet, China’s education policies in the region, and a newly released book by the 14th Dalai Lama. The campaign ultimately led to the deployment of Mustang Panda’s malware known as PUBLOAD. IBM tracks the group as Hive0154.
Victims received malicious archive files that included a harmless Word document, Tibetan articles, and photos from the WPCT. Hidden within these files was an executable disguised as a document. Once opened, the executable used DLL side-loading to run a malicious DLL dubbed Claimloader, which then deployed PUBLOAD. PUBLOAD contacts a remote server to download a second-stage payload called Pubshell.
According to researchers Golo Mühr and Joshua Chung, Pubshell is a lightweight backdoor that enables attackers to access infected machines through a reverse shell.
IBM notes that while it calls the custom loader “Claimloader” and the downloader “PUBLOAD,” other cybersecurity firms like Trend Micro and Team T5 use different naming conventions. Despite the variation in terminology, all firms agree that the malware chain is consistent with Mustang Panda’s past tactics.
This campaign follows recent Hive0154 activity targeting the U.S., Taiwan, Philippines, and Pakistan. Those attacks also relied on spear-phishing emails containing links to weaponized ZIP or RAR archives hosted on Google Drive. The payloads in those cases were TONESHELL in 2024 and PUBLOAD in more recent attacks.
Both Pubshell and TONESHELL function similarly by establishing reverse shells. However, Pubshell lacks some features found in TONESHELL, suggesting it may be a simplified or lightweight version.
In the attacks targeting Taiwan, the group also used a USB worm known as HIUPAN (or MISTCLOAK/U2DiskWatch) to spread Claimloader and PUBLOAD via removable drives.
IBM concluded that Hive0154 remains a capable and evolving threat actor, likely to continue targeting East Asian governments, militaries, and other high-profile entities. The use of USB worms, customized malware, and frequent updates underscores the group’s sophistication and persistence.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



