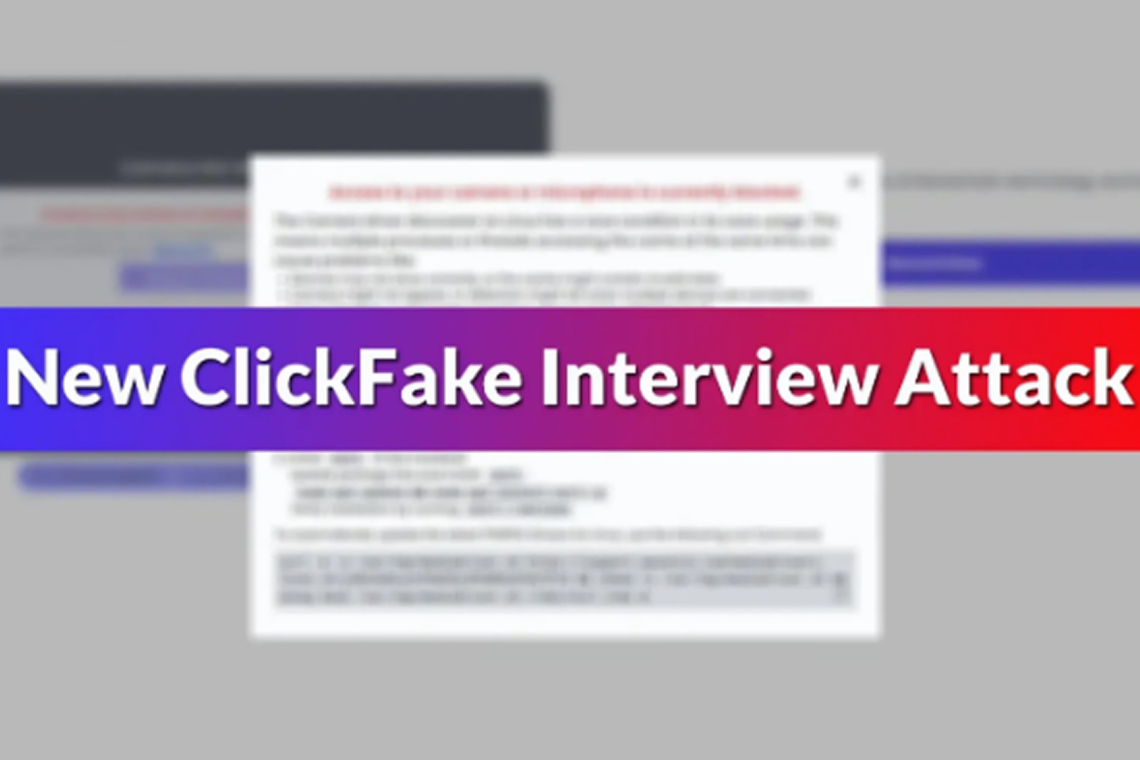
The Lazarus Group has revived its long-running recruitment scam under a new name, “ClickFake Interview,” using a newly registered domain, waventic[.]com.
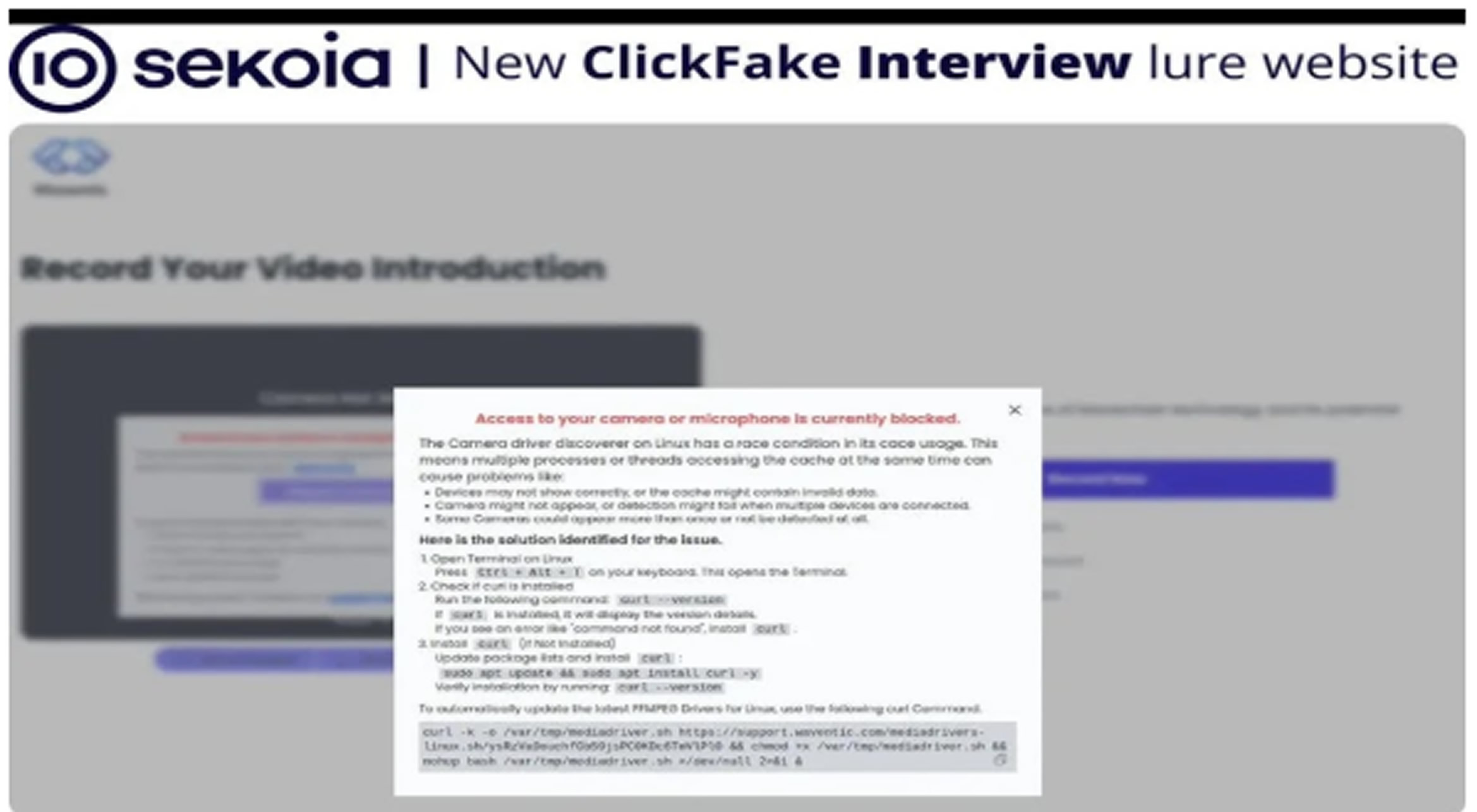
Victims are led through a polished JavaScript-based application form that concludes with a fake webcam “driver” download. Instead of a legitimate file, it installs the GolangGhost malware, designed to work across Windows, Linux, and macOS systems.
Researchers at Sekoia.io found that the group reused the earlier “ClickFix” website template seen in March 2025, but added geolocation filters and CAPTCHA to block basic scans. Since April, over 40 related domains have been launched, all redirecting users to apply[.]waventic[.]com, where the malware is served as a static Go binary. The attackers also use stolen LinkedIn profiles and Telegram channels to seem trustworthy, then rely on browser push notifications to trigger downloads.
Once installed, GolangGhost connects to preset command-and-control servers using encrypted WebSocket connections. It quickly sends back details like running processes and system metadata.
Initial reports show that finance and blockchain startups in Europe and Southeast Asia are among the early targets. Several macOS arm64 systems have already leaked sensitive credential data.
Because it is delivered as a self-contained Go executable, the malware often slips past antivirus systems that misidentify it as a harmless build.
Infection Details:
Upon execution, GolangGhost creates a user-specific copy in the autostart directory and adds persistence keys labeled “SysDrvX %RAND%”. Its small footprint is due to dynamic loading; most of its functions are pulled in later via base64-encoded gRPC modules. Security teams are advised to monitor WebSocket traffic to unknown domains and watch for Go executables launching shell processes from outside standard user folders.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.