A highly advanced phishing campaign known as “Scanception” has emerged as a major threat to enterprise security. It uses QR codes embedded in PDF attachments to bypass standard email security tools and steal user credentials.
This attack highlights a shift in social engineering tactics, taking advantage of the growing use of mobile devices for quick QR code scanning. The phishing operation unfolds through several stages, beginning with phishing emails that include PDF attachments designed to resemble official corporate documents. These attachments are often disguised as HR manuals or internal announcements, featuring realistic logos and company branding to gain users’ trust.
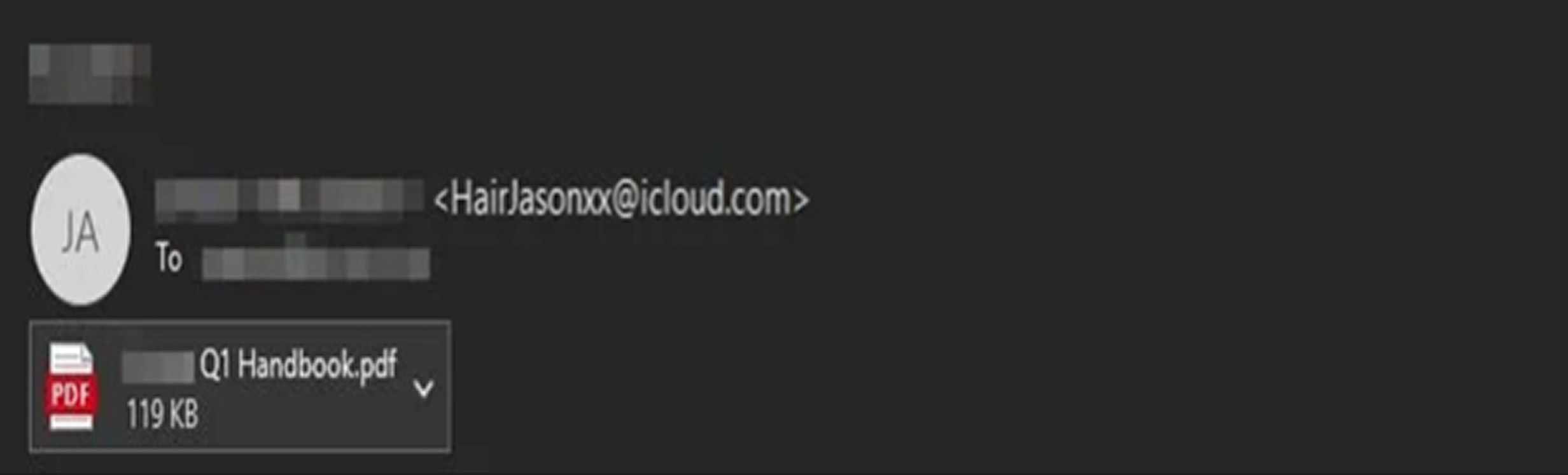
A key element of the attack is the placement of malicious QR codes on the final pages of multi-page PDFs. This tactic helps avoid detection by automated scanners, which typically review only the first few pages. Analysts at Cyble found more than 600 distinct phishing PDFs linked to the campaign within a three-month span. Nearly 80 percent of them had no detections on VirusTotal at the time of review.

The campaign’s complexity extends beyond the use of QR codes. When scanned, the QR codes route victims through trusted platforms like YouTube, Google, Bing, and Cisco before directing them to phishing sites.
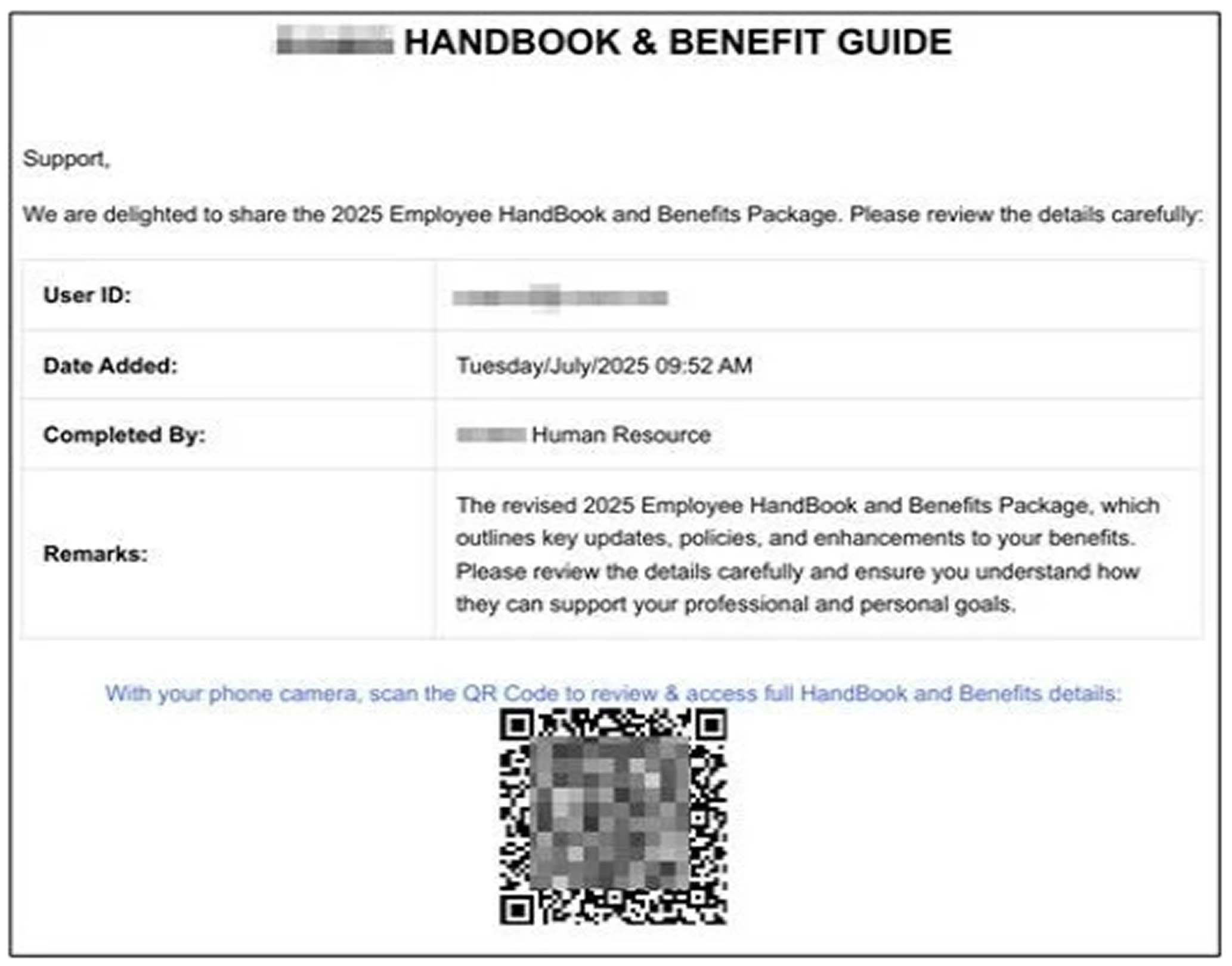
This redirection technique helps the campaign avoid detection by systems that rely on domain reputation.
Stealth Techniques and Credential Theft
Once users land on the fake Office 365 login page, the phishing site employs advanced methods to detect and block security research tools. It checks for tools such as Selenium, PhantomJS, and Burp Suite by running JavaScript functions repeatedly every 100 milliseconds. If any of these tools are identified, the site redirects users to a blank page to prevent further analysis.
To steal credentials, the attackers use an Adversary-in-the-Middle (AITM) method involving a function named sendAndReceive(), which connects in real time to attacker-controlled servers. The stolen data is sent using POST requests to dynamically generated endpoints, created with a randroute() function and a GitHub library called randexp.min.js. These randomized URLs make it harder for security software to identify known patterns.
One of the most alarming parts of this campaign is its ability to bypass multi-factor authentication. The system can prompt victims for additional credentials such as two-factor codes, email verifications, or SMS one-time passwords. This step-by-step process enables attackers to hijack user sessions and fully take over accounts, maintaining long-term access in Microsoft 365 environments and avoiding detection by relaying credentials to legitimate authentication services in real time.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



