O2, a major telecommunications provider in the United Kingdom had been leaking user location data for several months.
Any attacker could exploit this issue to access a user's location and other details simply by placing a call.
The now-fixed critical vulnerability affected O2’s Voice over LTE (VoLTE) technology.
Security researcher Daniel Williams discovered that O2 was sending “extremely detailed and long” Session Initiation Protocol (SIP) responses to callers. SIP is a digital protocol used to initiate and manage phone calls over the Internet.
Williams was initially interested in analyzing audio quality and supported voice codecs. Using a rooted Google Pixel 8 and the Network Signal Guru (NSG) app, he called another O2 customer with a 4G VoLTE-enabled phone and reviewed the network’s responses.
According to Williams, the SIP responses were unlike those from other networks. They included details about the SIP server used by O2, version numbers, and call-processing error messages generated by C++ services. Most concerning, however, were five headers that exposed sensitive user data.
Two of these revealed the International Mobile Subscriber Identity (IMSI) codes of the caller and the recipient. Two more contained their International Mobile Equipment Identity (IMEI) codes.
The final header exposed cellular network information, including the mobile network ID, Location Area Code (LAC), and the recipient's cell ID. This data identifies the exact mobile tower the user is connected to.
“This is bad,” Williams stated.
Using this information, he was able to determine that the recipient had a Google Pixel 9, was connected to the O2 network, and was using an O2 SIM card. Public databases like CellMapper made it possible to pinpoint the recipient’s general location based on cell tower data.
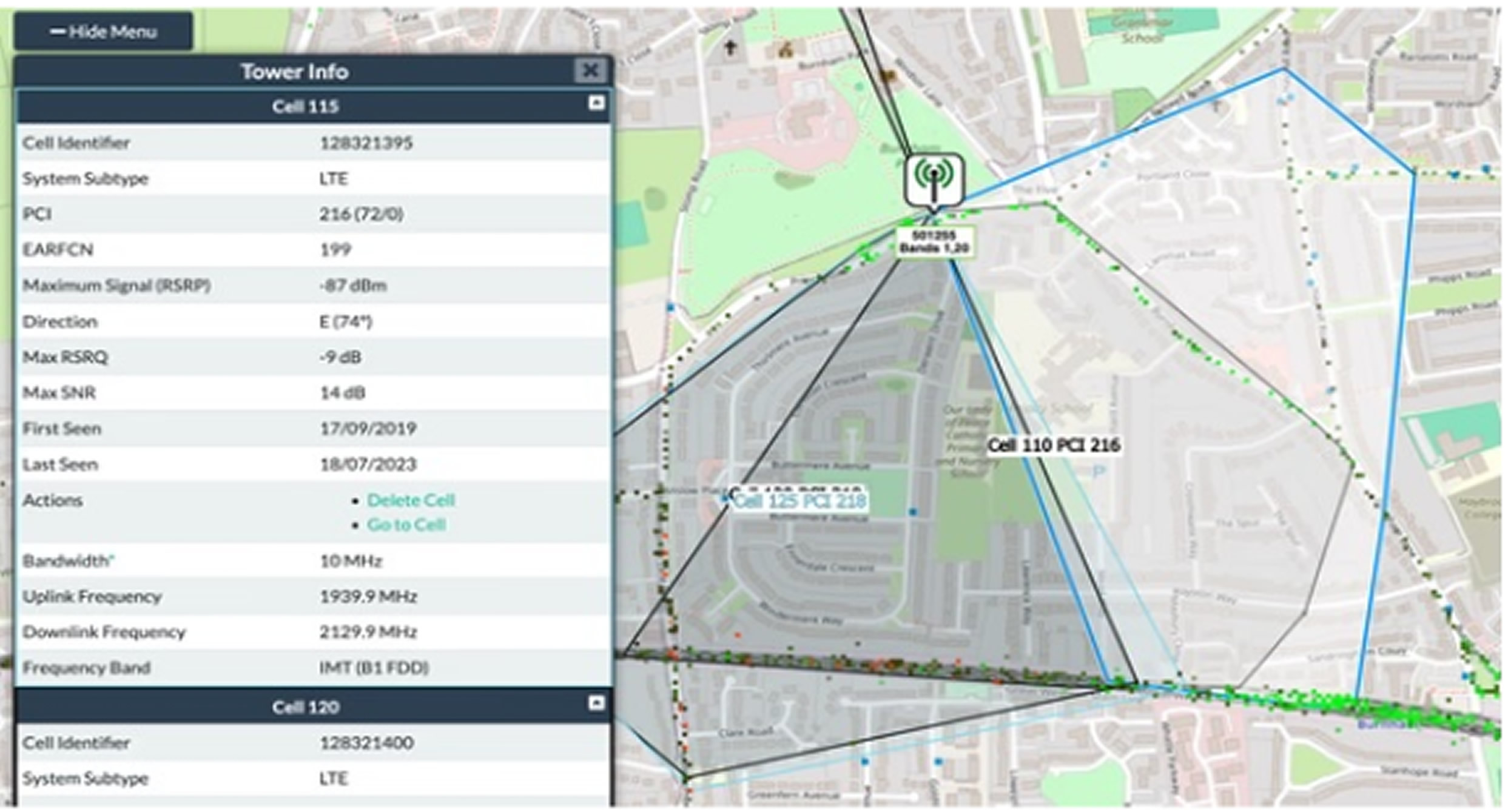
“In a city, this becomes an extremely accurate measure of location,” Williams explained. In densely populated areas, small cells attached to streetlamps or buildings often provide coverage for spaces as small as 100 square meters.
The flaw also exposed data from users who were roaming abroad.
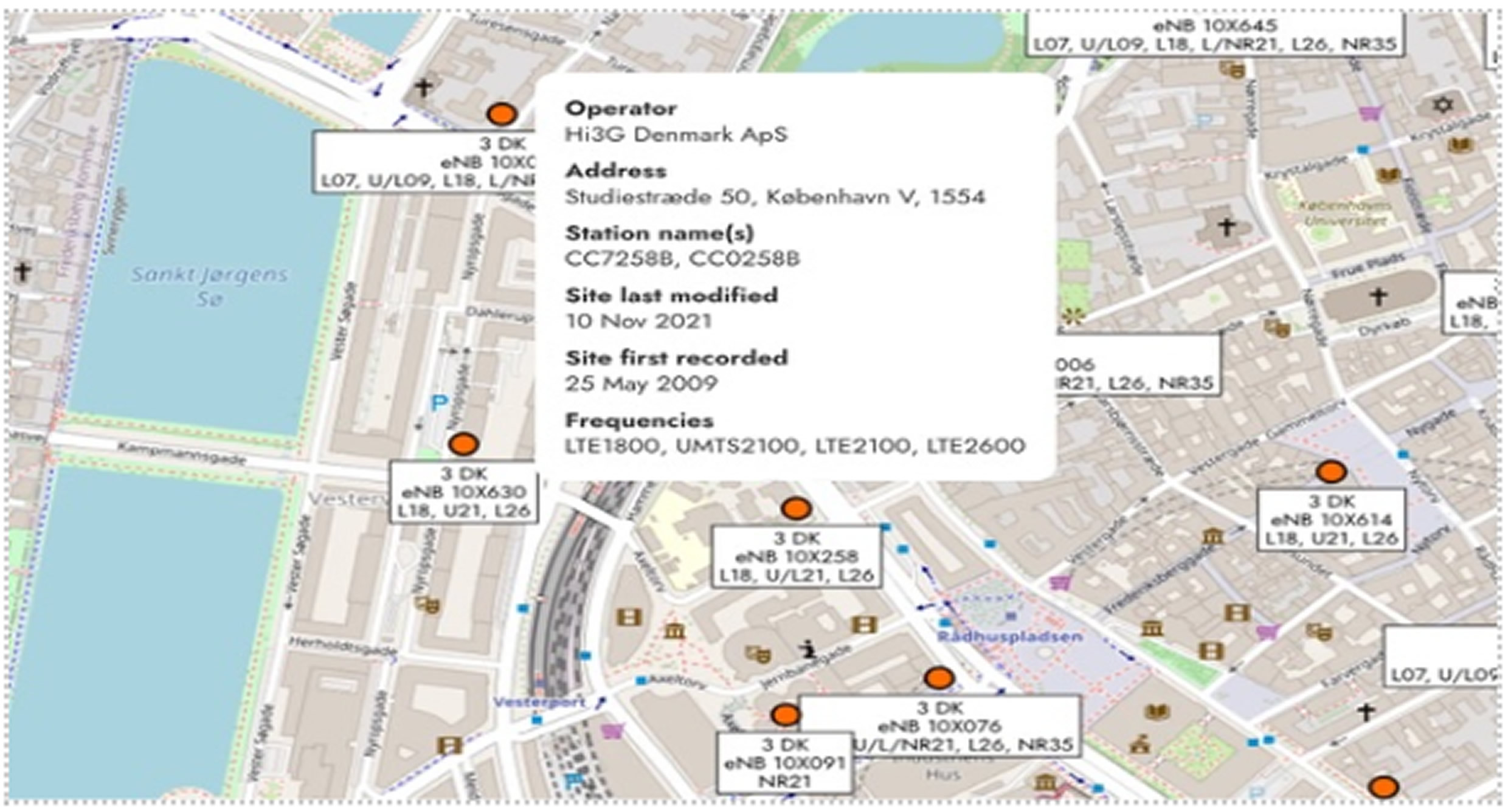
Williams demonstrated this by successfully identifying someone in the city center of Copenhagen, Denmark. He emphasized that the attack method was simple, as any device making a call could receive the data needed to locate the recipient.
He also expressed disappointment with O2’s lack of a clear channel for reporting security vulnerabilities. Williams attempted to notify O2 about the flaw on March 26 and 27, but received no response before publishing his findings on May 17.
Two days after publication, O2 contacted Williams and confirmed that the issue had been addressed. The researcher verified their claim and confirmed the vulnerability could no longer be exploited.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


