Lone Cybercriminal Behind 90+ Global Data Breaches Unmasked
A single cybercriminal posing as multiple hacker groups has been exposed as the mastermind behind over 90 data breaches worldwide over four years.
Operating under four different aliases—ALTDOS, DESORDEN, GHOSTR, and Omid16B—the attacker initially focused on Asian companies before expanding globally, leaving a trail of cyberattacks driven purely by financial motives. Their strategy involved infiltrating internet-facing Windows servers, specifically targeting databases containing personal information.
Using SQL injection tools like sqlmap, the hacker would scan for vulnerabilities and exploit them to gain unauthorized access to sensitive data. After breaching servers, they would extract valuable information and, in some cases, encrypt the data on compromised systems.
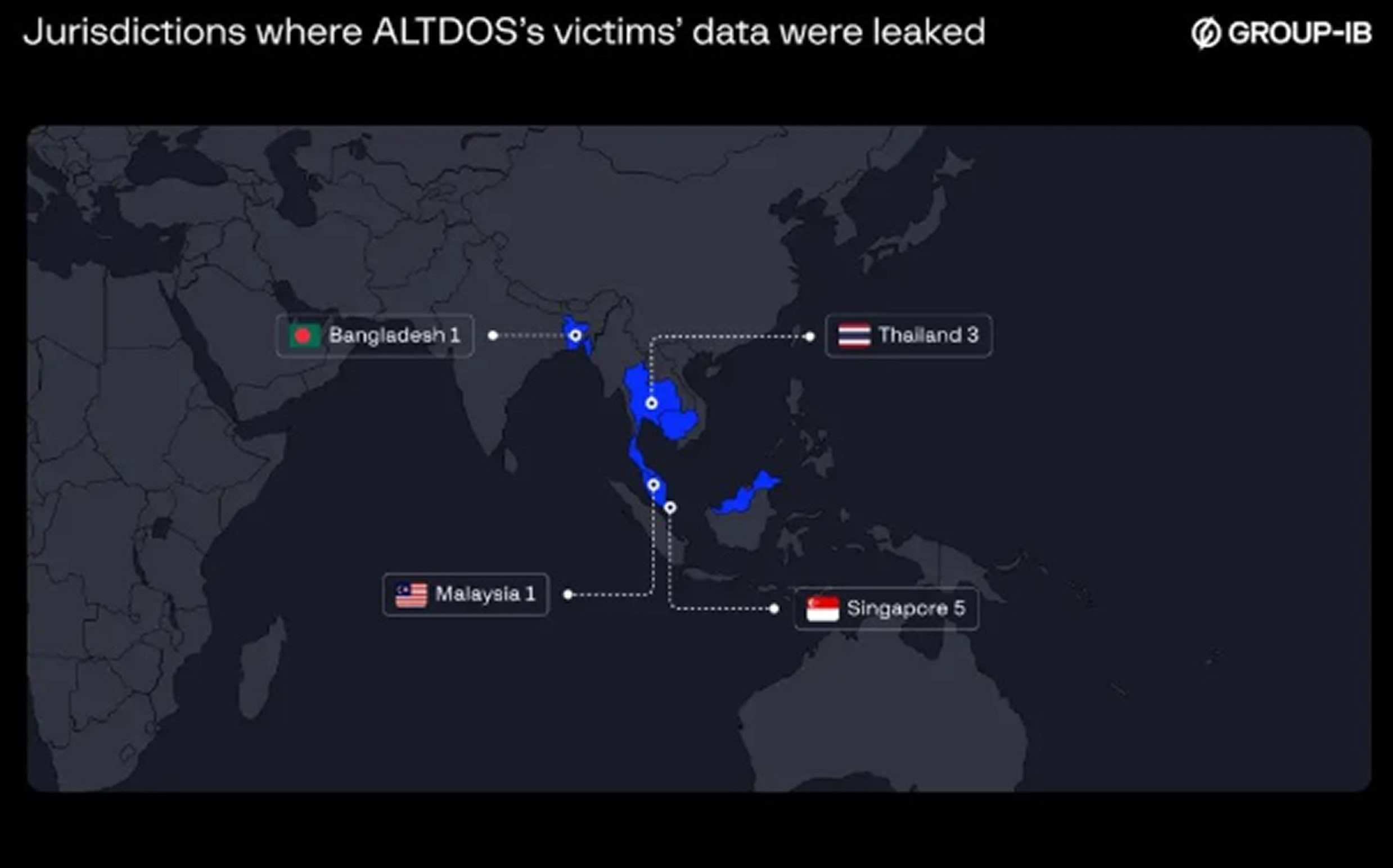
The ultimate goal was extortion demanding ransoms to prevent the leaked data from being exposed. If victims refused to comply, the attacker escalated tactics by reporting the breaches to data protection regulators and advertising the stolen data for sale on dark web forums to maximize profits.
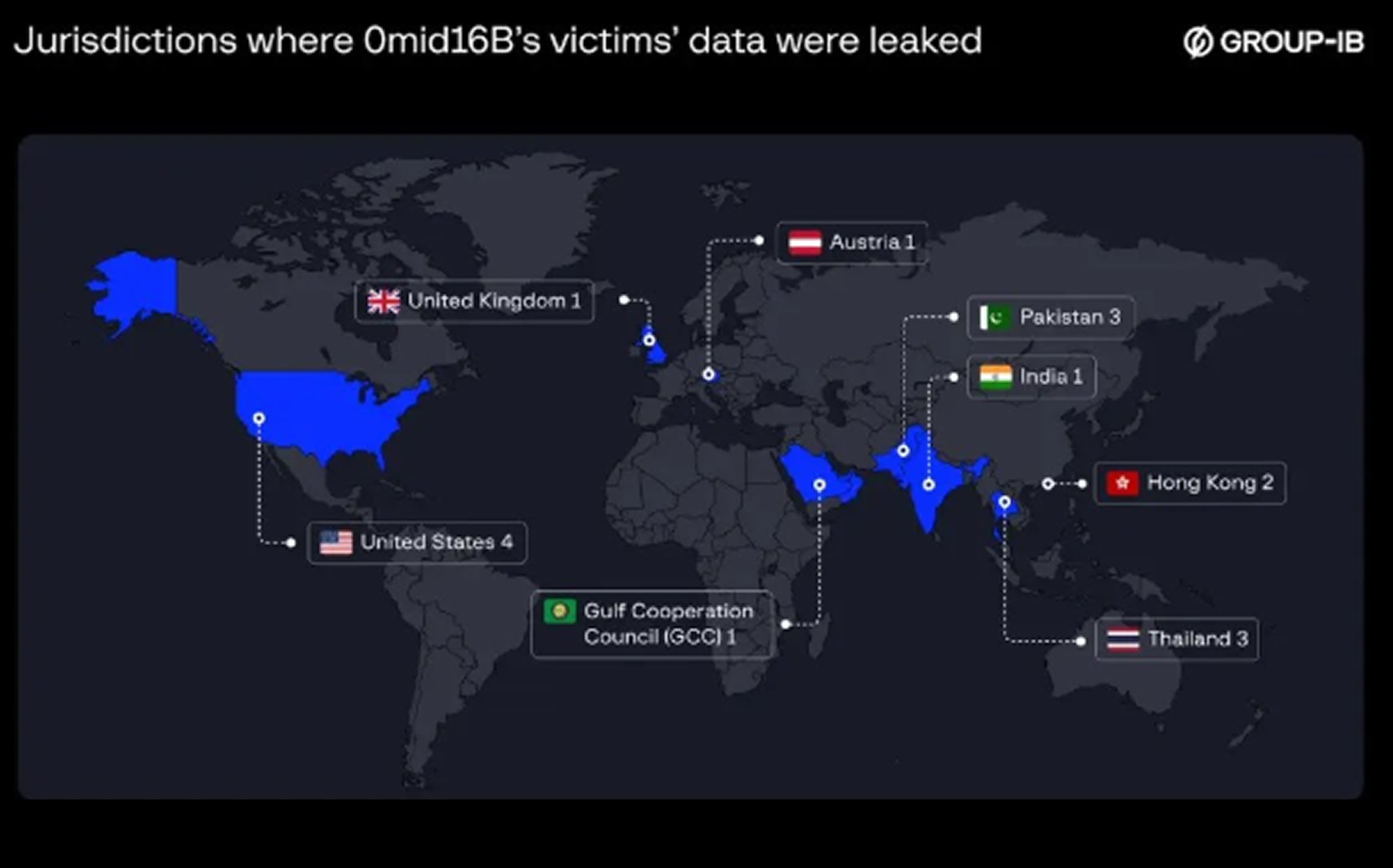
Cybersecurity analysts at Group-IB uncovered patterns linking all four aliases through extensive digital forensics. Despite using different identities, the hacker repeatedly left behind identifiable traces, allowing investigators to connect them to a single entity.
Technical Infrastructure and Attack Methods
A closer look into the hacker’s operations revealed a consistent technical setup:
- Used VirtualBox running Kali Linux for cyberattacks.
- Deployed a cracked version of Cobalt Strike to maintain access to compromised servers.
- Stored stolen data in an identical folder structure (/media/sf_E_DRIVE/) across all aliases.
Interestingly, the attacker showed minimal lateral movement within networks, focusing instead on efficiently extracting data to rented cloud servers before launching extortion attempts.
Ransom communications followed a predictable format, with messages always beginning with "Today is" followed by "This is", maintaining consistency across different aliases.
After years of investigation, the Royal Thai Police apprehended the cybercriminal on February 26, 2025. The operation was led by Group-IB’s Threat Intelligence and High-Tech Crime Investigation teams based in Thailand and Singapore.
Found this article interesting? Follow us on X(Twitter) and Instagram to read more exclusive content we post.


