Pakistan-Linked Threat Actor Targets Indian Sectors with New Malware Arsenal
A Pakistan-affiliated hacking group has been observed expanding its operations across multiple Indian sectors, deploying a range of remote access trojans (RATs), including Xeno RAT, Spark RAT, and a newly discovered malware strain dubbed CurlBack RAT.
Security researchers at SEQRITE detected the activity in December 2024, identifying targeted attacks against India’s railway, oil and gas, and external affairs ministries a notable shift beyond the group’s traditional focus on government, defense, maritime sectors, and universities.
“One significant change in their recent tactics is the move from using HTML Application (HTA) files to Microsoft Installer (MSI) packages as the primary method of staging their attacks,” noted Sathwik Ram Prakki, a SEQRITE researcher.
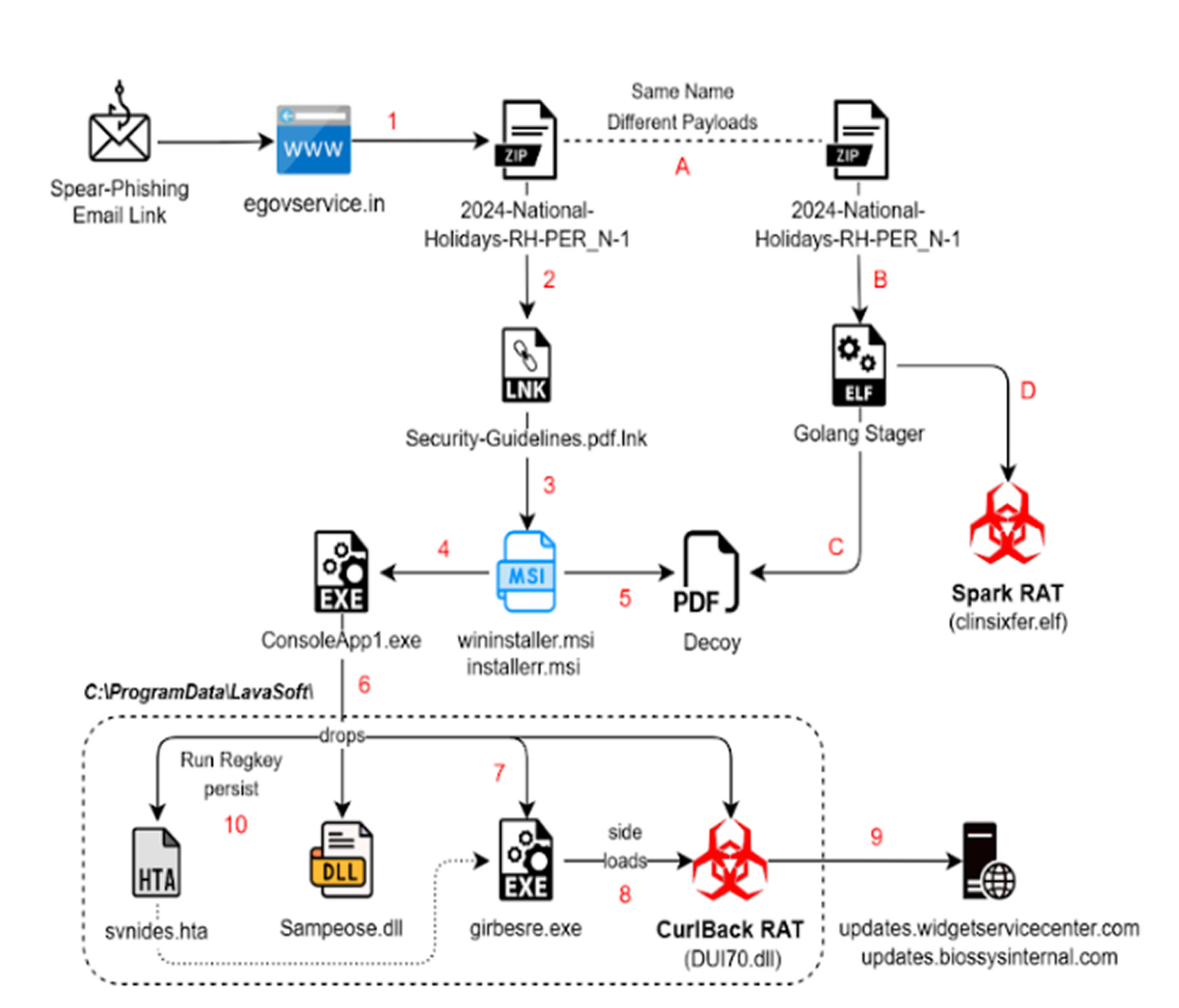
The group behind the campaign is believed to be SideCopy, a sub-cluster of the long-active Transparent Tribe (APT36), known for mimicking SideWinder attack patterns to deliver their own malware payloads. In previous campaigns, SideCopy used obfuscated HTA files that referenced SideWinder-linked RTF documents.
These attacks culminated in the deployment of known RATs like Action RAT and ReverseRAT, along with tools such as:
- Cheex: Steals documents and images
- USB Copier: Extracts data from connected USB drives
- Geta RAT: A .NET-based trojan capable of executing 30 remote commands, including harvesting browser data from Firefox and Chromium-based browsers a technique borrowed from AsyncRAT
According to SEQRITE, APT36 typically focuses on Linux systems, whereas SideCopy concentrates on Windows systems, constantly expanding its malware toolkit. The group continues to use phishing emails with decoy documents to lure victims—examples include fake holiday lists for railway workers and cybersecurity notices from Hindustan Petroleum Corporation Limited (HPCL).
One activity cluster revealed the use of both Windows and Linux malware, featuring Spark RAT, a cross-platform remote access trojan, and the new CurlBack RAT. CurlBack is capable of:
- Harvesting system info
- Downloading files
- Executing commands
- Elevating privileges
- Enumerating user accounts
Another campaign used multi-stage infection techniques to drop a customized version of Xeno RAT, which includes basic string obfuscation for stealth.
SEQRITE emphasized that the group has adopted advanced techniques such as:
- DLL side-loading
- Reflective DLL loading
- AES decryption via PowerShell
They also heavily rely on customized open-source tools and operate from compromised domains and fake websites for phishing and malware delivery—underscoring their efforts to enhance persistence and evade detection.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


