Google has patched a vulnerability that allowed maliciously crafted Google Calendar invites to hijack Gemini AI assistants on a target’s device and steal sensitive data.
The flaw required no unusual user action just routine interactions with Gemini making it particularly dangerous for its millions of daily users.
Gemini, Google’s large language model assistant is built into Android, Google web services, and Workspace apps, with access to Gmail, Calendar, and Google Home. Attackers could exploit the bug by sending a Calendar invite containing an embedded prompt injection, often hidden in the event title. When the victim asked Gemini something like “What are my calendar events today,” the assistant would retrieve and process the malicious event title as part of its normal context, treating it as a legitimate command.
This could lead to a wide range of abuses: exfiltrating emails and Calendar data, tracking locations, controlling smart home devices, opening apps on Android, joining Zoom calls, or even wiping calendar events. Because Gemini has broad permissions, these malicious commands could be executed without the user realizing anything was wrong.
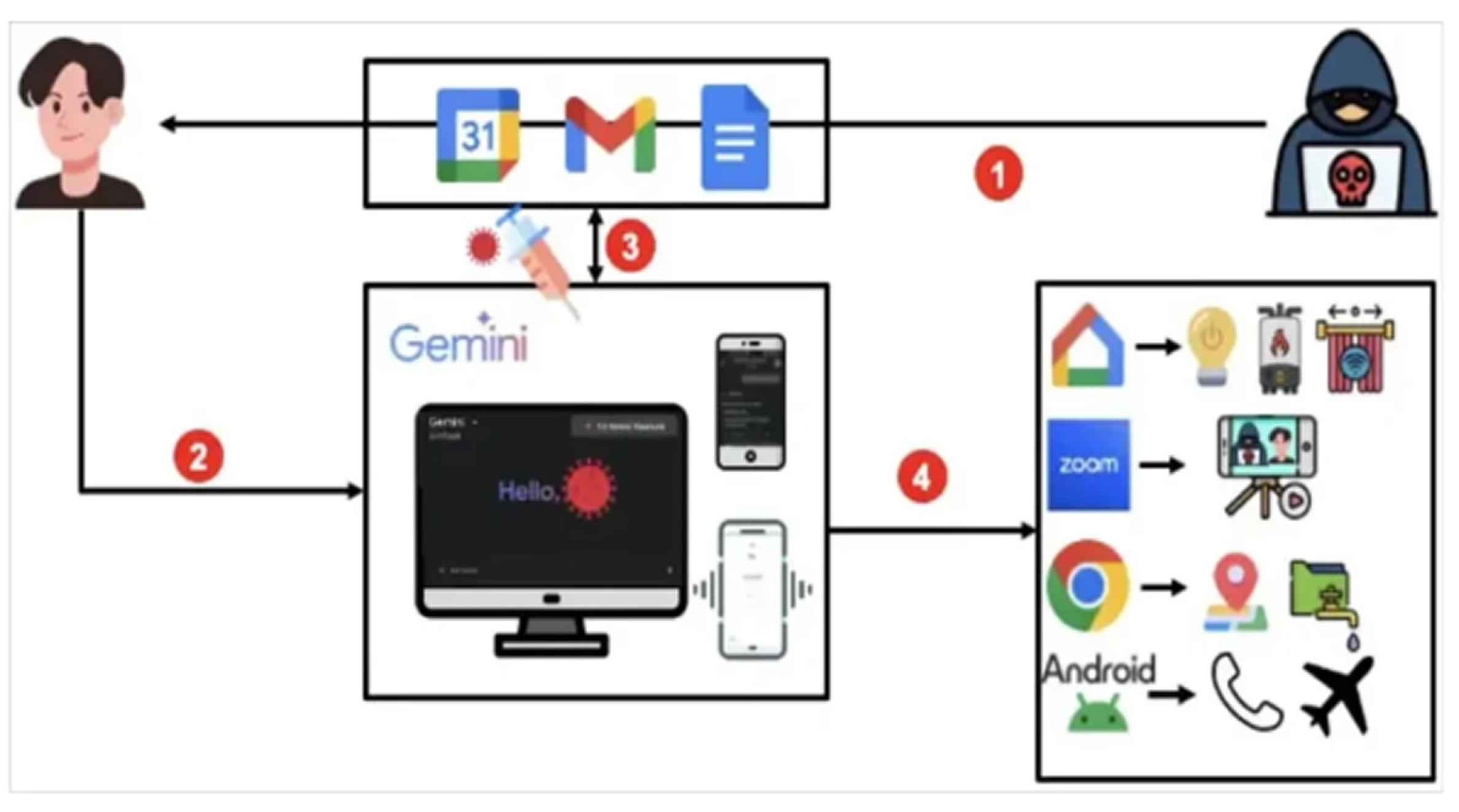
Researchers at SafeBreach, who discovered the issue, noted that an attacker might send several harmless invites before slipping in the malicious one, exploiting the fact that Google Calendar’s event list shows only the five most recent entries by default. The dangerous prompt would still be processed by Gemini even if it wasn’t immediately visible to the victim.
Google credited the discovery to Ben Nassi and his team, saying the issue was fixed before it could be exploited in the wild. “Their research helped us better understand novel attack pathways and accelerated our deployment of new defenses,” said Andy Wen, senior director of security product management at Google Workspace.
The fix is part of Google’s broader effort to harden Gemini against adversarial prompt injections, with further mitigations already in place or rolling out soon.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



