The cybercriminal group known as Silver Fox has been linked to a Bring Your Own Vulnerable Driver (BYOVD) attack that exploits a previously unknown driver from WatchDog Anti-malware. This tactic is used to disable security software on infected systems.
The targeted driver, "amsdk.sys" (version 1.0.600), is a 64-bit Windows kernel driver signed by Microsoft and built on the Zemana Anti-Malware SDK. It was not listed in Microsoft's Vulnerable Driver Blocklist and had evaded detection by community tools like LOLDrivers.
Silver Fox uses a dual-driver approach. For Windows 7, they deploy the known vulnerable Zemana driver "zam.exe." For Windows 10 and 11, they use the undetected WatchDog driver. This driver contains serious flaws, including the ability to terminate any process without checking its protection status and a local privilege escalation vulnerability that grants full access to the device.
Check Point first identified the campaign in May 2025. The attackers aim to disable endpoint protection and deploy ValleyRAT (also known as Winos 4.0), a remote access trojan. The malware is delivered via a single loader that includes anti-analysis features, embedded drivers, antivirus-killing logic, and a downloader for ValleyRAT.
If the malware detects a virtual machine, sandbox, or hypervisor, it halts execution and displays a fake error message. Once active, it connects to a command-and-control server to download the ValleyRAT backdoor.
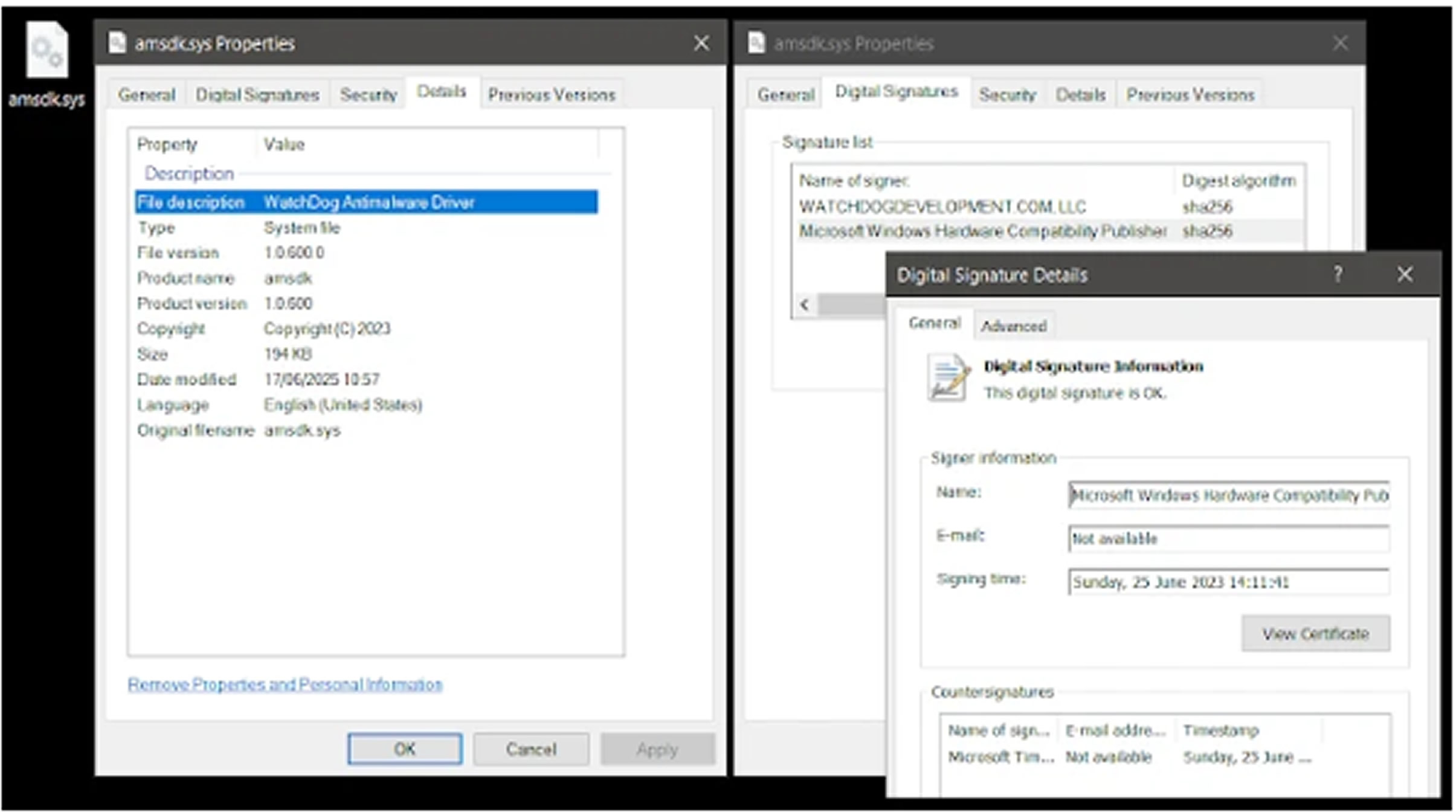
After disclosure, WatchDog released a patch (version 1.1.100) to fix the privilege escalation issue by enforcing stricter access controls. However, the process termination flaw remains. Attackers quickly adapted by modifying a single byte in the driver's timestamp field, preserving its Microsoft signature while bypassing hash-based blocklists.
This campaign highlights how attackers are now exploiting previously unknown, signed drivers, which many security tools fail to detect. Signature manipulation adds another layer of evasion.
Silver Fox, also known by aliases like SwimSnake and UTG-Q-1000, has been active since late 2022. The group mainly targets Chinese-speaking users through fake websites posing as Chrome, Telegram, and AI tools like DeepSeek. They distribute ValleyRAT using trojanized open-source software, Qt-based programs, and disguised MSI installers.
According to Antiy, Silver Fox spreads malware via instant messaging apps like WeChat, SEO tricks, and phishing emails. Their tactics evolve frequently to bypass antivirus defenses.
QiAnXin has identified a subgroup within Silver Fox called the Finance Group. This unit targets financial professionals using phishing lures related to tax audits and subsidies. They host malware on legitimate cloud platforms like Alibaba Cloud OSS and Youdao Cloud Notes to avoid detection.
Once inside a system, the Finance Group hijacks social media accounts and sends phishing QR codes to WeChat groups to steal bank credentials and drain funds. Other subgroups include the News and Romance Group, the Design and Manufacturing Group, and the Black Watering Hole Group.
QiAnXin describes UTG-Q-1000 as one of China's most aggressive cybercrime groups. Their operations combine espionage, remote control, and financial fraud, forming a well-organized black-market ecosystem.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.