Cybersecurity experts have uncovered a new phishing campaign targeting users in Taiwan with malware strains such as HoldingHands RAT and Gh0stCringe.
According to Fortinet’s FortiGuard Labs, the attacks are part of a wider operation that previously delivered the Winos 4.0 malware framework in January through phishing emails posing as messages from Taiwan’s National Taxation Bureau. Continued monitoring allowed researchers to identify more malware samples and link them to the same threat actor, known as Silver Fox APT. This group has been observed distributing malware-laden PDF documents and ZIP files through deceptive emails to deploy Gh0stCringe and a variant of HoldingHands RAT.
Both HoldingHands RAT (also referred to as Gh0stBins) and Gh0stCringe are versions of the well-known Gh0st RAT, a remote access trojan commonly used by Chinese hacking groups.
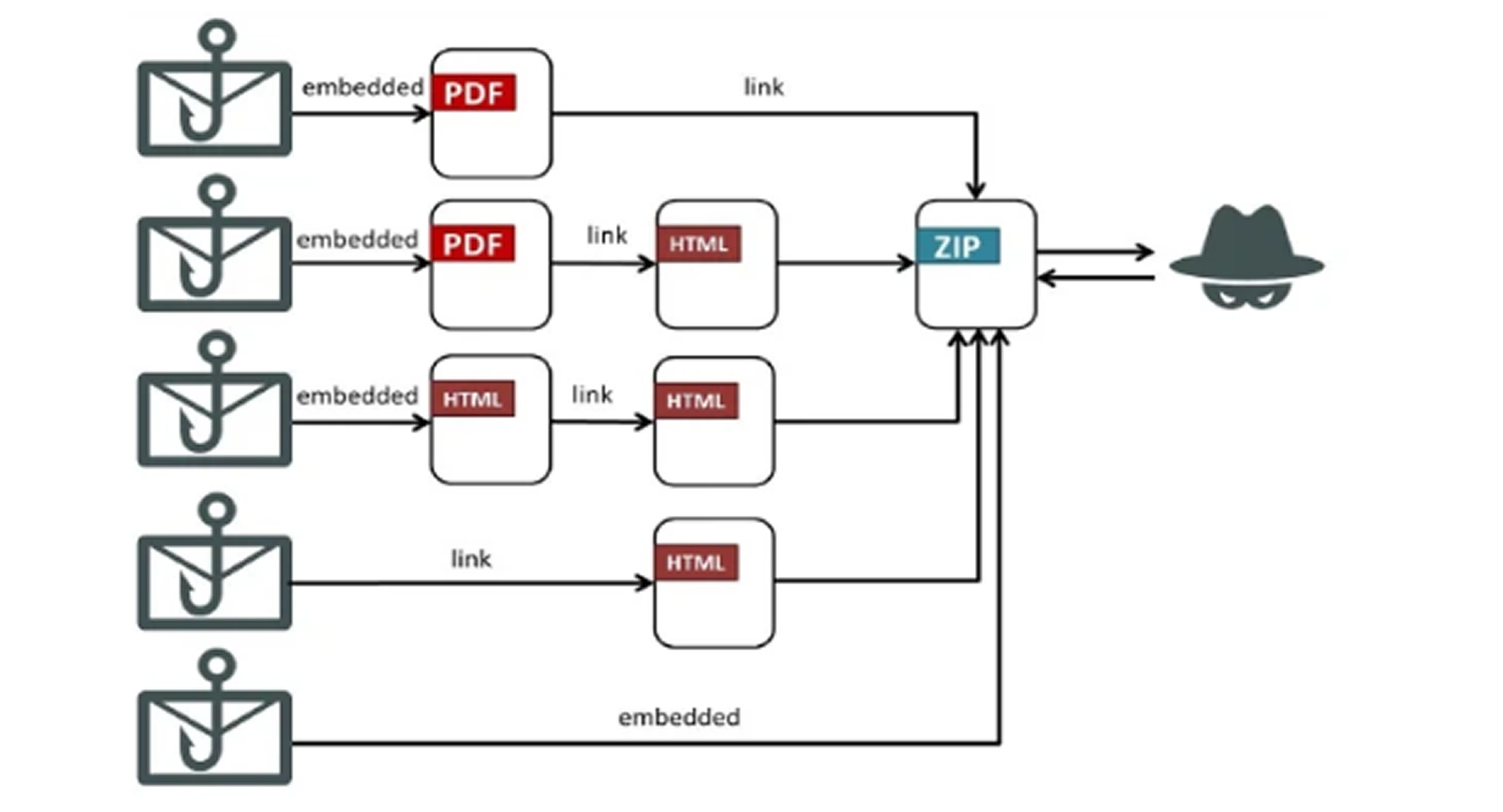
The attack typically starts with a phishing email that appears to be from a government agency or business contact. These messages often use topics like taxes, invoices, or pensions to convince victims to open the attachment. In some cases, an embedded image leads the recipient to download the malware.
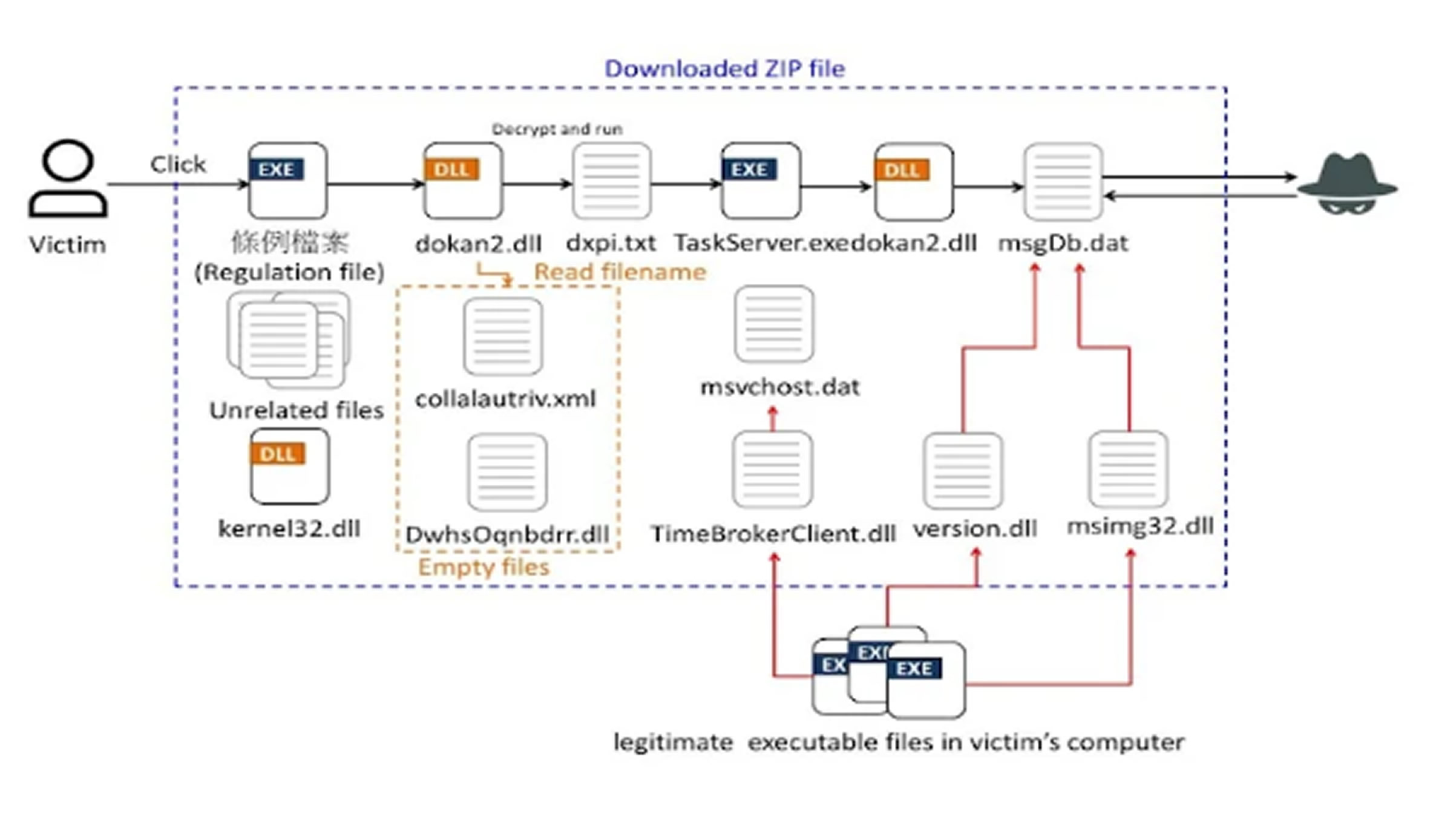
The malicious PDF files contain links directing targets to a webpage where they can download a ZIP file. Inside the archive are legitimate-looking executables, shellcode loaders, and encrypted shellcode. The infection process unfolds in multiple stages. First, the shellcode loader decrypts and executes the embedded shellcode, which consists of DLL files executed via DLL side-loading. These intermediate payloads are designed with anti-virtual machine checks and privilege escalation features to ensure successful deployment on the target system.
The attack ultimately results in the execution of a file named "msgDb.dat," which handles command-and-control operations. This includes gathering user data and downloading additional modules that support file access and remote desktop functionality.
Fortinet also reported that the threat actor uses PDF attachments in phishing emails to direct users to HTM pages, which host malicious document downloads.
"The attack chain includes various shellcode snippets and loaders, creating a complex infection flow," Fortinet explained. "Through Winos, HoldingHands, and Gh0stCringe, this threat actor continues to adapt its malware and distribution techniques."
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.