Complex Multi-Stage Attack Deploys Agent Tesla, Remcos RAT, and XLoader Variants
Security researchers from Palo Alto Networks' Unit 42 have uncovered a sophisticated multi-stage malware campaign distributing several prominent malware families, including Agent Tesla variants, Remcos RAT, and XLoader.
Threat actors are increasingly leveraging complex delivery chains to bypass detection, evade sandbox environments, and ensure successful payload execution,” said Saqib Khanzada, a researcher at Unit 42.
Attack Chain Breakdown
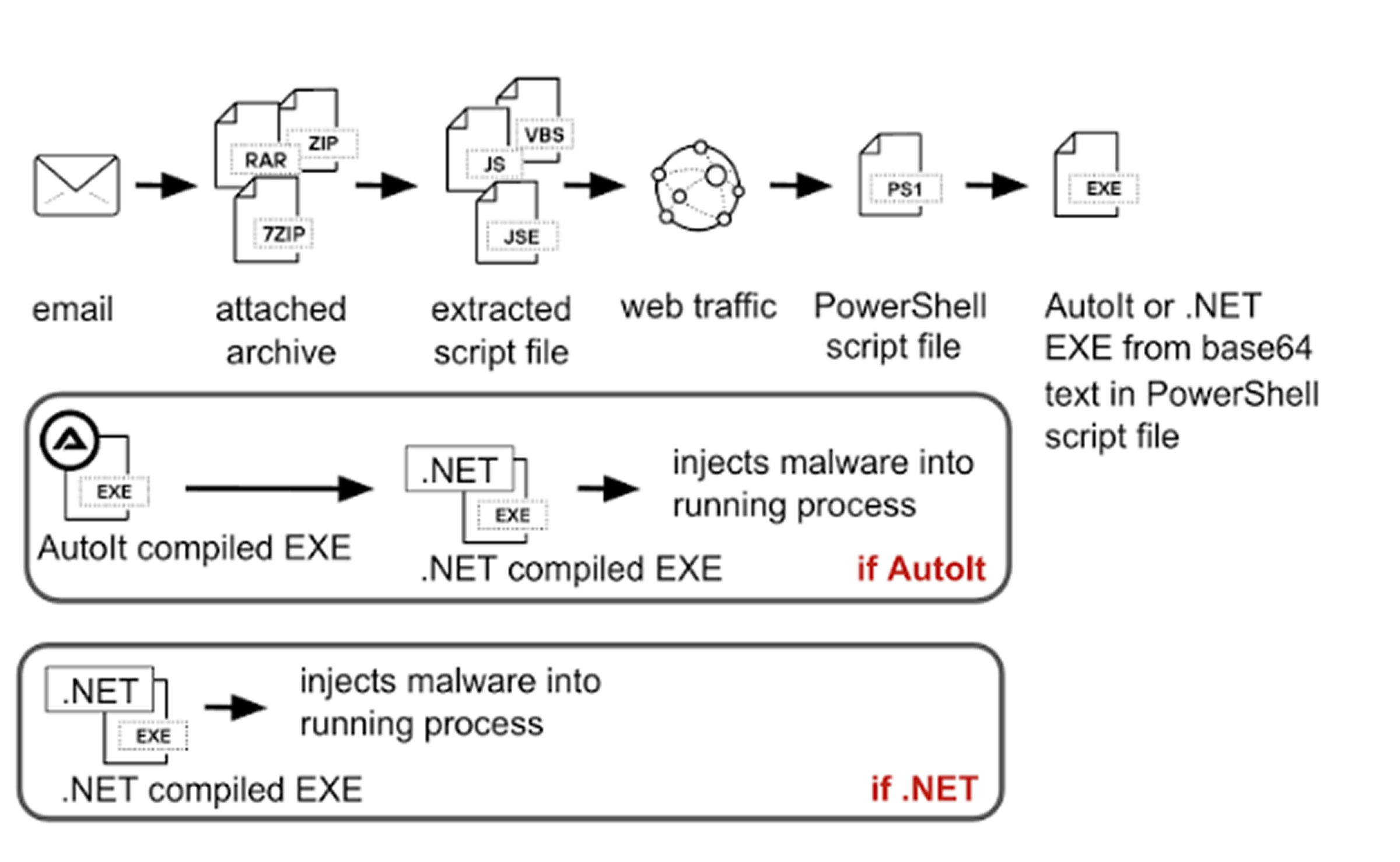
The attack begins with a phishing email masquerading as a payment or order request. The email contains a malicious 7-Zip archive that includes a JavaScript Encoded (.JSE) file. First observed in December 2024, the message falsely claims a payment has been made and urges the recipient to open the attached "order" file.
Once executed, the JavaScript payload initiates a PowerShell download from an external server. This PowerShell script carries a Base64-encoded payload, which is decoded, written to the Windows temporary directory, and executed. The infection then proceeds to a second-stage dropper—either a .NET or AutoIt-compiled executable.
.NET Path: The embedded encrypted payload, likely Agent Tesla, Snake Keylogger, or XLoader, is decrypted and injected into the "RegAsm.exe" process, following tactics previously seen in Agent Tesla campaigns.
AutoIt Path: Adds an extra obfuscation layer. The compiled AutoIt script carries an encrypted payload that loads final shellcode, injecting a .NET file into the "RegSvcs.exe" process to deploy Agent Tesla.
Khanzada notes, “The attackers employ multiple execution paths to enhance resilience and detection evasion. Their focus lies in stacking straightforward stages over using heavily obfuscated techniques.
IronHusky Campaign Deploys MysterySnail RAT Variant
Meanwhile, Kaspersky has reported a separate campaign targeting government agencies in Mongolia and Russia, attributed to the Chinese-speaking threat group IronHusky, active since at least 2017.
The attack uses a malicious Microsoft Management Console (MMC) script disguised as a Word document from Mongolia’s National Land Agency ("co-financing letter_alamgac"). This script fetches a ZIP archive containing a decoy document, a legitimate binary ("CiscoCollabHost.exe"), and a malicious DLL ("CiscoSparkLauncher.dll").
Although the delivery method of the MMC script is unclear, the phishing-style document suggests a social engineering approach.
The attack relies on DLL sideloading. The legitimate executable loads the backdoor DLL, which uses the open-source piping-server project to connect to attacker-controlled infrastructure. The backdoor supports various functions including:
- File uploads/downloads
- Directory listing
- Command shell execution
- Process control
- Self-deletion
These capabilities enable the deployment of the full-featured MysterySnail RAT, which now includes nearly 40 commands for file management, service control, network access, and process handling.
After initial intrusion attempts were mitigated, Kaspersky observed the attackers switching to a lighter version called MysteryMonoSnail, capable of only 13 basic functions—such as launching remote shells, writing data, and listing directories.
“This stripped-down version is clearly a fallback tool used after organizations hardened their systems against the original payload,” Kaspersky explained.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


