The Computer Emergency Response Team of Ukraine (CERT-UA) has identified a new wave of cyber attacks targeting Ukrainian institutions
with malware designed to steal sensitive information. These attacks are aimed at military groups, law enforcement, and local government bodies, particularly those near Ukraine’s eastern border.
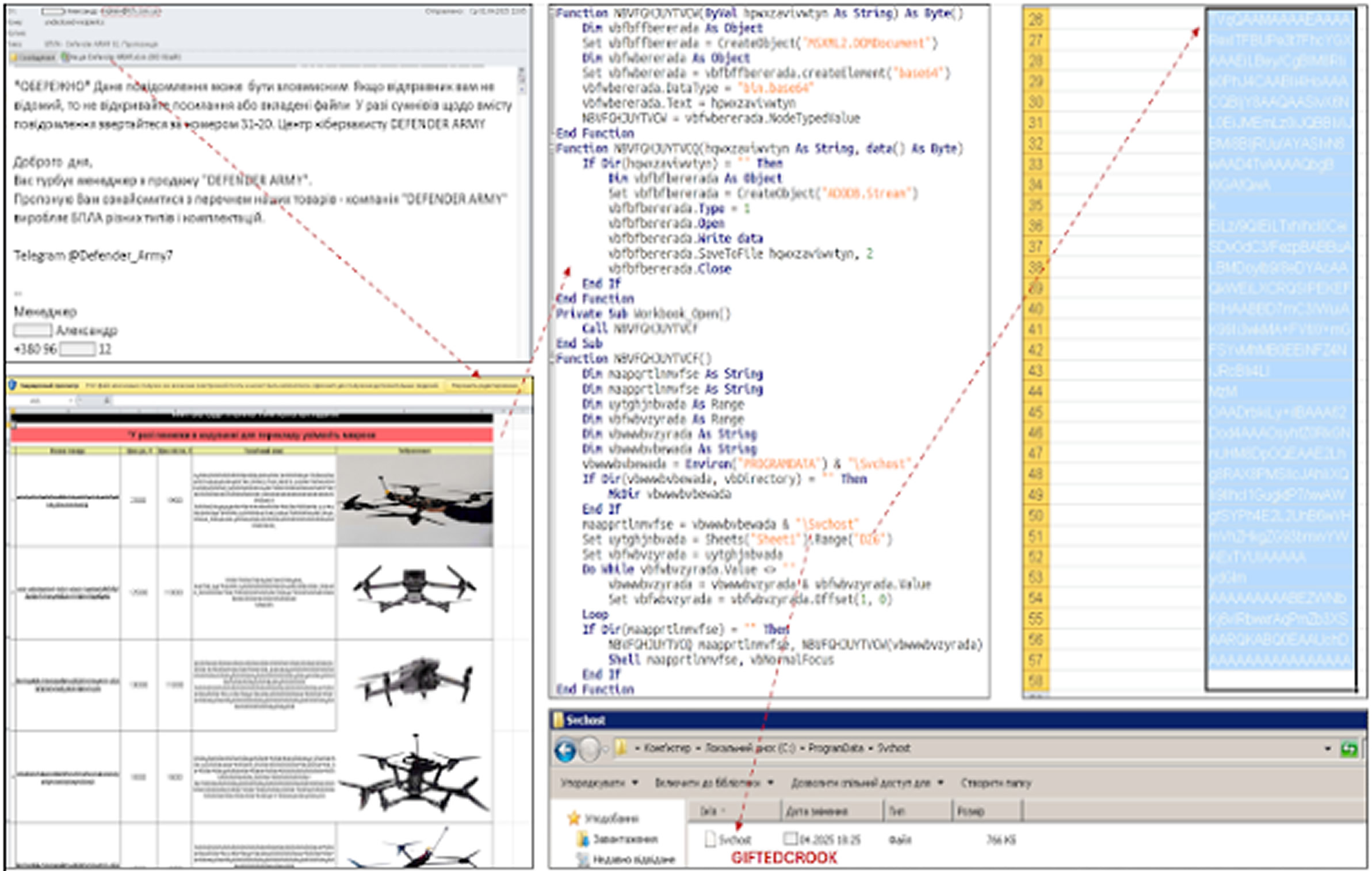
The attacks utilize phishing emails that contain a macro-enabled Microsoft Excel spreadsheet (XLSM). When the recipient opens the spreadsheet, it triggers the deployment of two types of malwares: a PowerShell script sourced from the PSSW100AVB GitHub repository, which opens a reverse shell, and an undocumented malware called GIFTEDCROOK. The file names and email subject lines are crafted to appear relevant and sensitive, referencing topics like demining, fines, UAV production, and compensation for destroyed property, in order to deceive the recipients. Once the victim enables macros, the malicious code is executed automatically.
GIFTEDCROOK, written in C/C++, is used to steal sensitive information from popular web browsers such as Google Chrome, Microsoft Edge, and Mozilla Firefox. It targets data like cookies, browsing history, and authentication details. The phishing emails are sent from compromised accounts, often through email clients' web interfaces, to make the messages look more legitimate and encourage recipients to open the attachments. CERT-UA has attributed these attacks to the threat cluster UAC-0226, but it has not yet linked the campaign to a specific nation.
This discovery follows the activity of another suspected Russian-linked espionage group, UNC5837, which was tied to a phishing campaign in October 2024 targeting European government and military organizations. This campaign used signed .RDP file attachments to establish Remote Desktop Protocol (RDP) connections. Instead of typical RDP attacks focusing on interactive sessions, the campaign creatively used resource redirection and RemoteApps to map victim file systems to attacker servers and present attacker-controlled applications to the victims.
The RDP attack, documented by CERT-UA and other organizations like AWS, Microsoft, and Trend Micro, also utilized the open-source tool PyRDP to automate malicious activities such as file exfiltration and clipboard capture, including passwords. The primary objective of this campaign appears to be espionage and file theft.
Additionally, there have been reports of phishing campaigns leveraging fake CAPTCHAs and Cloudflare Turnstile to distribute Legion Loader (also known as Satacom). This malware acts as a gateway for installing a malicious Chromium-based browser extension named “Save to Google Drive.” The malware is delivered through a drive-by download infection, where victims are lured to a malicious website. Once the victim clicks the CAPTCHA, they are redirected multiple times, leading to a page that prompts them to download a document. In reality, this process is used to install Legion Loader, which then executes PowerShell scripts to add the rogue browser extension to the victim's browser. The extension’s purpose is to capture sensitive information and send it to the attackers.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.