Cybercriminals are actively taking advantage of a severe vulnerability in the "Alone – Charity Multipurpose Non-profit WordPress Theme" to seize control of vulnerable websites.
The flaw, identified as CVE-2025-5394 and carrying a CVSS score of 9.8, was discovered and reported by security researcher Thái An. Wordfence reports that the issue involves an arbitrary file upload vulnerability affecting all theme versions up to and including 7.8.3. A fix was introduced in version 7.8.5 on June 16, 2025.
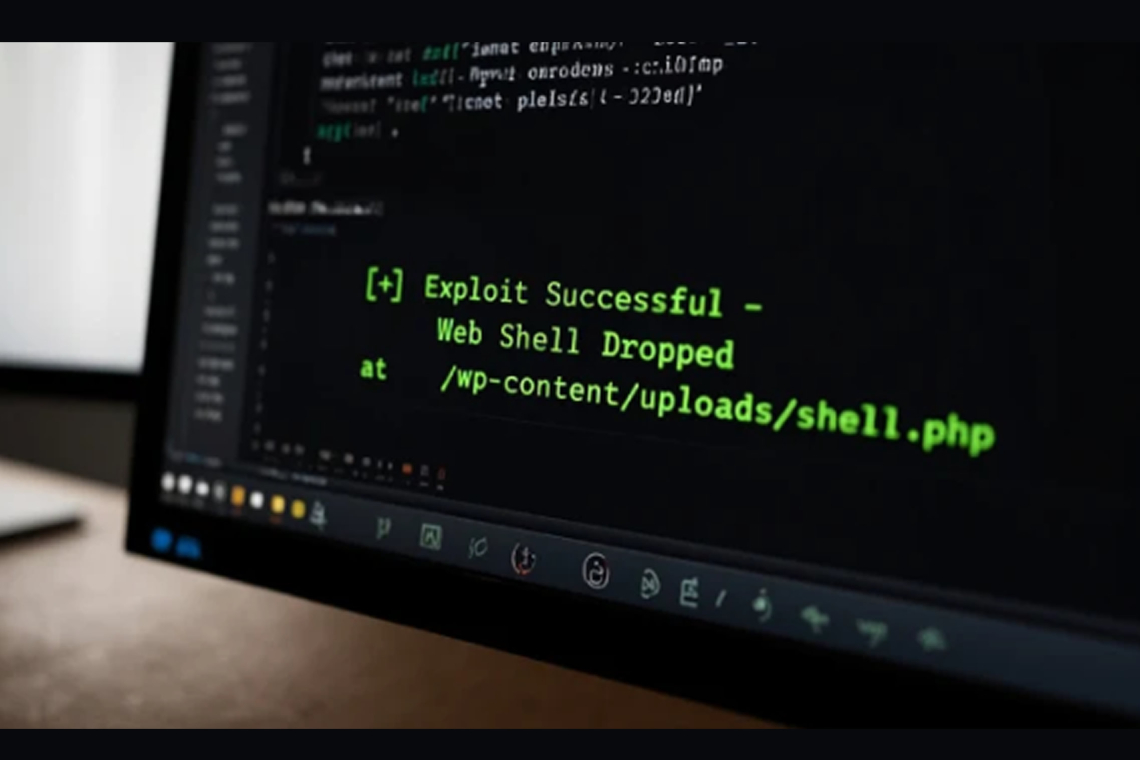
The vulnerability stems from a plugin installation function called alone_import_pack_install_plugin() which lacks a proper capability check. This oversight allows unauthenticated users to upload plugins from external sources via AJAX, leading to remote code execution.
"This flaw enables attackers to upload arbitrary files and execute code remotely, which often results in complete site takeovers," said Wordfence's István Márton.
Exploitation of the flaw began on July 12, two days before public disclosure suggesting attackers may have been monitoring code changes to detect newly patched weaknesses. Wordfence has already blocked more than 120,000 exploit attempts linked to this vulnerability. Attacks have originated from the following IP addresses:
- 193.84.71.244
- 87.120.92.24
- 146.19.213.18
- 185.159.158.108
- 188.215.235.94
- 146.70.10.25
- 74.118.126.111
- 62.133.47.18
- 198.145.157.102
2a0b:4141:820:752::2
During these attacks, threat actors commonly upload ZIP files like "wp-classic-editor.zip" or "background-image-cropper.zip" that include PHP-based backdoors to execute commands remotely and upload additional files. These payloads often contain advanced file managers and scripts that can create rogue admin accounts.
To reduce exposure, WordPress site owners using the affected theme should immediately update to the latest version, review admin accounts for unauthorized access, and check server logs for suspicious activity related to the URL /wp-admin/admin-ajax.php?action=alone_import_pack_install_plugin
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.