The advanced persistent threat (APT) group Cloud Atlas, also known as Clean Ursa, Inception, Oxygen, and Red October,
According to a recent analysis by Kaspersky researcher Oleg Kupreev, the infection vector primarily involves malicious Microsoft Office documents embedded within phishing emails. These documents exploit CVE-2018-0802, a well-known vulnerability in Microsoft’s Equation Editor, to execute arbitrary code, allowing attackers to download and deploy VBShower, PowerShower, and VBCloud malware onto compromised systems.
Over 80% of the affected victims have been identified in Russia, with additional targets located in Belarus, Canada, Moldova, Israel, Kyrgyzstan, Turkey, and Vietnam. This geographical distribution suggests a geo-political or intelligence-gathering motivation, consistent with Cloud Atlas’s previous campaigns. The group has been active since at least 2014 and has previously been linked to high-profile cyber-espionage operations against entities in Russia, Belarus, and Transnistria.
In December 2022, Cloud Atlas was found leveraging a PowerShell-based backdoor called PowerShower, and by late 2023, it had evolved its tactics to exploit another outdated Microsoft Office vulnerability, CVE-2017-11882, to drop a Visual Basic Script (VBS) payload. The latest campaign expands on these techniques, integrating VBShower and VBCloud into its attack arsenal.
Cloud Atlas employs a multi-stage malware deployment strategy, using a combination of phishing tactics, document-based exploits, and staged payload execution. The attack sequence unfolds as follows:
The victim receives a well-crafted phishing email containing a malicious Microsoft Office document (.docx, .rtf, or .xls).
Upon opening, the document retrieves an embedded RTF template from a remote command-and-control (C2) server.
The template exploits CVE-2018-0802, allowing for arbitrary code execution.
Malware Download and Execution
The exploit fetches an HTML Application (HTA) file, which downloads additional payloads.
The HTA file leverages NTFS Alternate Data Streams (ADS) to store and execute multiple components stealthily within **%APPDATA%\Roaming\Microsoft\Windows**.
These files collectively establish the VBShower backdoor.
Persistence and Anti-Forensics Measures
The malware installs a launcher module that extracts and executes the VBShower backdoor in memory, avoiding disk-based detection.
A self-deleting VBS script clears forensic evidence by erasing files stored within *\Local\Microsoft\Windows\Temporary Internet Files\Content.Word* and removing traces of the launcher.
Command-and-Control Communication and Payload Deployment
VBShower connects to the attacker-controlled C2 infrastructure to download additional payloads, including PowerShower and VBCloud.
The PowerShower backdoor, functionally similar to VBShower, focuses on lateral movement and network reconnaissance by executing PowerShell scripts.
VBCloud differentiates itself by leveraging public cloud storage services for exfiltration and C2 communications, making its traffic harder to detect.
PowerShower enables post-exploitation activities and functions as a modular PowerShell-based reconnaissance tool. Kaspersky identified at least seven distinct PowerShell scripts delivered through PowerShower, each designed for specific offensive operations:
Active Directory Reconnaissance – Extracts lists of local groups, administrators, and domain controllers.
Credential Harvesting – Conducts Kerberoasting attacks, exploiting weak service principal names (SPNs) to obtain hashed credentials.
Privilege Escalation & Lateral Movement – Enumerates user accounts and attempts brute-force attacks.
Data Collection & Exfiltration – Scans for sensitive files stored in ProgramData and other system directories.
Additionally, PowerShower serves as a downloader for ZIP archive files, which may contain further payloads for deeper infiltration.
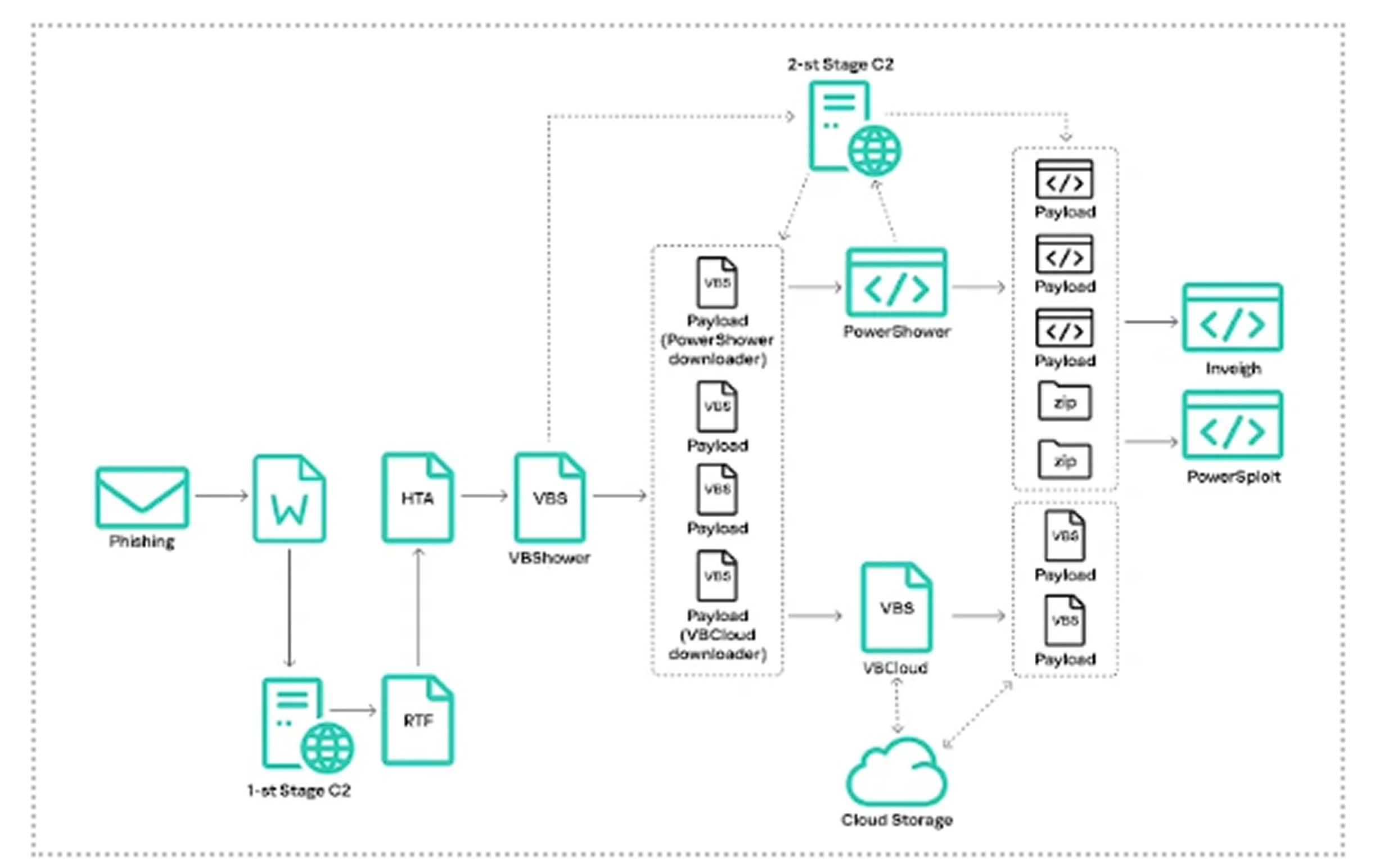
VBCloud functions as a covert data theft tool, designed to evade traditional network security measures by using cloud-based storage services for C2 communications. Executed via a scheduled task, VBCloud is triggered every time the infected user logs into the system.
Upon execution, VBCloud gathers:
System Metadata – Disk partitions, drive types, media size, and available free space.
Targeted File Exfiltration – Documents and data with extensions DOC, DOCX, XLS, XLSX, PDF, TXT, RTF, and RAR.
Telegram Data Theft – Searches for Telegram-related files, potentially extracting session tokens or stored messages for further compromise.
Strategic Implications: A Growing Cyber Threat
According to Kupreev, the infection chain is designed to achieve long-term persistence, conduct surveillance, and exfiltrate sensitive information from high-value targets. Cloud Atlas continues to adapt its tactics, techniques, and procedures (TTPs), demonstrating a sophisticated understanding of Microsoft Office exploits, PowerShell abuse, and cloud-based C2 architectures.
The combination of phishing, multi-stage malware deployment, and advanced persistence mechanisms underscores Cloud Atlas’s evolving cyber-espionage capabilities. Given the scale and sophistication of these attacks, organizations must
Implement robust email security to detect and filter phishing attempts.
Apply security patches promptly, particularly for Microsoft Office vulnerabilities (CVE-2018-0802, CVE-2017-11882).
Monitor PowerShell activity and restrict its execution where possible.
Deploy endpoint detection and response (EDR) solutions to identify anomalous behaviors linked to VBCloud and PowerShower.
As Cloud Atlas continues refining its attack methodologies, organizations—especially those in targeted regions—must remain vigilant against evolving threats posed by this sophisticated adversary.


