An unidentified threat actor has been linked to the development of several malicious
Chrome browser extensions since February 2024. These extensions are disguised as useful tools but secretly carry out activities such as data theft, command reception, and remote code execution.
According to a report shared with The Hacker News by the DomainTools Intelligence (DTI) team, the attacker creates websites that mimic legitimate services including productivity tools, ad and media assistants, VPNs, and crypto or banking platforms. These fake sites are used to lure users into downloading malicious extensions from the Chrome Web Store.
Although the extensions seem to deliver their promised functions, they also enable a range of malicious behaviors. These include stealing credentials and cookies, hijacking sessions, injecting ads, redirecting users to harmful websites, manipulating browser traffic, and launching phishing attacks through DOM manipulation. The extensions request broad permissions via the manifest.json file, allowing them to access every site the user visits, run arbitrary code from attacker-controlled servers, redirect web traffic, and inject advertisements.
Additionally, the extensions exploit the "onreset" event handler on a temporary DOM element to execute code, likely as a tactic to evade content security policy restrictions.
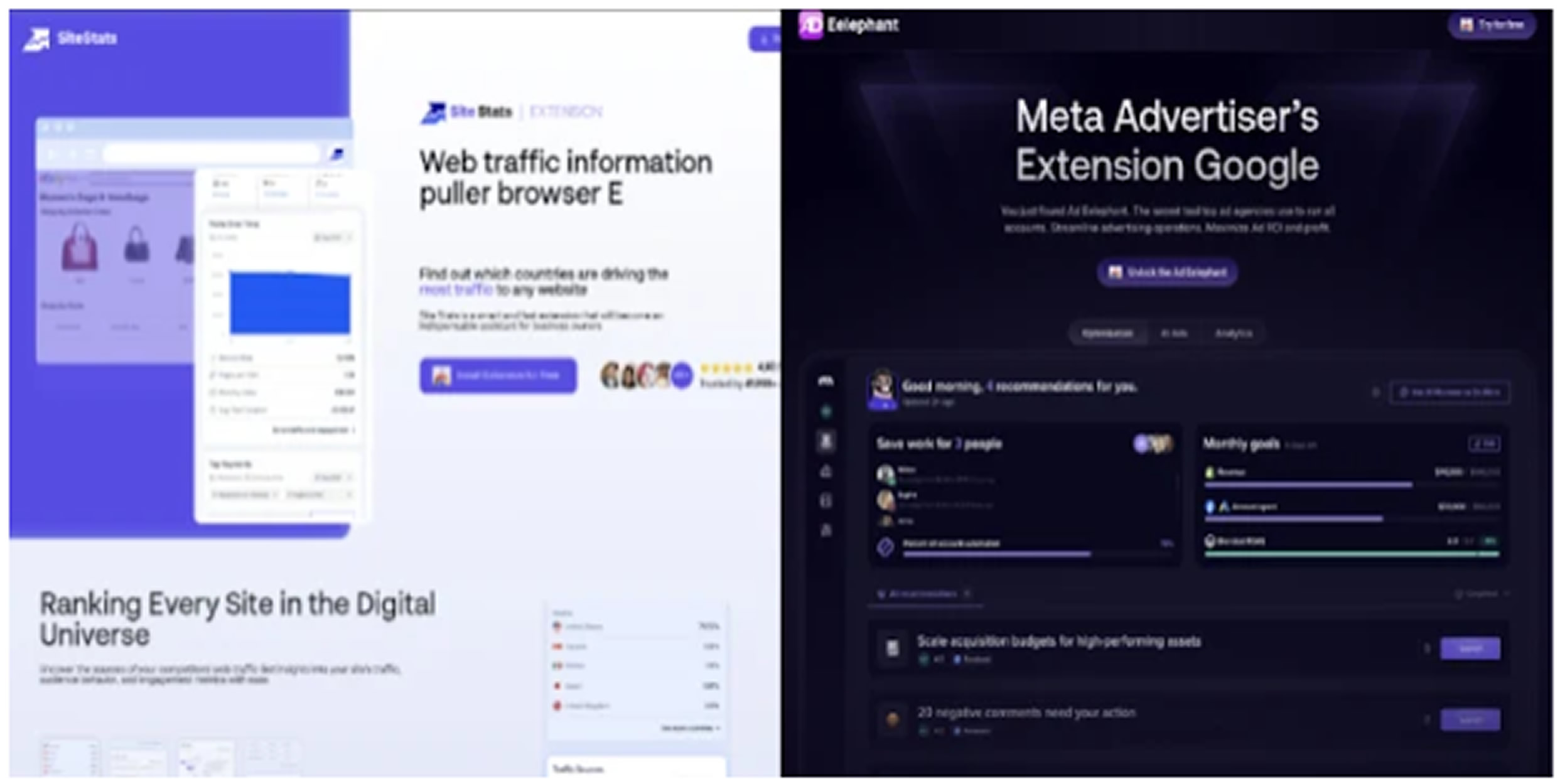
Some of the fake websites identified imitate real services such as DeepSeek, Manus, DeBank, FortiVPN, and Site Stats. These sites trick users into installing the harmful extensions, which then steal browser cookies, download remote scripts, and create a WebSocket connection to function as a traffic-routing proxy.
It remains unclear how users are initially directed to the fake websites. However, DomainTools suggested that common tactics like phishing or social media campaigns may be involved.
Because the malicious extensions are available in the Chrome Web Store and linked to accompanying websites, they can appear in search results both on the web and within the store itself. DomainTools also noted that many of the lure sites contain Facebook tracking IDs. This suggests the attackers may be using Facebook or Meta platforms such as pages, groups, or ads to attract visitors.
The identity of those behind the operation is still unknown, but more than 100 fake websites and extensions have been created. Google has removed the offending extensions from the store. To minimize the risk, users are encouraged to download extensions only from verified developers, carefully review permission requests, read user reviews, and avoid using extensions that appear suspicious or mimic well-known tools.
It is important to remember that ratings can be manipulated. For instance, DomainTools found that one of the malicious extensions pretending to be DeepSeek redirected users who gave low ratings (1 to 3 stars) to a private feedback form, while those giving high ratings (4 to 5 stars) were sent to the official review page on the Chrome Web Store.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


