Security researcher Jan Michael Alcantara noted that attackers use search engine optimization (SEO) techniques to manipulate search results
Cybersecurity researchers have uncovered a large-scale phishing campaign leveraging fake CAPTCHA images embedded in PDF documents hosted on Webflow's content delivery network (CDN) to distribute the Lumma Stealer malware. According to Netskope Threat Labs, 260 unique domains have been identified hosting around 5,000 phishing PDFs designed to redirect victims to malicious websites.
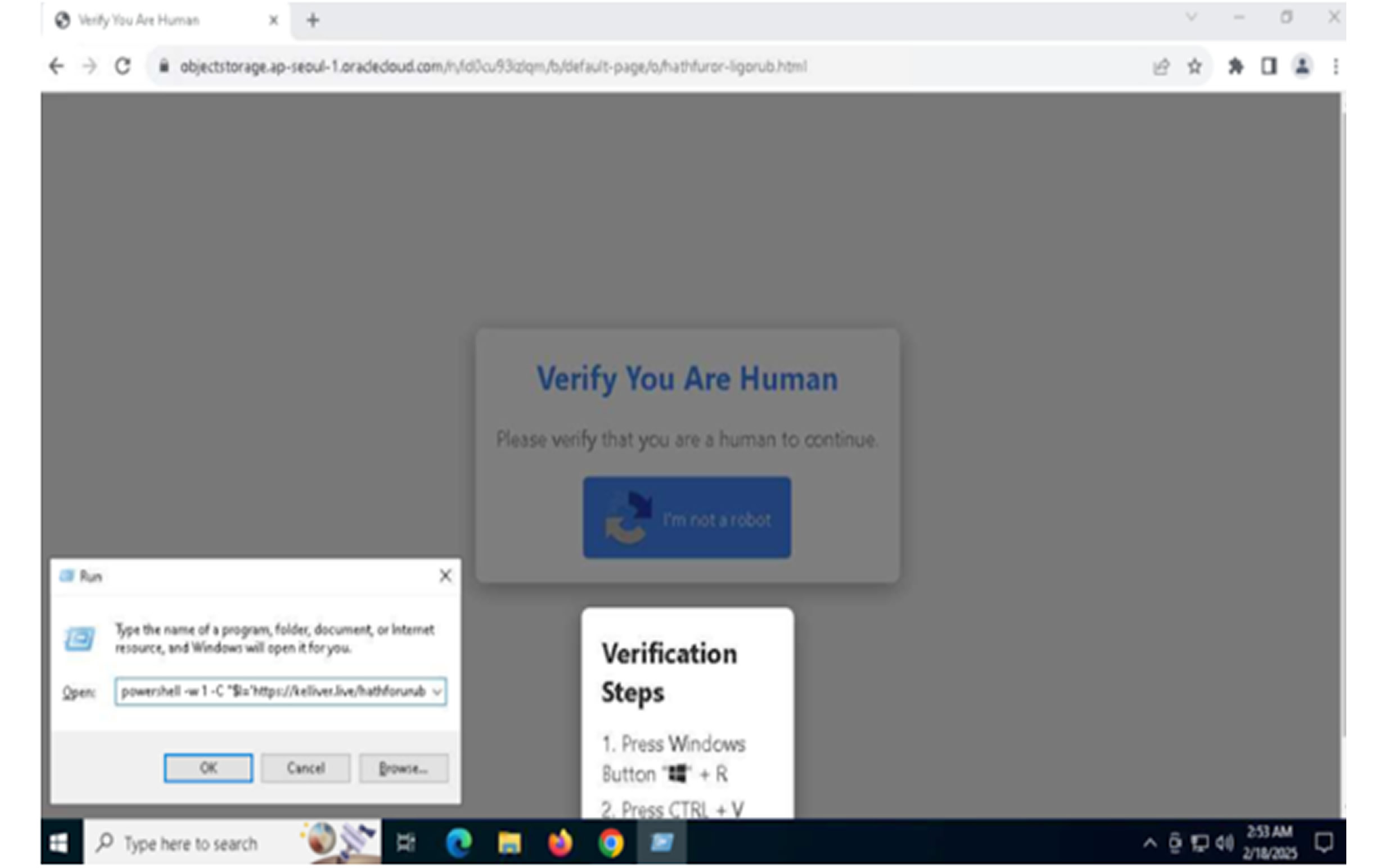
Security researcher Jan Michael Alcantara noted that attackers use search engine optimization (SEO) techniques to manipulate search results, leading unsuspecting users to these harmful pages. While many phishing campaigns aim to steal credit card details, some of these PDFs contain fake CAPTCHA verifications that trick victims into executing malicious PowerShell commands, ultimately leading to the Lumma Stealer malware infection.
This phishing operation has impacted over 1,150 organizations and more than 7,000 users since mid-2024, primarily targeting victims in North America, Asia, and Southern Europe across technology, financial services, and manufacturing sectors. The majority of the 260 identified phishing domains are associated with Webflow, followed by GoDaddy, Strikingly, Wix, and Fastly. Attackers have also uploaded these PDF files to legitimate online libraries and repositories such as PDFCOFFEE, PDF4PRO, PDFBean, and Internet Archive, making them more accessible to users searching for documents online.
The phishing PDFs employ fraudulent CAPTCHA images as a mechanism for stealing credit card information. Others distributing Lumma Stealer contain deceptive download buttons that redirect users to malicious sites. These sites mimic CAPTCHA verification pages and use the ClickFix technique, tricking victims into executing an MSHTA command, which runs the stealer malware via a PowerShell script.
In recent weeks, Lumma Stealer has also been disguised as Roblox games and a cracked version of the Total Commander tool for Windows, showcasing the diverse delivery methods used by threat actors. Many victims are redirected through YouTube videos, likely uploaded from previously compromised accounts. According to Silent Push, attackers often embed malicious links in YouTube video descriptions, comments, or pinned messages. The company warns that users should be cautious when prompted to download files or click on suspicious links while browsing YouTube.
Additionally, Lumma Stealer logs have been found on Leaky[.]pro, a relatively new hacking forum that emerged in late December 2024. The malware operates under a Malware-as-a-Service (MaaS) model, allowing cybercriminals to harvest sensitive data from compromised Windows hosts. Earlier in 2024, the Lumma operators integrated the malware with GhostSocks, a Golang-based proxy malware that enhances its capabilities.
According to Infrawatch, the SOCKS5 backconnect feature introduced in Lumma infections allows cybercriminals to bypass geographic restrictions and IP-based security checks, especially those implemented by financial institutions and other high-value targets. This significantly increases the likelihood of unauthorized access attempts using stolen credentials from infostealer logs, further enhancing the malware’s post-exploitation value.
The discovery of this campaign comes as other stealer malware, such as Vidar and Atomic macOS Stealer (AMOS), continue to spread via the ClickFix method using lures related to the DeepSeek AI chatbot, according to Zscaler ThreatLabz and eSentire.
Meanwhile, phishing campaigns are also abusing a JavaScript obfuscation technique that leverages invisible Unicode characters to represent binary values, a method first documented in October 2024. This approach utilizes Hangul half-width (U+FFA0) and Hangul full-width (U+3164) characters to encode binary values (0 and 1) and convert ASCII characters into their Hangul equivalents.
According to Juniper Threat Labs, these attacks are highly personalized and sophisticated, often containing non-public information about the target. The initial JavaScript payload employs anti-analysis mechanisms, such as invoking a debugger breakpoint to detect if it is being examined, and if so, it redirects users to a benign website to avoid detection.


