Cybercriminals Expand BADBOX 2.0 Scheme, Infecting Millions of Devices for Ad Fraud and Proxy Services.
Researchers have identified at least four cybercriminal groups involved in an advanced version of the BADBOX ad fraud and proxy botnet, highlighting a vast and interconnected cybercrime network.
The groups—SalesTracker Group, MoYu Group, Lemon Group, and LongTV—were identified by the HUMAN Satori Threat Intelligence and Research team in collaboration with Google, Trend Micro, Shadowserver, and other security partners.
BADBOX 2.0: The Largest Botnet Targeting Smart Devices
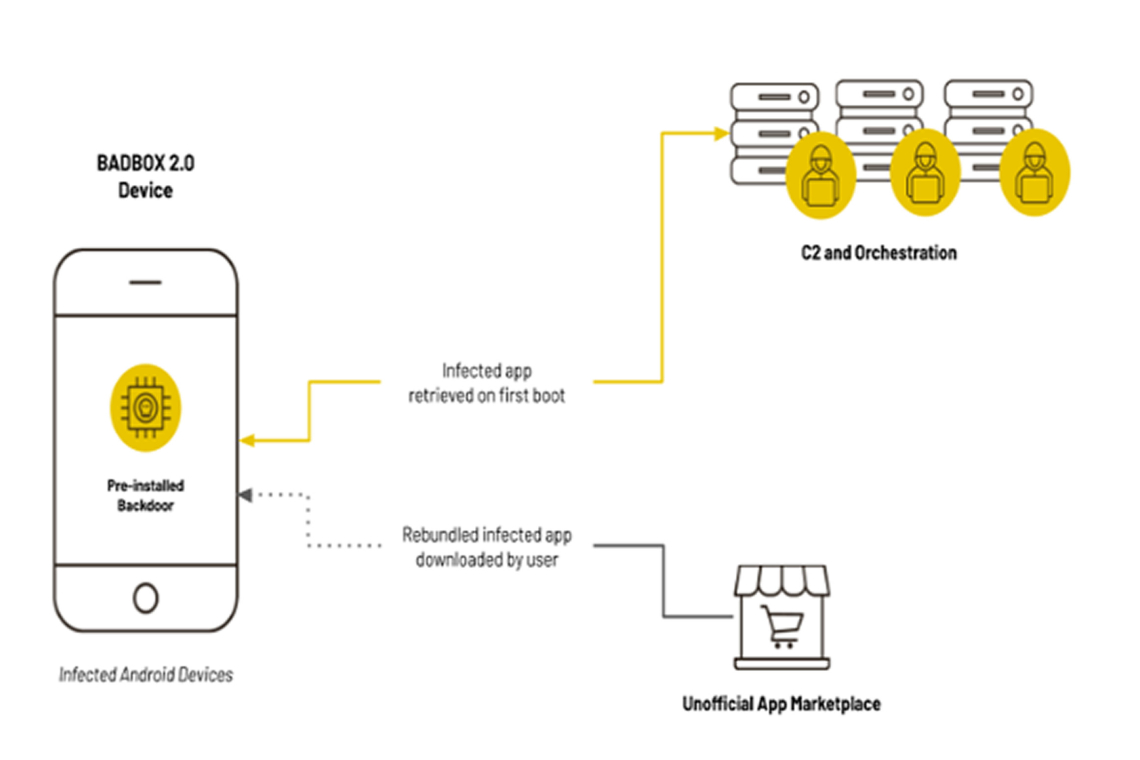
The BADBOX 2.0 botnet has been labeled the largest-ever network of infected connected TV (CTV) devices, significantly expanding the original BADBOX operation. Like its predecessor, BADBOX 2.0 spreads through backdoors embedded in low-cost consumer devices, allowing cybercriminals to remotely load fraud modules.
Once infected, these devices communicate with command-and-control (C2) servers operated by distinct but cooperating hacker groups. Attackers distribute malware through supply chain compromises and third-party marketplaces, embedding hidden loader functionality in seemingly legitimate applications.
How BADBOX 2.0 Operates
Infected devices become part of a larger botnet used for:
- Hidden ad fraud – Running fake ads in the background to generate revenue.
- Click fraud – Navigating users to low-quality websites and clicking on ads for profit.
- Residential proxy abuse – Routing malicious traffic through infected devices.
- Cybercriminal activities – Enabling account takeovers (ATO), fake account creation, malware distribution, and DDoS attacks.
Scale of the Attack
An estimated one million devices have been compromised, including cheap Android tablets, connected TV boxes, digital projectors, and car infotainment systems. All affected devices are manufactured in China and distributed globally, with the highest infection rates in Brazil (37.6%), the U.S. (18.2%), Mexico (6.3%), and Argentina (5.3%).
Ongoing Efforts to Disrupt BADBOX 2.0
Authorities have taken steps to disrupt the botnet. An undisclosed number of BADBOX 2.0 domains were sinkholed, cutting off infected devices from their control servers. Additionally, Google removed 24 malicious apps from the Play Store. Previously, in December 2024, German authorities also took down part of BADBOX’s infrastructure.
Google clarified that affected devices are Android Open Source Project (AOSP) devices, not Play Protect-certified Android or Android TV OS devices. Play Protect-certified devices undergo strict security testing, making them less vulnerable to such malware.
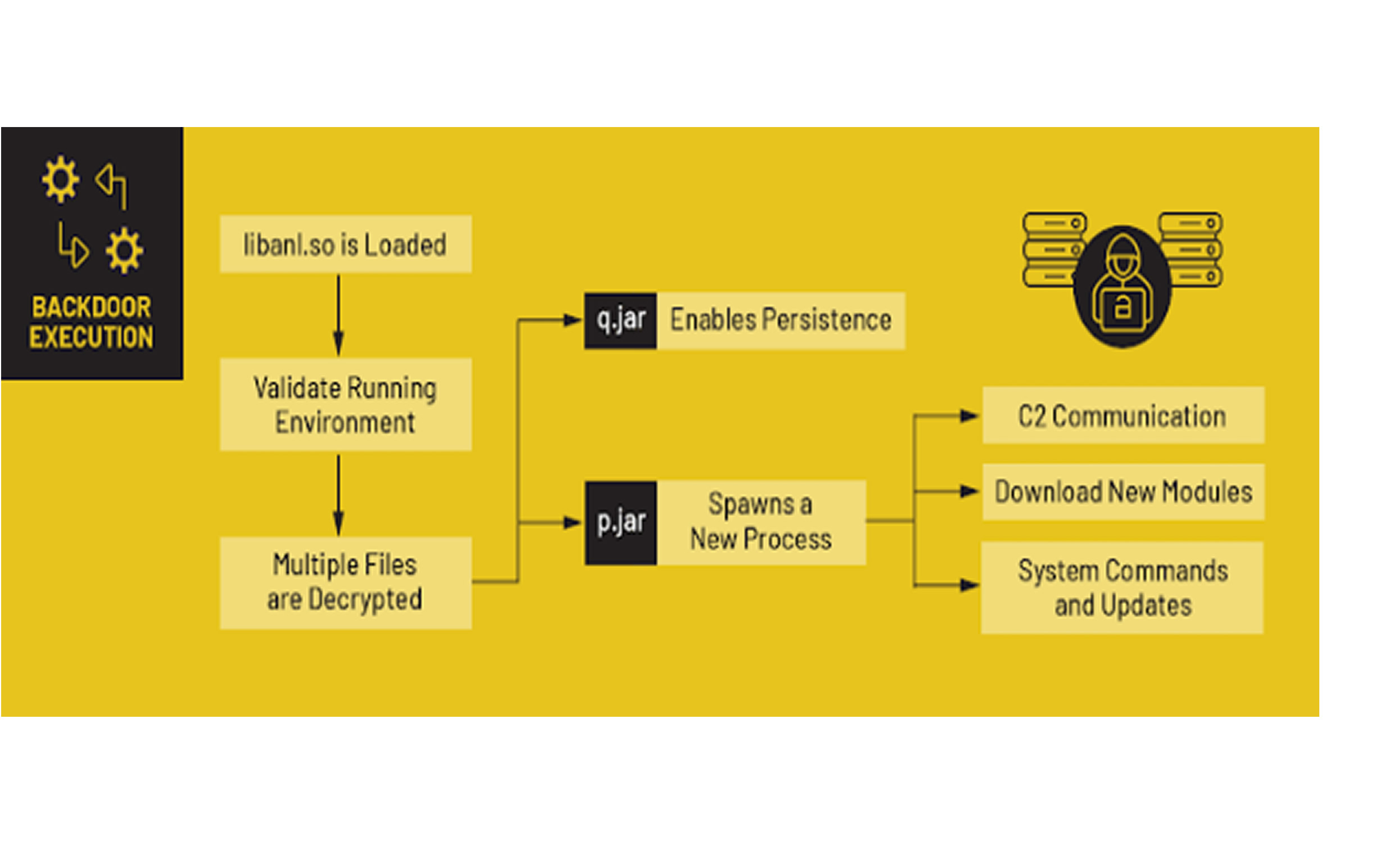
The core backdoor, known as BB2DOOR, originates from the Android malware Triada and spreads through:
- Pre-installed components on infected devices.
- Downloads from remote servers when devices boot for the first time.
- Over 200 trojanized versions of popular apps from third-party app stores.
The MoYu Group appears to be the primary operator behind BB2DOOR, using the infected devices for residential proxy services. Other cybercriminal groups oversee different aspects of the operation:
- SalesTracker Group – Monitors infected devices and links to the original BADBOX operation.
- Lemon Group – Uses BADBOX for ad fraud and residential proxy services across HTML5 (H5) gaming sites.
- LongTV – A Malaysian company running an "evil twin" ad fraud scheme through its apps.
Investigators found that these groups share infrastructure, such as C2 servers and business connections, revealing a deeply intertwined cybercrime network.
A More Sophisticated Malware Evolution
BADBOX 2.0 introduces new methods of infection, including modifying legitimate Android libraries to achieve persistence. Evidence suggests overlaps between BB2DOOR and Vo1d, another malware specifically targeting off-brand Android TV boxes.
A Growing Threat to Smart Devices
BADBOX 2.0 highlights how cybercriminals exploit security loopholes in cheap, unregulated devices. With backdoors in place, infected devices can be commanded to carry out any cyber attack an attacker develops.
This discovery follows Google’s removal of over 180 Android apps (56 million downloads) involved in the "Vapor" ad fraud scheme and a recent campaign tricking users into downloading Android banking malware (Octo).
As cybercriminals continue to evolve their tactics, security experts stress the urgent need for stronger supply chain security, user awareness, and stricter enforcement against fraudulent apps in the global digital ecosystem.