Google Forms, known for its seamless data collection, has unexpectedly become a launchpad for a fast-moving crypto-phishing campaign.
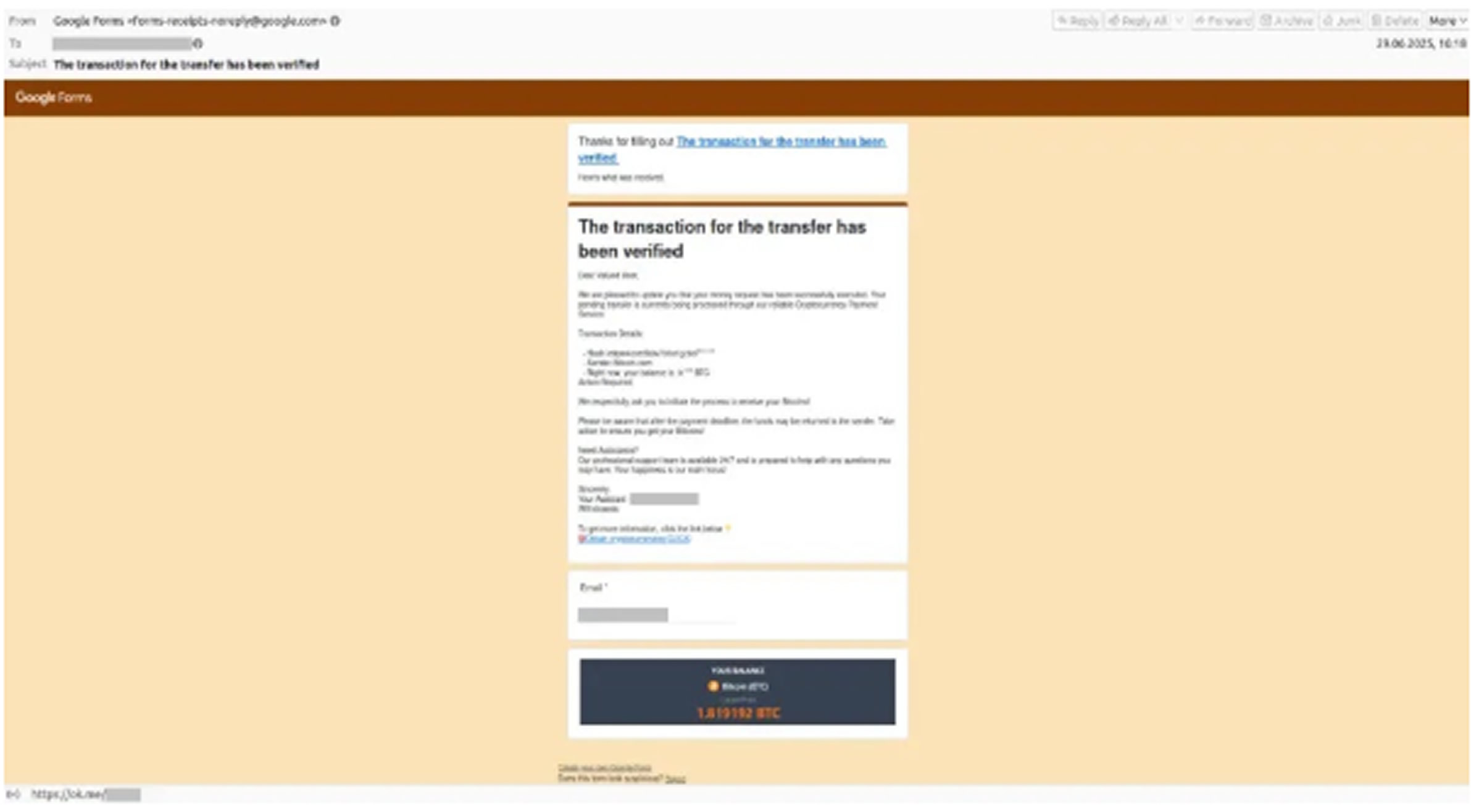
First observed in late 2024, this scheme saw a major surge in the second quarter of 2025. It typically starts with an unsolicited email that includes a convincing forms.gle link, which slips past most spam filters.
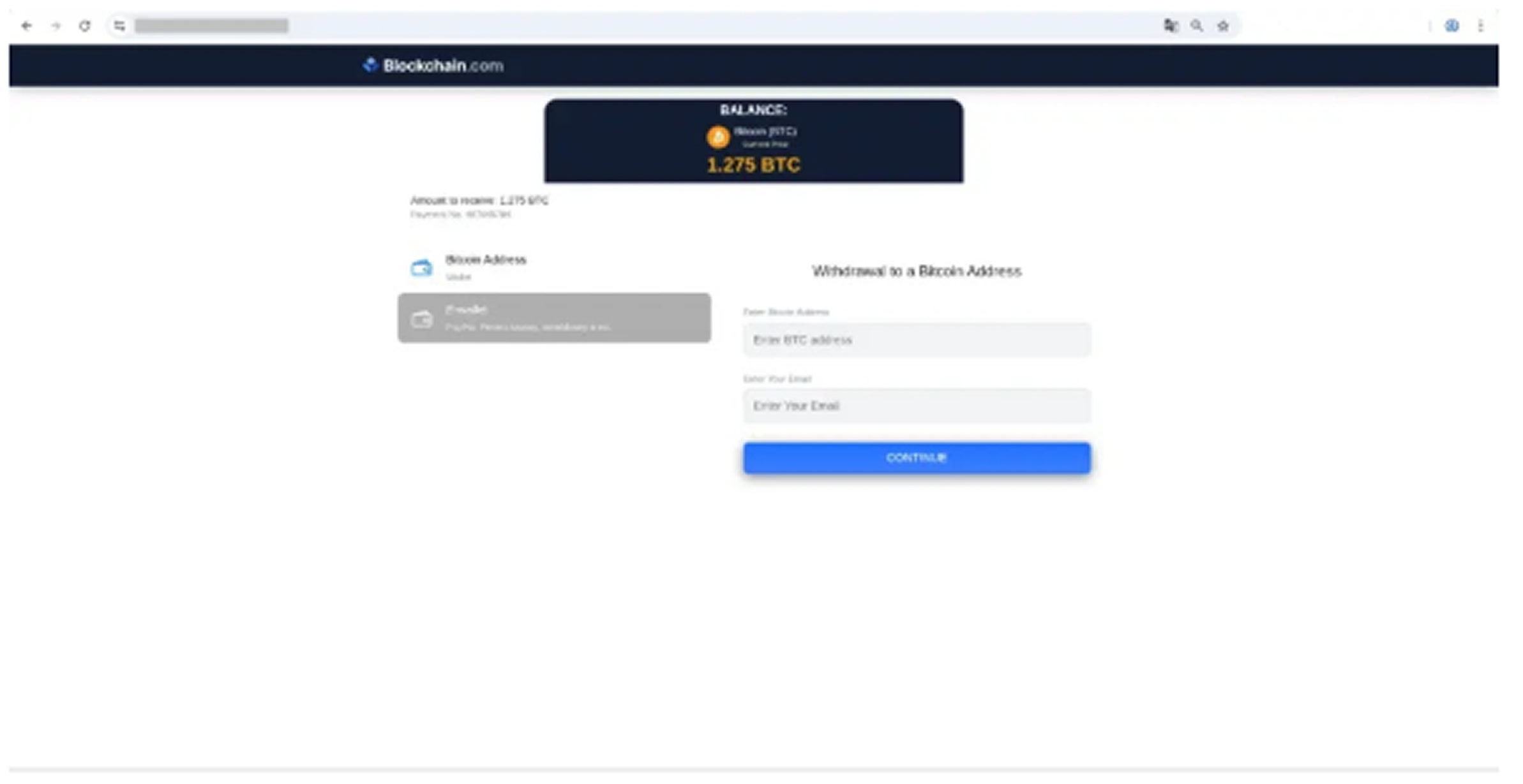
Once accessed, the form mimics a trusted cryptocurrency exchange and congratulates the recipient with news of a “pending 1.275 BTC payout.” One click redirects users to a fake withdrawal site that prompts them to verify their wallet and send a small network fee.
Victims’ credentials are immediately transferred to a hidden command-and-control server using Cloudflare Workers, and any payments are redirected to mixer wallets, erasing the digital trail.
A key factor in the scheme’s success is its use of Google’s notification system. Since messages are sent via Google’s SMTP infrastructure, reputation filters mark them as safe, helping the attackers land directly in victims’ inboxes.
Kaspersky researchers noticed a sharp rise in this tactic in July 2025, reporting a 63 percent increase in phishing attempts that use Google Forms. The campaign has been classified as one of the year’s most effective low-tech social engineering threats.
The infection method centers on credential theft through embedded WebHooks. These are tied to an Apps Script that extracts submitted data instantly, without requiring full form completion.
It also triggers a one-time redirect to a spoof site at hxxps://claim-btc-id[.]online, built with a polished React interface and a Python Flask backend that reroutes data to the attacker’s server.
Mitigation strategies rely on multiple layers of protection. These include quarantining Google Forms emails that haven’t been pre-approved, and installing browser extensions to block outgoing requests to unfamiliar domains.
Finally, training users to recognize scams remains essential. They must remember that legitimate cryptocurrency giveaways are never distributed via form submissions.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



