Cybersecurity researchers have uncovered an Android banking malware campaign that uses a trojan called Anatsa to target users in North America. The malware was hidden inside malicious apps that were published on the official Google Play Store.
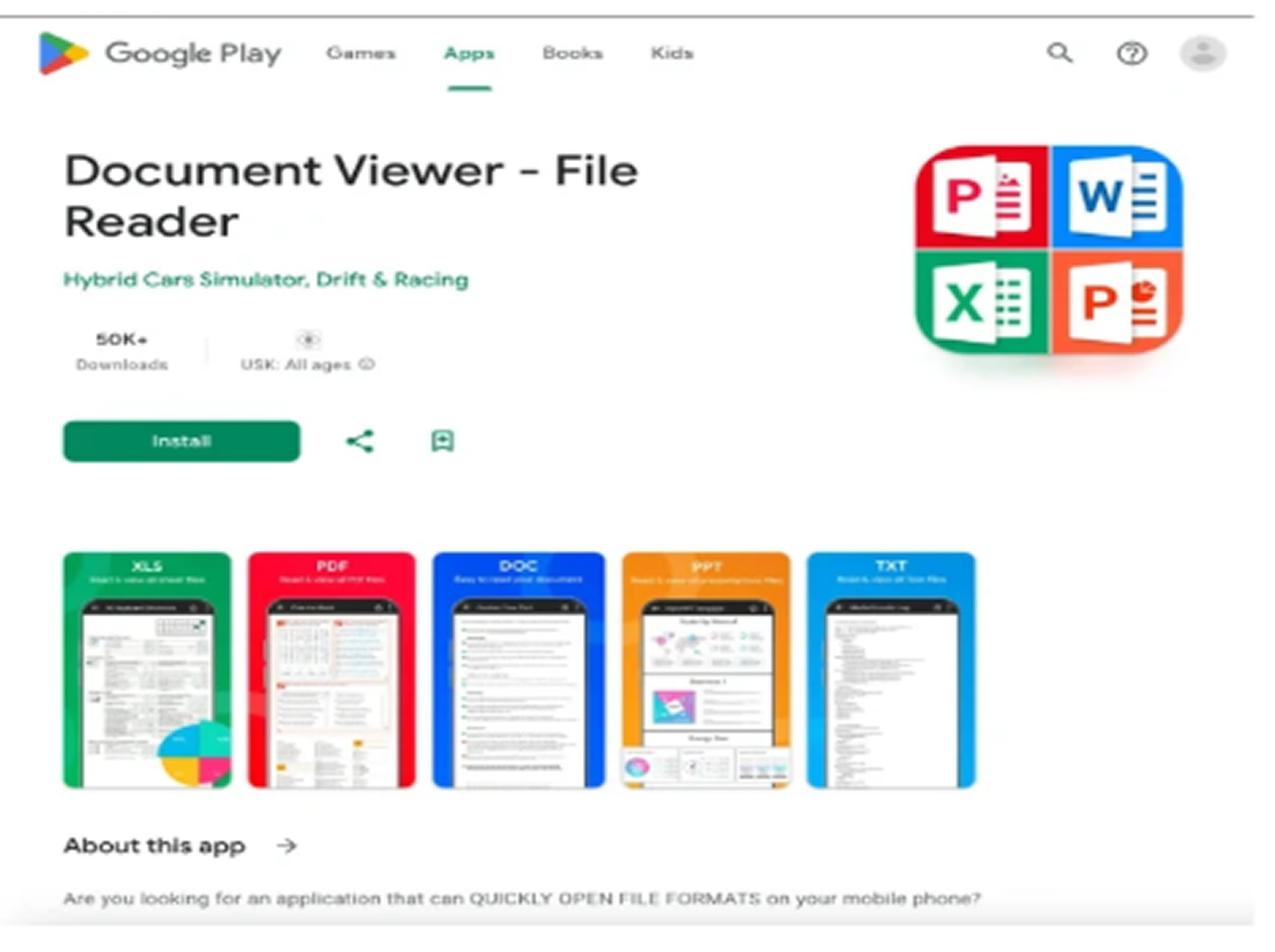
Disguised as a "PDF Update" for a document viewer app, the malware presents a fake screen when users try to open their banking apps. This screen claims the service is temporarily unavailable due to scheduled maintenance.
According to mobile security company ThreatFabric, this is the third known campaign involving Anatsa targeting banking customers in the United States and Canada. As with previous incidents, the malware was distributed through the Google Play Store.
Anatsa, also known as TeaBot or Toddler, has been active since at least 2020. It is usually delivered through dropper apps. In early 2024, the malware targeted users in Slovakia, Slovenia, and Czechia by first publishing harmless-looking apps like PDF readers and phone cleaners. Malicious code was then added through an update about a week after the apps were released.
Like other Android banking trojans, Anatsa can steal login information through overlay attacks and keylogging. It can also take full control of a device to carry out fraudulent transactions without the user’s knowledge.
ThreatFabric stated that these campaigns usually follow the same method. The attackers create a developer profile, release a functional app, and build up a user base. After the app reaches thousands or tens of thousands of downloads, it receives an update that secretly includes malware. This update installs Anatsa as a separate app on the victim's device.
Once installed, the malware connects to an external server to receive a list of banks and financial apps to target. It then collects credentials, records keystrokes, and may initiate automated transactions. A key feature of Anatsa is its ability to remain undetected by staying inactive for periods of time between attacks.
The most recent app targeting North American users was called Document Viewer. Its package name was "com.stellarastra.maintainer.astracontrol_managerreadercleaner," and it was published by a developer named "Hybrid Cars Simulator, Drift & Racing." Both the app and the developer’s profile have been removed from the Play Store.
Sensor Tower data shows that the app was first uploaded on May 7, 2025. By June 29, it had reached the fourth position in the "Top Free - Tools" category. It is estimated to have been downloaded about 90,000 times.
ThreatFabric explained that this dropper followed the usual Anatsa method. It launched as a legitimate app and was converted into a malicious one about six weeks later. The malware was active between June 24 and June 30. This version of Anatsa also targeted more U.S. banking apps than previous versions, showing a growing interest in exploiting financial institutions in the region.
The malware includes a deceptive feature that displays a fake maintenance alert when users open their banking apps. This trick helps hide the malware’s activity and prevents users from reaching out to their bank, which delays the discovery of fraudulent transactions.
ThreatFabric concluded that this operation expanded its scope while using well-established tactics against financial targets. They encouraged banking institutions to review the threat details and evaluate any potential risks to their systems or customers.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



